- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- External DHCP not working in a foreign / Guest anchor setup
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-16-2021 02:54 PM - edited 08-16-2021 04:14 PM
hello all,
I have setup a centralized guest wireless design in my lab but can not for the life of me get DHCP to work from my internal dhcp servers for clients joining the guest network.
Things i have tried but did not work:
- on the guest anchor, set management svi to also relay dhcp - failed
- on the guest anchor, set the svi for guest-dmz network to relay and set source interface to mgmt - failed
- on the guest anchor, globally set dhcp relay on Gig2 (trunk) interface - failed
What has worked:
- adding guest anchor ip to Policy profile on both foreign and guest anchor
- creating dhcp pool on guest anchor, which uses internal dns server
- this allows the client to obtain a valid dhcp lease for the guest dmz subnet which in turn kicks off the CWA process which can be completed successfully and guest access to the internet works fine.
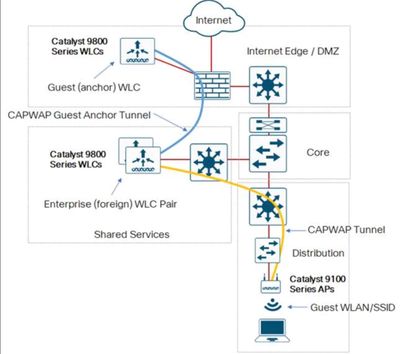
Design Overview
Additional Details
both controllers are 9800-cl virtual controllers
mobility tunnel is configured and up between both foreign and guest anchor
Foreign Controller:
Management Vlan: 72
Wireless Management SVI Interface: interface vlan 72 (172.16.72.10)
Guest Anchor:
Management Vlan: 300
Wireless Management SVI Interface: interface vlan 300 (10.1.1.11) (DMZ network which is L2 on the campus lan and l3 off an interface on the internet facing firewall)
Guest Wireless Network: 10.1.5.0/24
Guest Vlan: 105
Guest SVI Interface: interface vlan 105 (10.1.5.2) (Guest-DMZ network which is L2 on the lan and l3 off an interface on the internet facing firewall)
firewall has static routes pointing towards the core switch where firewall is connected (vlan + l3 svi) for both the DMZ network and the Guest-DMZ network
core switch has static routes pointing to the firewall nexthop for each of the dmz networks
firewall rules allow ip between zones (zone to internet [outside] is more restrictive but that's not the issue at the moment)
- inside to dmz / dmz to inside / dmz to outside
- inside to guest dmz / guest dmz to inside / guest dmz to outside
- dmz to guest dmz / guest dmz to dmz
- inside to outside
Solved! Go to Solution.
- Labels:
-
Catalyst Wireless Controllers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2021 12:58 AM
Hi Jay,
DHCP relay on Catalyst 9800 is not fully upported at this time so the only thing that will work 100% is to configure DHCP relay on the firewall or, if any, on any L3 switch you may have between anchor controller and the firewall.
HTH
-Jesus
*** Please Rate Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2021 02:05 PM
Make sure that you have the VM switch correctly configured. https://www.cisco.com/c/en/us/products/collateral/wireless/catalyst-9800-cl-wireless-controller-cloud/nb-06-cat9800-cl-wirel-cloud-dep-guide-cte-en.html
Also can you post the policy profiles of both WLC's? If your upstream ports are correctly configured you dont need to create a L3 SVI for Guest VLAN on Foreign controller.
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2021 05:34 AM
On the VM switch side i have this configured correctly per all of the documentation. it's important to note at this point i currently have dhcp configured and working on the guest anchor. the preferred design would be to use an external dhcp server (ie microsoft dhcp servers in failover configuration)
here are the policy profiles as requested.
Foreign Controller
9800-wlc01#show wireless profile policy detailed anchor-policy-profile
Policy Profile Name : anchor-policy-profile
Description :
Status : ENABLED
VLAN : 105
Multicast VLAN : 0
OSEN client VLAN :
Multicast Filter : DISABLED
QBSS Load : ENABLED
Passive Client : DISABLED
ET-Analytics : DISABLED
StaticIP Mobility : DISABLED
WLAN Switching Policy
Flex Central Switching : ENABLED
Flex Central Authentication : ENABLED
Flex Central DHCP : ENABLED
Flex NAT PAT : DISABLED
Flex Central Assoc : ENABLED
WLAN Flex Policy
VLAN based Central Switching : DISABLED
WLAN ACL
IPv4 ACL : Not Configured
IPv6 ACL : Not Configured
Layer2 ACL : Not Configured
Preauth urlfilter list : Not Configured
Postauth urlfilter list : Not Configured
WLAN Timeout
Session Timeout : 1800
Idle Timeout : 300
Idle Threshold : 0
Guest LAN Session Timeout : DISABLED
WLAN Local Profiling
Subscriber Policy Name : Not Configured
RADIUS Profiling : DISABLED
HTTP TLV caching : DISABLED
DHCP TLV caching : DISABLED
CTS Policy
Inline Tagging : DISABLED
SGACL Enforcement : DISABLED
Default SGT : 0
WLAN Mobility
Anchor : DISABLED
AVC VISIBILITY : Disabled
IPv4 Flow Monitors
Ingress
Egress
IPv6 Flow Monitors
Ingress
Egress
NBAR Protocol Discovery : Disabled
Reanchoring : Disabled
Classmap name for Reanchoring
Reanchoring Classmap Name : Not Configured
QOS per SSID
Ingress Service Name : Not Configured
Egress Service Name : Not Configured
QOS per Client
Ingress Service Name : Not Configured
Egress Service Name : Not Configured
Umbrella information
Cisco Umbrella Parameter Map : Not Configured
DHCP DNS Option : ENABLED
Mode : ignore
Autoqos Mode : None
Call Snooping : Disabled
Tunnel Profile
Profile Name : Not Configured
Calendar Profile
Fabric Profile
Profile Name : Not Configured
Accounting list
Accounting List : default
DHCP
required : ENABLED
server address : 10.1.1.11
Opt82
DhcpOpt82Enable : DISABLED
DhcpOpt82Ascii : DISABLED
DhcpOpt82Rid : DISABLED
APMAC : DISABLED
SSID : DISABLED
AP_ETHMAC : DISABLED
APNAME : DISABLED
POLICY TAG : DISABLED
AP_LOCATION : DISABLED
VLAN_ID : DISABLED
Exclusionlist Params
Exclusionlist : ENABLED
Exclusion Timeout : 60
AAA Policy Params
AAA Override : ENABLED
NAC : ENABLED
NAC Type : ISE NAC
AAA Policy name : default-aaa-policy
WGB Policy Params
Broadcast Tagging : DISABLED
Client VLAN : DISABLED
Hotspot 2.0 Server name : Not Configured
Mobility Anchor List
IP Address Priority
-------------------------------------------------------
10.1.1.11 3(Tertiary)
mDNS Gateway
mDNS Service Policy name : default-mdns-service-policy
User Defined (Private) Network : Disabled
User Defined (Private) Network Unicast Drop : Disabled
Policy Proxy Settings
ARP Proxy State : DISABLED
IPv6 Proxy State : None
Airtime-fairness Profile
2.4Ghz ATF Policy : default-atf-policy
5Ghz ATF Policy : default-atf-policy
Guest Anchor
9800-wlc03#show wireless profile policy detailed anchor-policy-profile
Policy Profile Name : anchor-policy-profile
Description :
Status : ENABLED
VLAN : 105
Multicast VLAN : 0
OSEN client VLAN :
Multicast Filter : DISABLED
QBSS Load : ENABLED
Passive Client : DISABLED
ET-Analytics : DISABLED
StaticIP Mobility : DISABLED
WLAN Switching Policy
Flex Central Switching : ENABLED
Flex Central Authentication : ENABLED
Flex Central DHCP : ENABLED
Flex NAT PAT : DISABLED
Flex Central Assoc : ENABLED
WLAN Flex Policy
VLAN based Central Switching : DISABLED
WLAN ACL
IPv4 ACL : Not Configured
IPv6 ACL : Not Configured
Layer2 ACL : Not Configured
Preauth urlfilter list : Not Configured
Postauth urlfilter list : Not Configured
WLAN Timeout
Session Timeout : 1800
Idle Timeout : 300
Idle Threshold : 0
Guest LAN Session Timeout : DISABLED
WLAN Local Profiling
Subscriber Policy Name : Not Configured
RADIUS Profiling : DISABLED
HTTP TLV caching : DISABLED
DHCP TLV caching : DISABLED
CTS Policy
Inline Tagging : DISABLED
SGACL Enforcement : DISABLED
Default SGT : 0
WLAN Mobility
Anchor : ENABLED
AVC VISIBILITY : Disabled
IPv4 Flow Monitors
Ingress
Egress
IPv6 Flow Monitors
Ingress
Egress
NBAR Protocol Discovery : Disabled
Reanchoring : Disabled
Classmap name for Reanchoring
Reanchoring Classmap Name : Not Configured
QOS per SSID
Ingress Service Name : Not Configured
Egress Service Name : Not Configured
QOS per Client
Ingress Service Name : Not Configured
Egress Service Name : Not Configured
Umbrella information
Cisco Umbrella Parameter Map : Not Configured
DHCP DNS Option : ENABLED
Mode : ignore
Autoqos Mode : None
Call Snooping : Disabled
Tunnel Profile
Profile Name : Not Configured
Calendar Profile
Fabric Profile
Profile Name : Not Configured
Accounting list
Accounting List : default
DHCP
required : ENABLED
server address : 10.1.1.11
Opt82
DhcpOpt82Enable : DISABLED
DhcpOpt82Ascii : DISABLED
DhcpOpt82Rid : DISABLED
APMAC : DISABLED
SSID : DISABLED
AP_ETHMAC : DISABLED
APNAME : DISABLED
POLICY TAG : DISABLED
AP_LOCATION : DISABLED
VLAN_ID : DISABLED
Exclusionlist Params
Exclusionlist : ENABLED
Exclusion Timeout : 60
AAA Policy Params
AAA Override : ENABLED
NAC : ENABLED
NAC Type : ISE NAC
AAA Policy name : default-aaa-policy
WGB Policy Params
Broadcast Tagging : DISABLED
Client VLAN : DISABLED
Hotspot 2.0 Server name : Not Configured
Mobility Anchor
IP Address Priority
----------------------------------------------------
10.1.1.11 Local
mDNS Gateway
mDNS Service Policy name : default-mdns-service-policy
User Defined (Private) Network : Disabled
User Defined (Private) Network Unicast Drop : Disabled
Policy Proxy Settings
ARP Proxy State : DISABLED
IPv6 Proxy State : None
Airtime-fairness Profile
2.4Ghz ATF Policy : default-atf-policy
5Ghz ATF Policy : default-atf-policy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2021 11:51 PM
Hi, policy profiles looks ok. I would delete that SVI you have created on the Anchor, but leave the L2 VLAN as it is. Make sure to remove all DHCP relays, IP helpers under Management interface and also from the policy profiles.
Then try to sniff the packets in Firewall to see whether DHCP Discover messages are hitting the Firewall.
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2021 12:58 AM
Hi Jay,
DHCP relay on Catalyst 9800 is not fully upported at this time so the only thing that will work 100% is to configure DHCP relay on the firewall or, if any, on any L3 switch you may have between anchor controller and the firewall.
HTH
-Jesus
*** Please Rate Helpful Responses ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2021 06:48 PM
I did try setting up DHCP relay on the firewall but didn't get this working. I can test this again and see if i can get this working.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2021 12:14 PM - edited 08-22-2021 12:16 PM
thanks @JPavonM & @Arshad Safrulla
This is working now, here's what i changed
1. removed the DHCP settings in the policy profile that pointed to the Anchor where I had a dhcp pool setup.
2. Removed DHCP pool on Anchor in the DMZ
3. Setup Dhcp relay on L3 interface on firewall for the Guest Subnet (G1/4 - 10.1.5.1/24) pointed relay towards both internal dhcp servers 172.16.2.20 and 172.16.2.21 (load-balanced windows dhcp)
4. ran a packet capture of a client connecting to anchor-guest ssid
Success!
i've included some screen shots of the packet captures as well for anyone that's interested in seeing as it's rather helpful
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide