- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: ACL / WLC / ISE Question
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2020 06:32 PM - edited 07-05-2021 11:34 AM
Hi everyone,
Thanks in advance for taking the time to read this post and for any advice or help offered.
I am a contractor working for a customer. I am familiar enough with Cisco switching, but this is my first exposure to both Cisco wireless/WLC and ISE and both seem a little beyond me right now.
Here is the issue. We need to allow a certain VLAN to send traffic to TCP destination port 631 for printing. I believe it is being blocked by an ACL. I thought I had located the ACL on the WLC and adjusted it properly to allow printing, but my change did not have the intended affect. I created an ACL permit rule to allow ICMP to a test server, and that is not working either.
There is a FlexConnect ACL and a regular ACL configured on the WLC. Both are named "INTERNET_ONLY" and appear to be the same set of permit and deny statements, however config changes to one do not propagate to the other, so I know they are separate. My focus has been on the FlexConnect ACL but I have also tested w/ the regular ACL.
The access point to which our test client is associated is a member of a FlexConnect group. When I navigate to FlexConnect Groups > relevant group > ACL Mapping > AAA VLAN-ACL mapping, I see that Vlan Id 960 has an ingress and egress ACL of "PERMIT_ALL_TRAFFIC". Vlan Id 970 has an ingress ACL of "PERMIT_ALL_TRAFFIC" and an egress ACL of "INTERNET_ONLY". My understanding is that in this context, ingress and egress are opposite to what might be traditionally assumed, so egress ACL would refer to traffic coming FROM the client, and ingress ACL would refer to traffic going TO the client.
I did investigate the ACL "PERMIT_ALL_TRAFFIC" and it is configured to permit source 0.0.0.0/0.0.0.0 to destination 0.0.0.0/0.0.0.0 for all protocols, ports and DSCP settings.
Our clients are authenticating via 802.1x and AD credentials through ISE. If the clients are in a special MAC address whitelist on ISE, they are put into vlan 960. If they are not in that whitelist, they are put into VLAN 970. The test client when put into VLAN 960 does not have any issue printing or accessing other network resources. The test client when put into VLAN 970 cannot print or access most network resources (intended behavior besides not being able to print).
Here is one of the more interesting parts. The ACL in question does appear to be in effect for the VLAN 970 clients. There are some permit statements to allow TCP destination port 80 to some servers, and some of those servers are accessible via the browser on port 80 for the VLAN 970 client. I assume other servers that are not reachable have been decomissioned.
I have checked the VLAN interface on the distribution/layer 3 switch, and no ACLs are applied to either VLAN 960 or 970. I believe the client traffic is locally switched from the AP (rather than tunneling back to the controller), since a Wireshark capture on the spanned access point switchport was able to clearly see printing traffic from VLAN 960 from my test client with no evidence of that traffic being tunneled. TCP traffic to destination port 631 was the only connection or traffic initiated from the client to the printer for a successful print session. Routing should be taking place on said layer 3 switch, as VLAN 960, VLAN 970 and the printer VLAN are directly connected routes on that switch.
ISE also has an INTERNET_ONLY ACL, but it is much shorter and only seems to allow access to the ISE servers for 802.1x authentication.
I believe my ACL rules are sound, but please feel free to review:
(Cisco Controller) >show flexconnect acl detailed INTERNET_ONLY
Source Destination Source Port Dest Port
Index IP Address/Netmask IP Address/Netmask Prot Range Range DSCP Action
------ ------------------------------- ------------------------------- ---- ----------- ----------- ----- -------
1 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 17 0-65535 53-53 Any Permit
2 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 17 53-53 0-65535 Any Permit
3 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 17 68-68 67-67 Any Permit
4 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 17 67-67 68-68 Any Permit
5 0.0.0.0/0.0.0.0 [serverA]/255.255.255.255 6 0-65535 443-443 Any Permit
6 0.0.0.0/0.0.0.0 [ISE Server 1]/255.255.255.255 6 0-65535 8443-8443 Any Permit
7 0.0.0.0/0.0.0.0 [ISE Server 2]/255.255.255.255 6 0-65535 8443-8443 Any Permit
8 0.0.0.0/0.0.0.0 [serverB]/255.255.255.255 6 0-65535 80-80 Any Permit
9 0.0.0.0/0.0.0.0 [serverB]/255.255.255.255 6 0-65535 443-443 Any Permit
10 0.0.0.0/0.0.0.0 [serverC]/255.255.255.255 6 0-65535 80-80 Any Permit
11 0.0.0.0/0.0.0.0 [serverC]/255.255.255.255 6 0-65535 443-443 Any Permit
12 0.0.0.0/0.0.0.0 [serverD]/255.255.255.255 6 0-65535 80-80 Any Permit
13 0.0.0.0/0.0.0.0 [serverD]/255.255.255.255 6 0-65535 443-443 Any Permit
14 0.0.0.0/0.0.0.0 [serverE]/255.255.255.255 6 0-65535 80-80 Any Permit
15 0.0.0.0/0.0.0.0 [serverE]/255.255.255.255 6 0-65535 443-443 Any Permit
16 0.0.0.0/0.0.0.0 [serverF]/255.255.255.255 6 0-65535 80-80 Any Permit
17 0.0.0.0/0.0.0.0 [serverF]/255.255.255.255 6 0-65535 443-443 Any Permit
18 0.0.0.0/0.0.0.0 [serverG]/255.255.255.255 6 0-65535 8080-8080 Any Permit
19 0.0.0.0/0.0.0.0 [serverG]/255.255.255.255 6 0-65535 8443-8443 Any Permit
20 0.0.0.0/0.0.0.0 [serverH]/255.255.255.255 6 0-65535 80-80 Any Permit
>21 0.0.0.0/0.0.0.0 [test ICMP server]/255.255.255.255 1 0-65535 0-65535 Any Permit
22 0.0.0.0/0.0.0.0 [serverI]/255.255.255.255 6 0-65535 80-80 Any Permit
>23 0.0.0.0/0.0.0.0 [test printing]0.0.0.0/0.0.0.0 6 0-65535 631-631 Any Permit
24 0.0.0.0/0.0.0.0 10.0.0.0/255.0.0.0 Any 0-65535 0-65535 Any Deny
25 0.0.0.0/0.0.0.0 172.16.0.0/255.240.0.0 Any 0-65535 0-65535 Any Deny
26 0.0.0.0/0.0.0.0 192.168.0.0/255.255.0.0 Any 0-65535 0-65535 Any Deny
27 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0 Any 0-65535 0-65535 Any Permit
So, here are my questions:
1) Are FlexConnect ACL changes applied immediately, or do I need to do something to update AP configurations so they will take effect?
2) Am I looking in the correct place to see that this ACL is being applied to VLAN 970 clients?
3) Where might alternative ACLs be coming from? My understanding is that ISE might be able to deliver a AAA override ACL on a per client basis. I might be completely misunderstanding this concept.
My confusion mostly stems from believing I have found the ACL responsible for blocking the printer traffic, but also finding that my changes are not allowing the traffic.
Thanks again for taking the time to read and for any help you might be able to provide. Jumping into this has felt like trying to untangle a big knot.
Thanks,
Cameron
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2020 08:48 PM
Flex acl is the right place if your ssid is locally switched.
Your AP can be in flexconnect but your ssid could be in central or local switching (on the advanced tab of the ssid at the bottom left, there's a checkbox to make the ssid centrally switched).
After you modified your acl, client has to disconnect and reconnect.
On ISE, is any acl pushed dynamically? If so maybe you're modifying the wrong acl.
On your wlc, on the home tab, under client menu (left menu), you can see your client and if you click on the mac address you'll view all details like the acl being applied. Can you verify that you have the correct acl?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2020 08:48 PM
Flex acl is the right place if your ssid is locally switched.
Your AP can be in flexconnect but your ssid could be in central or local switching (on the advanced tab of the ssid at the bottom left, there's a checkbox to make the ssid centrally switched).
After you modified your acl, client has to disconnect and reconnect.
On ISE, is any acl pushed dynamically? If so maybe you're modifying the wrong acl.
On your wlc, on the home tab, under client menu (left menu), you can see your client and if you click on the mac address you'll view all details like the acl being applied. Can you verify that you have the correct acl?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2020 04:34 PM - edited 01-22-2020 04:54 PM
Hey Francesco,
Thank you very much for taking the time to read and reply.
We did reauthenticate the test client to the SSID after making the ACL change, even going as far as rebooting the client (which is a Chromebook)
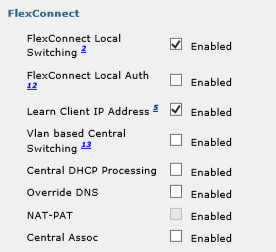
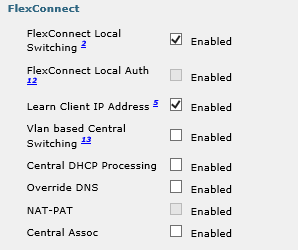
I have discovered something in investigating to find the answers to your questions. There are two WLAN profiles which reference a WLAN SSID name of "workstation". One of the profiles is named "Wireless Data", the other is named "Wireless_Data_ISE".
"Wireless Data" advanced settings:
"Wireless_Data_ISE" advanced settings:
I think this means the SSID is not centrally switched.
Another thing I have noticed is that "Wireless_Data_ISE" has "Allow AAA Override" checked on the Advanced tab, while "Wireless Data" does not.
There is an "INTERNET_ONLY" ACL in ISE, but it does not have permit statements for the few web servers that are working like the ACLs in the WLC have. ISE INTERNET_ONLY ACL:
permit udp any eq bootpc any eq bootps
permit udp any any eq domain
permit tcp any host [ISEserver1] eq 8443
permit tcp any host [ISEserver2] eq 8443
deny ip any 10.0.0.0 0.255.255.255
deny ip any 172.16.0.0 0.15.255.255
deny ip any 192.168.0.0 0.0.255.255
permit ip any any
For "BYOD", which is the Authorization Profile Result that ISE is matching the client with when we cannot print, under common tasks, only the VLAN option is checked, with "970" in the field. DACL Name is not checked. For "DPS_Workstation", which is the Authorizatoin Profile Result that ISE is matching the client with when we can print, only the VLAN option is checked, with "960" in the field. DACL Name is also not checked.
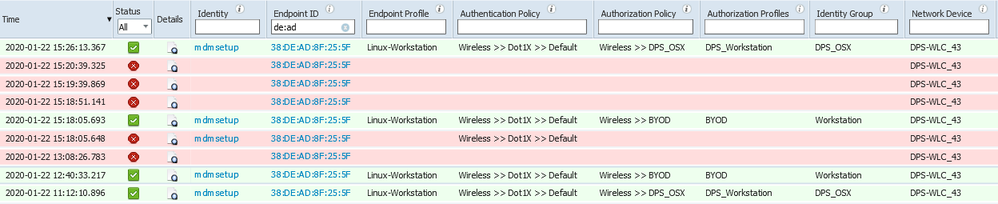
Here are the ISE Authorization/Authentication results:
If you check out the bottom two rows, the "DPS_OSX" authorization policy association is allowed to print and send other traffic, while the "BYOD" authorization policy is not. I think "DPS_OSX" is really just a MAB whitelist of MAC addresses--when we add the client to that list, we get the "DPS_OSX" treatment. Correction: DPS_OSX is the Identity Group where we define which MAC addresses belong to that group. I find ISE to be a bit confusing and haven't worked out all the pieces yet.
We will try to check the ACL being applied to the client ASAP. I am not on site this week so I am working with my colleague to gather info.
Thank you again for taking the time to help!
Cheers,
Cameron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2020 12:41 PM
Hi
AAA Override is needed when using radius to be able to change attributes based on client authentication.
On your acl, if it's to only allow internet access without portal authentication/onboarding, the 2 lines for ISE allowing port 8443 are useless.
The ACL is in ISE right? it's a dACL. On your authorization profile, you have a field airespace_acl which is the name of the ACL hosted on the WLC if any ACL is being pushed. DACL aren't working with wireless. The name of ACL is referring to an acl configured on your wlc.
When the user is authenticated, on your wlc, on the client details, you'll see which acl is being applied and this is the one you need to modify.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 05:58 AM
Hi Francesco,
Thank you again for responding.
I had not noticed the "Airespace ACL Name" option before. However, it is not checked for either of the relevant Authorization Profiles.
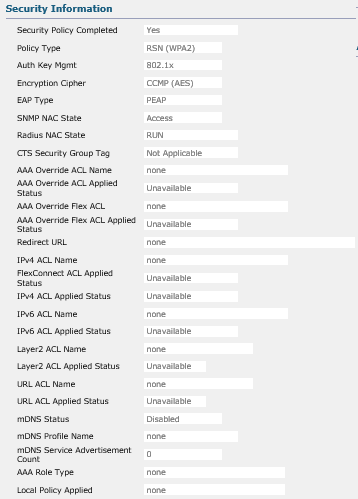
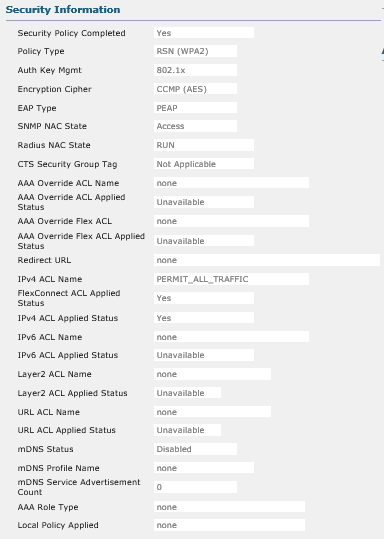
I am back onsite today and can do further testing. I am seeing the following for my test client:
Hopefully this means more to you than it does to me. It doesn't seem too helpful at first glance. The client has been authenticated for several minutes at this point so I would think all relevant information would have time to update.
Compare that to a VLAN 960 client, who has authenticated the same way, but has been placed into VLAN 960 due to its MAC address being in DPS_OSX group in ISE:
It shows that the IPv4 ACL is applied and active and FlexConnect ACL are applied and active. I am going to poke around in ISE some more for now since I am starting to think that the ACL being applied to the clients is actually hosted there...somewhere.
Any and all help or insight is appreciated--thank you.
Cameron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 06:37 AM
Just adding some more info here...I am back to thinking that ISE is not providing the ACL via AAA override based on these authentication results taken from ISE, which, as far as I understand it, should show if an ACL is being provided via RADIUS:
Overview
Event 5200 Authentication succeeded
Username test_user
Endpoint Id 06:5C:D4:29:37:8C
Endpoint Profile
Authentication Policy Wireless >> Dot1X >> Default
Authorization Policy Wireless >> BYOD
Authorization Result BYOD
Authentication Details
Source Timestamp 2020-01-27 08:04:04.936
Received Timestamp 2020-01-27 08:04:04.937
Policy Server isepan01
Event 5200 Authentication succeeded
Failure Reason
Resolution
Root cause
Username test_user
User Type
Endpoint Id 06:5C:D4:29:37:8C
Endpoint Profile
IP Address
Authentication Identity Store AD1
Identity Group
Audit Session Id 2bc819ac019c1e93c4df2e5e
Authentication Method dot1x
Authentication Protocol PEAP (EAP-MSCHAPv2)
Service Type Framed
Network Device company_name-WLC_43
Device Type All Device Types#Wireless Controllers
Location All Locations#company_name
NAS IP Address 172.25.200.43
NAS Port Id
NAS Port Type Wireless - IEEE 802.11
Authorization Profile BYOD
Posture Status
Security Group
Response Time 9
Other Attributes
ConfigVersionId 36
DestinationPort 1812
Protocol Radius
NAS-Port 8
Framed-MTU 1300
State 37CPMSessionID=2bc819ac019c1e93c4df2e5e;37SessionID=isepan01/364781611/28154874;
Acct-Session-Id 5e2edfc4/06:5c:d4:29:37:8c/32432860
Tunnel-Type (tag=0) VLAN
Tunnel-Medium-Type (tag=0) 802
Tunnel-Private-Group-ID (tag=0) 960
undefined-89 +
undefined-131
Airespace-Wlan-Id 17
AcsSessionID isepan01/364781611/28154874
SelectedAuthenticationIdentityStores AD1
SelectedAuthenticationIdentityStores Internal Users
SelectedAuthenticationIdentityStores Internal Endpoints
AuthorizationPolicyMatchedRule BYOD
CPMSessionID 2bc819ac019c1e93c4df2e5e
EndPointMACAddress 06-5C-D4-29-37-8C
ISEPolicySetName Wireless
AllowedProtocolMatchedRule Dot1X
IdentitySelectionMatchedRule Default
AD-Domain company_name_domain.local
AD-User-Candidate-Identities test_user@company_name_domain.local
AD-User-Join-Point company_name_domain.LOCAL
AD-User-Resolved-DNs CN=test_user,OU=Employees,OU=People,DC=company_name_domain,DC=local
AD-Groups-Names company_name_domain.local/IAM Groups/company_name-Staff/District/281-ITD/ACS Full Access
AD-Groups-Names company_name_domain.local/Groups/Domain Users
AD-Groups-Names company_name_domain.local/IAM Groups/company_name-Apps/ISE-Admins
Main Main#company_name
Location Location#All Locations#company_name
Device Type Device Type#All Device Types#Wireless Controllers
IdentityAccessRestricted false
AD ExternalGroups S-1-5-21-1198204733-3122656313-790680861-329297
AD ExternalGroups S-1-5-21-1198204733-3122656313-790680861-513
AD ExternalGroups S-1-5-21-1198204733-3122656313-790680861-323820
RADIUS Username test_user
NAS-Identifier company_name-WLC-43
Device IP Address 172.25.200.43
Called-Station-ID dc-a5-f4-64-e0-e0:workstation
CiscoAVPair audit-session-id=2bc819ac019c1e93c4df2e5e,
mDNS=true
Result
State ReauthSession:2bc819ac019c1e93c4df2e5e
Class CACS:2bc819ac019c1e93c4df2e5e:isepan01/364781611/28154874
Tunnel-Type (tag=1) VLAN
Tunnel-Medium-Type (tag=1) 802
Tunnel-Private-Group-ID (tag=1) 970
MS-MPPE-Send-Key ****
MS-MPPE-Recv-Key ****
LicenseTypes 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2020 06:40 PM
As you're running in flexconnect mode, have you verified if any acl was configured on the svi? Or does this vlan goes through a firewall?
Can you post the current flexconnect acl and the ssid/flexconnect group config?
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-28-2020 08:00 AM
Well, after rebooting the WLC and the AP last night, the ACL seems to be working as intended now. I am able to print (TCP Destination Port 631) and ping (ICMP) from VLAN 970 this morning on my test device, and another site has just confirmed that printing is working for them as well.
At least I learned a few things on my way to the reboot. My understanding is that FlexConnect ACL changes should take effect rather instantaneously, as long as the client re-authenticates.
Thank you very much for taking the time to help and take care.
Cameron
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-23-2024 08:28 AM
While in the dot1x implementation, Cisco ISE as radius Servers, APs as MAB , I am trying to have APs communicate to network devices , it needs to.
Q#1 dACL is defined in ISE and gets assigned as per radius logs and "Essential license" gets consumed. The authentication and authorization is successful, however, there is no IP assigned to the access point in closed mode.
On the other hand, IP gets assigned in Monitor mode. ACL remains same .
Followed this document and created ACL table 5 Understand Unified Wireless Network Protocol (CUWN WLC) and Port Matrix - Cisco https://www.cisco.com/c/en/us/support/docs/wireless/5500-series-wireless-controllers/113344-cuwn-ppm.html
permit udp any eq 68 any eq 67
permit udp any any eq 53
permit ip any (WLC Host)
permit ip host WLC any
permit ip any x.x.x.x (radius server)
permit icmp any any
deny ip any any
Can you please help , why IP is not getting assigned in closed mode and the purpose is the AP should access necessary devices access for (device authentication essentially) .
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide