- Cisco Community
- Webex
- Webex Community
- Webex Devices
- Webex 224-bit TLS Enforcement for H.323
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Webex 224-bit TLS Enforcement for H.323
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-11-2023 08:32 AM
Cisco has sent out the below notice to our customers.
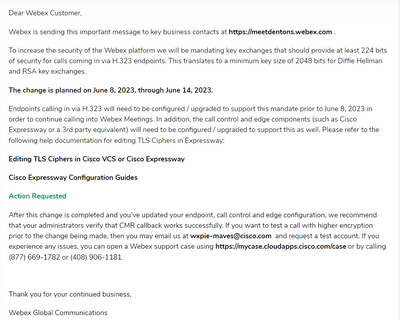
We have Expressways-C ver X8.10.4 for one of our customer.
Cisco WebEx Board 55 RoomOS 11.3.1.17 09fdf7c0b94
We do have H.323 enabled on our Expressways and the TLC already set to v1.2 with ciphers. Do we need to change anything on our WebEx device above ? Next software release/update for Board is pending in April 2023 Release RoomOS 11.4.0.31 0022c64ca1e
Would this take care of the 2048 encryption/TLS or do we still need to change anything ? If yes, what needs changing ? Any help would be appreciated.
Thanks,
Priyank
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2023 05:19 AM
Since Expressway release v12.6 , expressway supports 2048 bit encryption for H.323 calls. Expressway Will offer both 1024 bit and 2048 bit encryption for video endpoints.
You can check with the following command on the expressway CLI.
xConfiguration Interworking Encryption KeySize2048
is the command is on: expressway will allow 2048 key lenght
is the command is off: only 1024 keys will be offered.
So in order to have 2048 key lenght the command should be on ON.
You can follow more information on bellow document (page 13, Configuration of DH Key Length for H.323-SIP Interworking section)
https://www.cisco.com/c/dam/en/us/td/docs/voice_ip_comm/expressway/release_note/Cisco-Expressway-Release-Note-X12-6-4.pdf
Also if you want to check what devices do you have register using h.323 you can go to the following path on your expressway server
Status >> Registrations >> By device to check the devices using H323
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-02-2023 09:50 AM
Thank you Muhammad, I have a follow up question.
We use WebEx and we also have a number of customers who use it. We are all utilizing a mix of H.323 endpoints and WebEx browser based clients. I have examined two of our endpoints (Cisco SX20, Cisco Room Kit Mini) and located the Diffie-Hellman key length settings. I see both have support for 2048-bit keys.
However, if you review the H.235.6 standard information below for the two supported key lengths, there is an implication about the supported media encryption algorithms for the specified Diffie-Hellman key lengths.
https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-H.235.6-201401-I!!PDF-E&type=items
"DH1024": The OID references a standardized, fixed 1024-bit DH group. This DH group
shall be used to generate a master key for distribution of session key(s) for Triple-DES
("Z") encryption algorithms.
"DH2048": This DH group is offered as an option for version 3 end points having security
requirements that exceed the security of a 1536-bit DH group. The OID references a fixed
2048-bit DH group. This DH group shall be used to generate a master key for distribution
of session key(s) for AES-192 or AES-256 ("Z4", "Z5") encryption algorithms.
What I would like to know is, will WebEx also be requiring 256-bit AES media encryption when connecting from legacy H.323 equipment after June 8th, or can we continue using 128-bit AES media encryption with a 2048-bit Diffie Hellman key?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide