- Cisco Community
- Technology and Support
- Security
- VPN
- Two VPN SiteTOSite with different Encryption Algo
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 01:48 AM - edited 03-12-2019 05:24 AM
Hi Team,
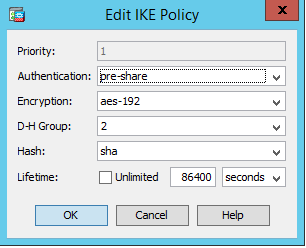
I Have a site to site connect to another site of our office with encryption algorithm IKE Policy :
- Authentication : pre-share
- encryption : aes-192
- DH : 2
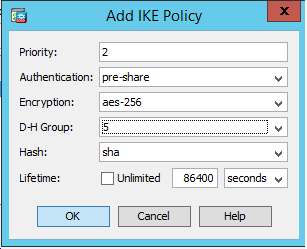
I have to add a new site to site connection to another site but this time, the customer from the other side have sent to me the encryption algorithm IKE Policy :
- Authentication : pre-share
- encryption : aes-256
- DH : 5
So, I created the new connection and suddenly the first connection is down. After check, I found that the DH of the first connection has cchanged to DH : 5.
Is there any solution please.
regards,
Solved! Go to Solution.
- Labels:
-
Other VPN Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 01:19 AM
Thank you for your feedback Sir.
I have resolved the problem by adding the two IKEv1 Policy, the CLI show command is as below :
crypto ikev1 policy 1
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 2
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
The two VPN Connections are up now by adding the two IKEv1 policy in the same field :
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 02:12 AM
Please upload the configuration on the device that is already working and an example what you added/changed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 02:21 AM
Thank you for responding ,
In fact, I work with an ASA5515-x.
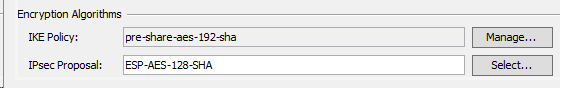
The existing VPN STS is as below :
The IKE Policy credentiels are :
The second VPN STS that I have to add is as below :
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-25-2018 09:18 AM
Your first screenshot only shows there to be 1 IKE policy, can you confirm that both IKEv1 policies are assigned?
What is the output from the CLI? There should be at least 2 IKEv1 policies, one with Group 2 and the other with Group 5.
crypto ikev1 policy 5
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 01:19 AM
Thank you for your feedback Sir.
I have resolved the problem by adding the two IKEv1 Policy, the CLI show command is as below :
crypto ikev1 policy 1
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 2
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
The two VPN Connections are up now by adding the two IKEv1 policy in the same field :
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2018 02:44 AM
Glad I could assist in helping you resolve this!
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide