- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- apic ssh stronger ciphers
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2021 02:31 PM
Hello. Hope you are all doing fine.
Do you know how to change the ssh ciphers for the apic/leafs/spines connections to be stronger using ctr ciphers instead of cbt?
I can´t acces the devices using ssh if I dont have an older Secure CRT version.
If I try to connect from another switch for example, i get this error:
No matching ciphers found. Client (10.x.x.x) supported ciphers : aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc,rijndael-cbc@lysator.liu.se .Server supported ciphers : aes128-ctr,aes128-gcm@openssh.com,aes192-ctr,aes256-ctr,chacha20-poly1305@openssh.com
So what is asking is to use ctr in order to be able to connect from the switch.... the same from secure.
I know I can enable weaker ciphers on switches but I would like to improve to ctr.
Solved! Go to Solution.
- Labels:
-
APIC
-
Cisco ACI
-
Other ACI Topics
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2021 11:17 PM
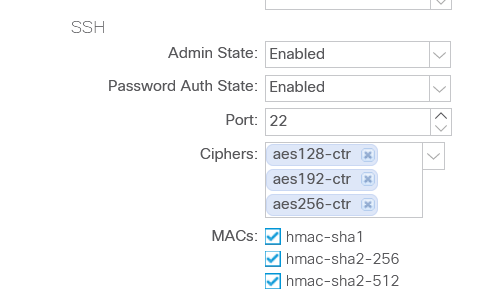
It looks like the CRT is the default one enabled, at least in the version I am running (4.2.5k):
You can find the settings at Fabric -> Fabric Policies -> Policies -> Pod -> Management Access -> Default
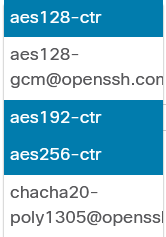
Also, these are the other available cipher options:
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2021 11:17 PM
It looks like the CRT is the default one enabled, at least in the version I am running (4.2.5k):
You can find the settings at Fabric -> Fabric Policies -> Policies -> Pod -> Management Access -> Default
Also, these are the other available cipher options:
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2021 08:10 AM
Hey thank you so much for letting me know where to find those values.
It is really weird cause I have the same version as you and yeah, they are ctr. I just dont understand why when I try to connect from another switch it shows that the apic has cbt.
No matching ciphers found. Client (10.x.x.x) supported ciphers : aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc,rijndael-cbc@lysator.liu.se .Server supported ciphers : aes128-ctr,aes128-gcm@openssh.com,aes192-ctr,aes256-ctr,chacha20-poly1305@openssh.com
10.x.x.x on the message is the APIC IP.
Just to confirm..... ctr is stronger than cbt right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2021 12:57 PM
I think there is a confusion here.
This is the error you receive:
Client (10.x.x.x) supported ciphers : aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc,rijndael-cbc@lysator.liu.se
Server supported ciphers : aes128-ctr,aes128-gcm@openssh.com,aes192-ctr,aes256-ctr,chacha20-poly1305@openssh.com
The client is your application or device from where you try to open the ssh connection.
The server is the APIC.
In other words, APIC supports CTR and your client supports CBC. CTR is more safer cipher compared with CBC. What you need to do is update the application to support CTR as well.
Stay safe,
Sergiu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2021 07:23 AM
Yeah, I thought so, but the log is little bit confusing showing the APIC IP next to the word client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2021 08:20 AM
That is definitely strange. Definitely a good self-suggestion from the switch side to upgrade ^_^
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide