- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Validation Error after successful DUO authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Validation Error after successful DUO authentication
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2024 09:06 AM
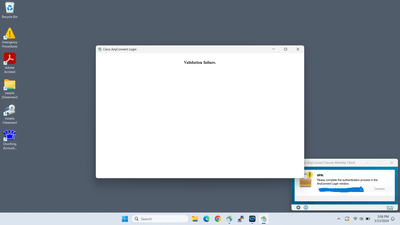
We have two FTD 1140n 's(version 7.2.5) in an HA being managed by a FMCv (verion 7.2.5.1) We are using AnyConnect version 4.10.08025 for VPN clients. We setup DUO SSO and it is working fine with one of the two vpn connection profiles we use. We get a "Validation Error"when we use the other connection profile. Here is a screenshot of the error.
As you can see this an "AnyConnect" window. This appears after a successful DUO MFA attempt. The connection profiles are identical except for the VPN IP pool being used. If I try using the same connection profile with DUO MFA taken out and a local database being used for AAA it works fine. Does "Validation Error" mean Certificate Validation error?
- Labels:
-
AnyConnect
-
Duo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2024 10:34 PM
What are the configurations set on the Duo side?
For the new connection profile, Did you create a separate Duo Application or are you using the same SSO for both the connection profile?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-20-2024 05:46 AM
The same SSO.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2024 10:59 AM
Im having this issue as well (version 7.2.4). Trying to get DUO SSO working for both PC and Mobile users. I created a separate connection profile for mobile, due to the pasting URI issue between browsers, and have run into this error on the secondary connection profile. Ill test out a secondary DUO application to see if that corrects the behavior.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-26-2024 09:15 PM
Generally speaking, each connection profile requires a separate Duo application:
https://duo.com/docs/sso-ciscofirepower#update-the-cisco-firepower-application-in-duo
I have not set it up personally, but others have reported success with multiple profiles using this work around:
https://community.cisco.com/t5/vpn/one-saml-for-2-anyconnect-profiles/td-p/4765122
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2024 08:59 AM
@Marvin RhoadsThank you for the update. We can implement another DUO SSO application for the other connection profile. I am curious as to why this is needed though. Seeing as the users are going through the same FTD and are found in the same User database. Wouldnt the FTD be sending the same URL, or whatever is needed, to DUO for Authentication? Or are the different connection profiles sending separate connection strings that then tell DUO that "these arent the droids your looking for" and tells the user to kick rocks? Also, why would DUO reject the second connection profile if it has all the needed information, i.e. Cert, inbound URL, outbound URL, etc.?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-28-2024 09:13 AM - edited 05-28-2024 09:17 AM
The Duo SSO application talks back to the firewall using a URL that includes the tunnel-group (AKA connection profile) name. That's why a different connection profile requires a different application instance.
In more detail, after Duo has worked with the primary authentication source and further authenticated the user's chosen Duo MFA method, Duo as a SAML Identity Provider is sending back an HTTP POST to the firewall as a SAML Service Provider at its Assertion Consumer Service URL. That ACS URL has the tgname (tunnel-group name) embedded within it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide