- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Cisco Service Provider Wi-Fi - PPPoE Feature Support
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-13-2012 09:27 PM - edited 11-18-2020 03:00 AM
Introduction
Cisco has come up with bunch of features those were developed to help Service Provider in deploying large network in public area and named it as SP Wi-fi but it does not mean that it is limited to Service Providers. Anybody can use SP Wi-Fi features, it all depends on company’s network and requirements.
In this document we will see details about SP Wi-Fi PPPoE Features support.
Brief description of PPP
We can divide it into two parts – PPP and PPPoE.
- PPP – Point to Point Protocol – It is an encapsulation protocol that is used over serial point-to-point links. The features of PPP are - Network address assignment, link configuration management, error detection, multi protocol.
- PPPoE – Point to Point Protocol over Ethernet – is a same protocol but can be used in Ethernet network. In other word, PPPoE creates point to point connection by establishing tunnel between two devices which are connected through Ethernet. Rest of the things remains same as PPP, means PPPoE uses standard methods of encryption, authentication, and compression specified by PPP.
In brief, we can say that PPPoE expands PPP functionality.
What kind of role is being played by Cisco wireless devices here?
There are two devices in PPPoE, one is PPPoE client and second is PPPoE server. Currently in most deployments, PPPoE clients are either Cisco Router or a modem that can act as a PPPoE client and Cisco Access Point are connected behind that. To save users money, Cisco wireless came up with a solution that now Cisco Access Point can act as a PPPoE client. That's correct, a Cisco AP can act as a PPPoE client hence users do not need to invest their money on separate router or a modem for PPPoE.
Let’s discuss how PPPoE works on Cisco Access Point –
Cisco Access Point uses Dialer interface to establish PPPoE connection. Cisco PPPoE Access Point discovers PPPoE server using PADI/PADO/PADR/PADS messages.
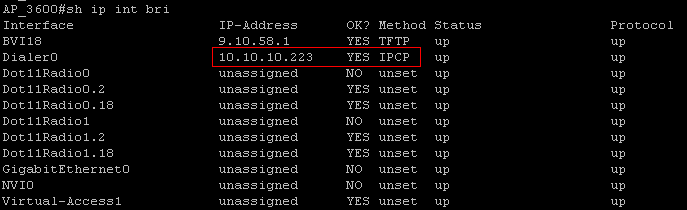
After this, Cisco Access Point sets up PPP connection with PPPoE server. In IPCP phase of PPP connection, Cisco PPPoE AP receives an IP Address from PPPoE server. This is the public IP address assigned by ISP to the Cisco AP and this IP address is assigned to dialer interface. Once the PPPoE session is establish then Cisco Access Point try to join WLC.
The default route is added automatically hence all the traffic will go over Dialer interface with PPPoE encapsulation. The PPPoE field in the frame will be removed by PPPoE server and the packet will be sent further as per the destination.
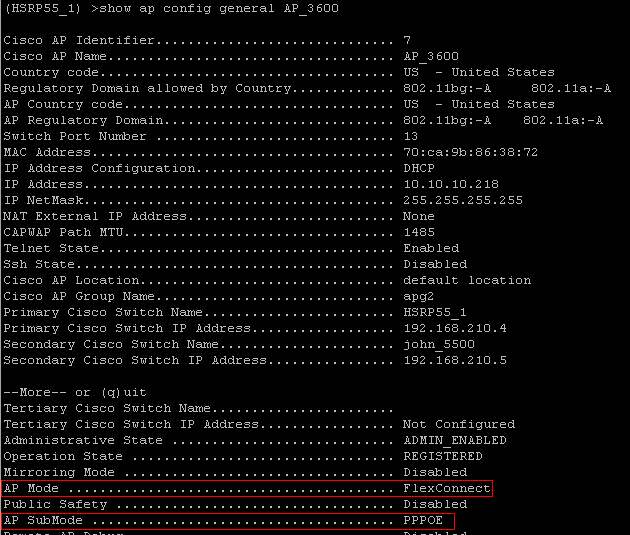
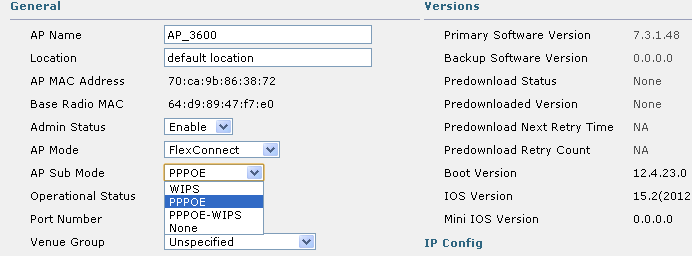
Note - Only Flexconnect Access Point supports PPPoE. PPPoE can be configured as submode of Flexconnect mode.
Before we jump of the configuration part let’s discuss different processes of PPPoE in a simple way –
PPPoE Peer Discovery Process
- Initiation - Cisco Access Point initiates PPPoE server discovery that is called PADI (PPPoE Active Discovery-Initiation). It will be a broadcast.
- Offer - Then the server responds with offer and it’s called PADO (PPPoE Active Discovery Offer). Offer contains server name and host unique id.
- Request - Upon receipt of the PADO packet, the client responds by sending a PPPoE Active Discovery Request (PADR) packet to the server.
- Confirmation - Upon receipt of the PADR packet, the server responds by generating a unique ID for the PPP session and sends it in a PPPoE Active Discovery Session (PADS) confirmation packet to the client.
LCP (Link Control Protocol) Process
PPPoE uses LCP to agree upon encapsulation format the encapsulation format options, handle varying limits on sizes of packets (MTU), detect a looped-back link and other common misconfiguration errors, and terminate the link. Other optional facilities provided are authentication of the identity of its peer on the link, and determination when a link is functioning properly and when it is failing.
In other word, we can say that LCP is used to establish, configure and test data link connection for PPP link.
Cisco AP supports following functionality in LCP Phase
- Maximum-Receive-Unit – used to negotiate MTU size and it is configurable on AP.
- Authentication-Protocol – negotiation auth protocol – PAP or CHAP. Configurable on AP.
- Magic-Number – This option is used to check link loop-back of the packets. This is NOT configurable on Cisco Access Point but can be negotiated if peer wants.
- Address-and-Control-Field-Compression – Cisco AP do not support it and AP will reject it if peer wants it.
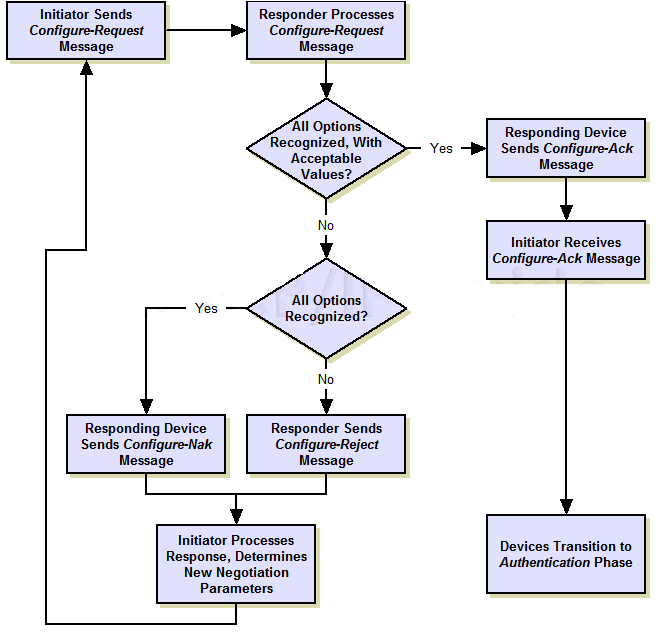
5. LCP config Request – Peers negotiate the value of the above supported features with each others.
6. LCP config ACK – Peers acknowledge the value of each other.
- LCP config NAK – This msg will be sent when the value is recognized but not acceptable.
- LCP config Reject – Peers reject the invalid values or unsupported feature.
7. Authentication – Authentication Protocol will be negotiated. PPPoE server sends “challenge” and the PPPoE client replies with credentials. Server then acknowledges it.
When relationship gets established IP address assignment process starts –
8. IPCP config Req – This is used to negotiate IP address with peers.
9. IPCP config ACK – This is used to acknowledge the IP address of peers.
- IPCP config NAK – This msg will be sent when the value is recognized but not acceptable.
- IPCP config Reject – Peers reject the invalid values or unsupported feature.
IPCP Process
Attributes is negotiated in IPCP process –
• IP Address - IP address is negotiated with peer. AP does not have any preferred address configuration for IPCP negotiation. This is configurable under “Dialer interface”.
Following Options are supported or negotiated in IPCP process –
• DNS configuration – NOT configurable on Access Point.
• WINS configuration – NOT configurable on Access Point.
• Static route configuration – Dynamic routing protocol are NOT allowed to work on Dialer Interface. By default a Static route will be added with Dialer interface as the outgoing interface. If the peer want to add any static route that will be added in the Access Point.
Negotiation of LCP and IPCP Phase
Configuration of PPPoE
Before we jump on the configuration part of PPPoE on Cisco Access Points, let’s discuss some key Points –
• PPPoE supported only on Flexconnect Access Point.
• There is PPPoE sub-mode under Flexconnect mode and that should be configured from Cisco Wireless Controller.
• Currently there is NO support for PPPoE related configuration from Cisco controller hence the configuration of PPPoE on Access Point has to be done directly on Access Point via console.
• Currently Cisco Access Point supports PAP and CHAP authentication methods. EAP, MS-CHAP, MS-CHAPv2 as authentication methods for PPP are NOT supported but in future the support for these methods will be added.
• MTU, Magic Number, Quality-Protocol, Authentication-Protocol and Address-and-Control-Field-Compression are supported features with limitation which we have discussed earlier in this doc.
• Maximum supported MTU – 1492 bytes.
• Only “dialer 0” interface will be supported for the PPPoE configuration.
• Vlan Tagging feature is NOT supported on Cisco PPPoE Access Point.
• Local-Auth feature is NOT supported on Cisco PPPoE Access Point.
• Vlan Mapping feature of Flex Access Point is NOT supported if AP is PPPoE.
• Vlan based central switching is not supported on PPPoE AP.
• In Standalone mode – already associated clients will be served as it is but new clients are not allowed. So when session time gets expired then re-association will not happen.
• WGB (WGB connects as a client to PPPoE AP) with multiple vlan supports is NOT supported.
• Multicast – local-switching wlan on PPPoE AP and non-PPPoE AP (NAT/PAT enabled) will not be supported because NAT/PAT does not support multicast. In case of non-PPPoE (NAT/PAT disabled) Multicast-Unicast is supported but it has scaling issue hence No claim for the support.
Multicast with central-switching wlan will work but No official support for that as well.
• Mobility – with central-switching wlan L2 and L3 both roaming are supported as it is. Local-switching wlan – L2 roaming between APs is supported. L3 Roaming is not supported with local-switching.
• Wireless clients with PPPoE application or it required to get IP address from PPPoE server are NOT supported.
• Client with static IP Address is Not supported on PPPoE AP.
As we discussed, PPPoE configuration has to done in-house before deploying. Any out of box Cisco Access Point will be joining in Local mode then change the mode of the access point to Flexconnect mode with sub-mode as PPPoE. If the Cisco Access Point is already in Flexconnect then just need to change the sub-mode as PPPoE. Cisco Access Point then reboot and come up and ready to be configured.
Commands
Commands | Remarks | Mandatory |
interface dialer 0 | Only "dialer 0" is supported | Yes |
ip address <negotiated|manual> | If negotiated is configure then Access Point will get IP address from PPPoE server in NCP phase. "ip address dhcp" is not support. | Yes |
encasulation PPP | It enables PPP encapsulation on dialer interface. | Yes |
mtu <size> | This will be negotiated with PPPoE server. Max is 1492 bytes supported. | No |
dialer pool <pool number> | Yes | |
ppp authentication <pap | chap> {callback | callin | callout | one-time | optional} default | Only "pap and chap" are supported for now. | No |
ppp pap sent-username <username> password <password> | No | |
ppp chap hostname <username> | No | |
ppp chap password <password> | No | |
ppp pap refuse [callin] | No | |
ppp pap wait | No | |
ppp chap refuse [callin] | No | |
ppp chap wait | No | |
ppp ipcp route default | ||
interface <ethernet interface type > <number> | e.g interface gig0 | Yes |
pppoe enable | It enables PPPoE on ethernet interface. | |
pppoe-client dial-pool-number <pool number> | Pool number should be same as configured on PPPoE server. There is an option with the Command "dial-on-demand" but it's NOT supported. | Yes |
pppoe-client dial-pool-number <pool-number> [restart <restart-timeout>] | When PPPoE receives PADT to terminate connection, this can be restarted after specified time in this option | No |
Configuration Example
Configuration on PPPoE server (Cisco router)
1. Creating virtual-template and Chap authentication
PPPoE_server(config)#bba-group pppoe 1
PPPoE_server(config-bba-group)#virtual-template 1
PPPoE_server(config-bba-group)#exit
PPPoE_server(config)#aaa new-model
PPPoE_server(config)# aaa authentication ppp PPPoE local
PPPoE_server(config)# username johnny password johnny
2. To provide the IP address to Access Point in NCP Phase we also need to configure DHCP pool on the same PPPoE server-
PPPoE_server(config)# ip dhcp excluded-address 10.10.10.1 10.10.10.10
PPPoE_server(config)# ip dhcp pool PPPoE_AP_Pool
PPPoE_server(dhcp-config)# network 10.10.10.0 255.255.255.0
PPPoE_server(dhcp-config)# default-router 10.10.10.1
3. Configuration of Virtual-Template interface –
PPPoE_server(config)#interface Virtual-Template 1
PPPoE_server(config-if)#ip address 10.10.10.1 255.255.255.0
PPPoE_server(config-if)#peer default ip address dhcp-pool PPPoE_AP_Pool
PPPoE_server(config-if)#ppp authentication chap
Configuration on Cisco Access Point (PPPoE Client)
AP_3600(config)#interface dialer 0
AP_3600(config-if)#ip address negotiated
AP_3600(config-if)#encapsulation ppp
AP_3600(config-if)#dialer pool 1
AP_3600(config-if)#ppp authentication chap callin
AP_3600(config-if)#ppp chap hostname johnny
AP_3600(config-if)#ppp chap password Johnny
AP_3600(config)#interface GigabitEthernet 0
AP_3600(config-if)# pppoe-client dial-pool-number 1
NOTE – when PPPoE is enabled on Access Point a default route will be created with dialer 0 interface as outgoing interface.
ip route 0.0.0.0 0.0.0.0 Dialer0
Verification with show commands
• On Cisco Wireless controller
Show ap config general <ap_name>
• On Cisco Access Point
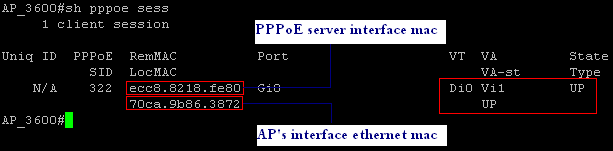
show pppoe session { all | interface | packets } |cr
show pppoe summary
show ip interface brief
Cisco Access Point GUI page on Cisco wireless controller
Debugs on Cisco Access Point
- debug ppp negotiation
- debug pppoe events
- debug pppoe packets
Sample example of “ppp negotiation and pppoe events” debugs when Cisco Access Point establish the PPPoE connection –
*May 4 10:12:05.019: Sending PADI: Interface = GigabitEthernet0
*May 4 10:12:05.019: PPPoE 0: I PADO R:ecc8.8218.fe80 L:70ca.9b86.3872 Gi0
AP_3600#
*May 4 10:12:05.159: %LINK-6-UPDOWN: Interface Dialer0, changed state to up
*May 4 10:12:07.067: PPPOE: we've got our pado and the pado timer went off
*May 4 10:12:07.067: OUT PADR from PPPoE Session
*May 4 10:12:07.079: PPPoE 323: I PADS R:ecc8.8218.fe80 L:70ca.9b86.3872 Gi0
*May 4 10:12:07.079: IN PADS from PPPoE Session
*May 4 10:12:07.079: %DIALER-6-BIND: Interface Vi1 bound to profile Di0
*May 4 10:12:07.079: PPPoE: Virtual Access interface obtained.
*May 4 10:12:07.079: PPPoE : encap string prepared
*May 4 10:12:07.079: [0]PPPoE 323: data path set to PPPoE Client
*May 4 10:12:07.083: %LINK-6-UPDOWN: Interface Virtual-Access1, changed state to up
*May 4 10:12:07.083: Vi1 PPP: Sending cstate UP notification
*May 4 10:12:07.083: Vi1 PPP: Processing CstateUp message
*May 4 10:12:07.083: PPP: Alloc Context [86C262C]
*May 4 10:12:07.083: ppp4 PPP: Phase is ESTABLISHING
*May 4 10:12:07.083: Vi1 PPP: Using dialer call direction
*May 4 10:12:07.083: Vi1 PPP: Treating connection as a callout
*May 4 10:12:07.083: Vi1 PPP: Session handle[33000004] Session id[4]
*May 4 10:12:07.083: Vi1 LCP: Event[OPEN] State[Initial to Starting]
*May 4 10:12:07.083: Vi1 PPP: No remote authentication for call-out
*May 4 10:12:07.083: Vi1 LCP: O CONFREQ [Starting] id 1 len 10
*May 4 10:12:07.083: Vi1 LCP: MagicNumber 0xDD51172D (0x0506DD51172D)
*May 4 10:12:07.083: Vi1 LCP: Event[UP] State[Starting to REQsent]
*May 4 10:12:07.091: Vi1 LCP: I CONFREQ [REQsent] id 1 len 19
*May 4 10:12:07.091: Vi1 LCP: MRU 1492 (0x010405D4)
*May 4 10:12:07.091: Vi1 LCP: AuthProto CHAP (0x0305C22305)
*May 4 10:12:07.091: Vi1 LCP: MagicNumber 0x53D691A5 (0x050653D691A5)
*May 4 10:12:07.091: Vi1 LCP: O CONFNAK [REQsent] id 1 len 8
*May 4 10:12:07.091: Vi1 LCP: MRU 1500 (0x010405DC)
*May 4 10:12:07.091: Vi1 LCP: Event[Receive ConfReq-] State[REQsent to REQsent]
*May 4 10:12:07.091: Vi1 LCP: I CONFACK [REQsent] id 1 len 10
*May 4 10:12:07.091: Vi1 LCP: MagicNumber 0xDD51172D (0x0506DD51172D)
*May 4 10:12:07.091: Vi1 LCP: Event[Receive ConfAck] State[REQsent to ACKrcvd]
*May 4 10:12:07.095: Vi1 LCP: I CONFREQ [ACKrcvd] id 2 len 19
*May 4 10:12:07.095: Vi1 LCP: MRU 1500 (0x010405DC)
*May 4 10:12:07.095: Vi1 LCP: AuthProto CHAP (0x0305C22305)
*May 4 10:12:07.095: Vi1 LCP: MagicNumber 0x53D691A5 (0x050653D691A5)
*May 4 10:12:07.095: Vi1 LCP: O CONFACK [ACKrcvd] id 2 len 19
*May 4 10:12:07.095: Vi1 LCP: MRU 1500 (0x010405DC)
*May 4 10:12:07.095: Vi1 LCP: AuthProto CHAP (0x0305C22305)
*May 4 10:12:07.095: Vi1 LCP: MagicNumber 0x53D691A5 (0x050653D691A5)
*May 4 10:12:07.095: Vi1 LCP: Event[Receive ConfReq+] State[ACKrcvd to Open]
*May 4 10:12:07.099: Vi1 PPP: Queue CHAP code[1] id[1]
*May 4 10:12:07.123: Vi1 PPP: Phase is AUTHENTICATING, by the peer
*May 4 10:12:07.123: Vi1 CHAP: Redirect packet to Vi1
*May 4 10:12:07.123: Vi1 CHAP: I CHALLENGE id 1 len 33 from "PPPoE_server"
*May 4 10:12:07.123: Vi1 LCP: State is Open
*May 4 10:12:07.123: Vi1 CHAP: Using hostname from interface CHAP
*May 4 10:12:07.123: Vi1 CHAP: Using password from interface CHAP
*May 4 10:12:07.123: Vi1 CHAP: O RESPONSE id 1 len 27 from "johnny"
*May 4 10:12:07.147: Vi1 CHAP: I SUCCESS id 1 len 4
*May 4 10:12:07.147: Vi1 PPP: Phase is FORWARDING, Attempting Forward
*May 4 10:12:07.147: Vi1 PPP: Phase is ESTABLISHING, Finish LCP
*May 4 10:12:07.147: Vi1 PPP: No AAA accounting method list
*May 4 10:12:07.147: Vi1 PPP: Phase is UP
*May 4 10:12:07.147: Vi1 IPCP: Protocol configured, start CP. state[Initial]
*May 4 10:12:07.147: Vi1 IPCP: Event[OPEN] State[Initial to Starting]
*May 4 10:12:07.147: Vi1 IPCP: O CONFREQ [Starting] id 1 len 22
*May 4 10:12:07.147: Vi1 IPCP: Address 0.0.0.0 (0x030600000000)
*May 4 10:12:07.147: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000)
*May 4 10:12:07.147: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000)
*May 4 10:12:07.147: Vi1 IPCP: Event[UP] State[Starting to REQsent]
*May 4 10:12:07.147: Vi1 CDPCP: Protocol configured, start CP. state[Initial]
*May 4 10:12:07.147: Vi1 CDPCP: Event[OPEN] State[Initial to Starting]
*May 4 10:12:07.147: Vi1 CDPCP: O CONFREQ [Starting] id 1 len 4
*May 4 10:12:07.147: Vi1 CDPCP: Event[UP] State[Starting to REQsent]
*May 4 10:12:07.147: Vi1 IPCP: I CONFREQ [REQsent] id 1 len 10
*May 4 10:12:07.147: Vi1 IPCP: Address 10.10.10.1 (0x03060A0A0A01)
*May 4 10:12:07.147: Vi1 IPCP: O CONFACK [REQsent] id 1 len 10
*May 4 10:12:07.147: Vi1 IPCP: Address 10.10.10.1 (0x03060A0A0A01)
*May 4 10:12:07.147: Vi1 IPCP: Event[Receive ConfReq+] State[REQsent to ACKsent]
*May 4 10:12:07.155: Vi1 LCP: I PROTREJ [Open] id 3 len 10 protocol CDPCP (0x01010006)
*May 4 10:12:07.155: Vi1 CDPCP: Event[Receive CodeRej-] State[REQsent to Stopped]
*May 4 10:12:07.159: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
*May 4 10:12:09.139: Vi1 IPCP: O CONFREQ [ACKsent] id 2 len 22
*May 4 10:12:09.139: Vi1 IPCP: Address 0.0.0.0 (0x030600000000)
*May 4 10:12:09.139: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000)
*May 4 10:12:09.139: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000)
*May 4 10:12:09.139: Vi1 IPCP: Event[Timeout+] State[ACKsent to ACKsent]
*May 4 10:12:09.147: Vi1 IPCP: I CONFREQ [ACKsent] id 2 len 10
*May 4 10:12:09.147: Vi1 IPCP: Address 10.10.10.1 (0x03060A0A0A01)
*May 4 10:12:09.147: Vi1 IPCP: O CONFACK [ACKsent] id 2 len 10
*May 4 10:12:09.147: Vi1 IPCP: Address 10.10.10.1 (0x03060A0A0A01)
*May 4 10:12:09.147: Vi1 IPCP: Event[Receive ConfReq+] State[ACKsent to ACKsent]
*May 4 10:12:09.155: Vi1 IPCP: I CONFREJ [ACKsent] id 2 len 10
*May 4 10:12:09.155: Vi1 IPCP: SecondaryDNS 0.0.0.0 (0x830600000000)
*May 4 10:12:09.155: Vi1 IPCP: O CONFREQ [ACKsent] id 3 len 16
*May 4 10:12:09.155: Vi1 IPCP: Address 0.0.0.0 (0x030600000000)
*May 4 10:12:09.155: Vi1 IPCP: PrimaryDNS 0.0.0.0 (0x810600000000)
*May 4 10:12:09.155: Vi1 IPCP: Event[Receive ConfNak/Rej] State[ACKsent to ACKsent]
*May 4 10:12:09.155: Vi1 IPCP: I CONFNAK [ACKsent] id 3 len 16
*May 4 10:12:09.155: Vi1 IPCP: Address 10.10.10.223 (0x03060A0A0ADF)
*May 4 10:12:09.155: Vi1 IPCP: PrimaryDNS 9.1.0.150 (0x810609010096)
*May 4 10:12:09.155: Vi1 IPCP: O CONFREQ [ACKsent] id 4 len 16
*May 4 10:12:09.155: Vi1 IPCP: Address 10.10.10.223 (0x03060A0A0ADF)
*May 4 10:12:09.155: Vi1 IPCP: PrimaryDNS 9.1.0.150 (0x810609010096)
*May 4 10:12:09.155: Vi1 IPCP: Event[Receive ConfNak/Rej] State[ACKsent to ACKsent]
*May 4 10:12:09.159: Vi1 IPCP: I CONFACK [ACKsent] id 4 len 16
*May 4 10:12:09.159: Vi1 IPCP: Address 10.10.10.223 (0x03060A0A0ADF)
*May 4 10:12:09.159: Vi1 IPCP: PrimaryDNS 9.1.0.150 (0x810609010096)
*May 4 10:12:09.159: Vi1 IPCP: Event[Receive ConfAck] State[ACKsent to Open]
*May 4 10:12:09.171: Vi1 IPCP: State is Open
*May 4 10:12:09.171: Di0 IPCP: Install negotiated IP interface address 10.10.10.223
*May 4 10:12:09.171: %CAPWAP-3-ERRORLOG: Failed to get PPP adjacency for CAPWAP forwarding 0
*May 4 10:12:09.171: PPPoE : ipfib_encapstr prepared
*May 4 10:12:09.175: Di0 Added to neighbor route AVL tree: topoid 0, address 10.10.10.1
*May 4 10:12:09.175: Di0 IPCP: Install route to 10.10.10.1
*May 4 10:12:09.175: PPPoE : ipfib_encapstr preparedSP WiFi Updates on Wireless LAN Controller - 7.3 Release
Features and Use Cases in Release 1.0
The main features supported in Release 1.0 include:
• Controlling, securing, and differentiating services through intelligent policies embedded directly in the network or received through open and standards-based control interfaces to the basic service set (BSS)
• Customizing service convergence with zero-touch provisioning across customized networks
• Authenticating and authorizing subscribers using Dynamic Host Configuration Protocol (DHCP), RADIUS-based authentication, web logon, Wireless Internet Service Provider roaming (WISPr), MAC address, and IP address
• Controlling and accounting for per-subscriber and per-service use for postpaid and prepaid billing
• Validating high availability under high scale for:
– Number of access points per controller
– Subscriber count
– Call rates
– Load balancers
Cisco SP Wi-Fi Services Overview
Our SP Wi-Fi Services portfolio is a comprehensive set of services representing a holistic approach to the total lifecycle of service provider Wi-Fi engagements. Starting with a proof of concept, it covers the end-to-end spectrum of planning, building, optimization, and operation services, each assured by Cisco service-level agreements (SLAs). These services are flexible and can be customized.
• Cisco SP Wi-Fi Proof of Concept Service
– Demonstration of a centralized management system, with zero-touch service fulfillment for rapid deployments of meshed access points, using a cloud-based architecture hosted in a Cisco data center
• Cisco SP Wi-Fi RF Plan and Build Service
– Professional services from Cisco and our Wi-Fi specialized partners
– Help in planning and deploying the RF components of the Cisco SP Wi-Fi solution
– Analysis of architectural readiness, with guidance on selecting and prioritizing locations for Wi-Fi
– RF expertise to obtain the most from your wireless access points
– Coverage and capacity planning
– Post-deployment RF analysis assistance to promote deployment success
• Cisco SP Wi-Fi Core Plan and Build Service
– Professional services from Cisco and our Wi-Fi specialized partners
– Help planning and deploying the core components of the Cisco SP Wi-Fi solution
– Analysis of architectural readiness and assistance with the SP Wi-Fi deployment design
– Start-to-finish deployment assistance, including a mobile subscriber policy enforcement system
– Pre-deployment validation to help ensure deployment success
– Post-deployment knowledge transfers to help ensure your understanding of the solution
• Cisco SP Wi-Fi Solution Support Service (Reactive)
– Expert assistance to streamline operation of the Wi-Fi architecture
– Quick isolation and remediation of unplanned service disruptions
– Tracking and identification of the root cause of disruptive incidents, which provides valuable information for design changes and to help you scale with mobile subscriber growth
• Cisco SP Wi-Fi Optimization Services (Proactive)
– Expert analysis and recommendations for transforming your Wi-Fi architecture into a high-performing, efficient environment
– Help creating a strategy for managing all the critical components of the Cisco SP Wi-Fi architecture using a suite of Cisco hosted network management applications
– Availability and performance optimization expertise to validate your planned design changes
– Collaboration in developing a strategy for managing software releases and changes
– Continuous learning activities that help your IT staff become more self-sufficient
• Cisco SP Wi-Fi Assurance Service (Preemptive)
– Extension of the measurement and analytical capabilities provided by your Cisco SP Wi-Fi architecture
– Real-time monitoring of various key performance indicators (KPIs) from Cisco network operations center
– Comprehensive analytics using fault, capacity, availability, and performance information to help ensure reliable operations
• Cisco SP Wi-Fi Operate Service (End-to-End Platform Management)
– Monitoring of the managed devices in the your environment to help ensure access points and controllers are properly activated and provisioned
– Management of incident and problem resolution
– Identification of operational trends to continually improve performance
Cisco Service Provider Wi-Fi Solution 3.0 Data Sheet
Reference
Packet Flow Between Cisco PPPoE Access Point (AP) and PPPoE server - Service Provider Wi-Fi
Service Provider Wi-Fi - MAC-Auth-Failover Feature Support
DHCP Option 82 - Service Provider Wi-Fi
- 1000
- 1040
- 1100
- 1100_ap
- 1100_lap
- 1130_AG
- 1130_ap
- 1130_lap
- 1140
- 1140_ap
- 1140_lap
- 1200
- 1200_ap
- 1200_lap
- 1230_AG
- 1230_ap
- 1230_lap
- 1240_AG
- 1240_ap
- 1240_lap
- 1250
- 1250_ap
- 1250_lap
- 1260
- 1300
- 1300_bridge
- 1400
- 1400_bridge
- 1500
- 1500_map
- 1520
- 1550
- 1600
- 2000_wlc
- 2100_wlc
- 2500
- 2600
- 3300_Series_Mobility_Services_Engine
- 340_ap
- 3500
- 350_ap
- 3600
- 3750_wlc
- 4400_wlc
- 500_lap
- 5500
- 5500_wlc
- 5505
- 5508
- 5700
- 600_Series OfficeExtend_AP
- 7900_ip_phone
- 802.11a
- 802.11b
- 802.11g
- 8500
- aaa
- active_directory
- air_cb21ag
- aironet
- aironet_antennas
- ap
- autonomous
- cisco_prime_ncs
- configuration
- configuration_example
- eap
- eap_fast
- hwic_ap
- lap
- leap
- lwapp
- ncs
- peap
- prime
- Prime_Network_Control_System
- radio
- radius
- roaming
- service_provider
- service_provider_wi-fi
- ssid
- tacacs
- tkip
- virtual_wireless_controller
- vowlan
- wcs
- wgb
- wireless_lan_controller
- wireless_lan_controllers
- wireless_vlan
- wism
- wlan
- wlc
- wlc_5500
- wlc_5508
- wlcm
- wlse
- wlsm
- wpa
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
When I use the command, it gives me an error, help me, I use air ap3602i.
ap(config)#int dialer 0
^
% Invalid input detected at '^' marker
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@hoanghoang93 maybe you didn't read the guide fully:
"Note - Only Flexconnect Access Point supports PPPoE. PPPoE can be configured as submode of Flexconnect mode."
So this is a controller based (CAPWAP) AP feature.
The fact that you're trying to configure that at an AP config prompt suggests you're trying to configure that on an autonomous AP where it will not be supported (as you discovered).
You can enable the feature directly on a CAPWAP AP as per:
https://www.cisco.com/c/en/us/td/docs/wireless/controller/8-8/config-guide/b_cg88/flexconnect_ap_easy_admin.html#ID1133
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: