- Cisco Community
- Technology and Support
- Networking
- Cisco Catalyst Center
- DNA LAN Automation faliure (RP-Adress was assigned)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2018 06:58 AM - edited 03-08-2019 05:29 PM
Hi There
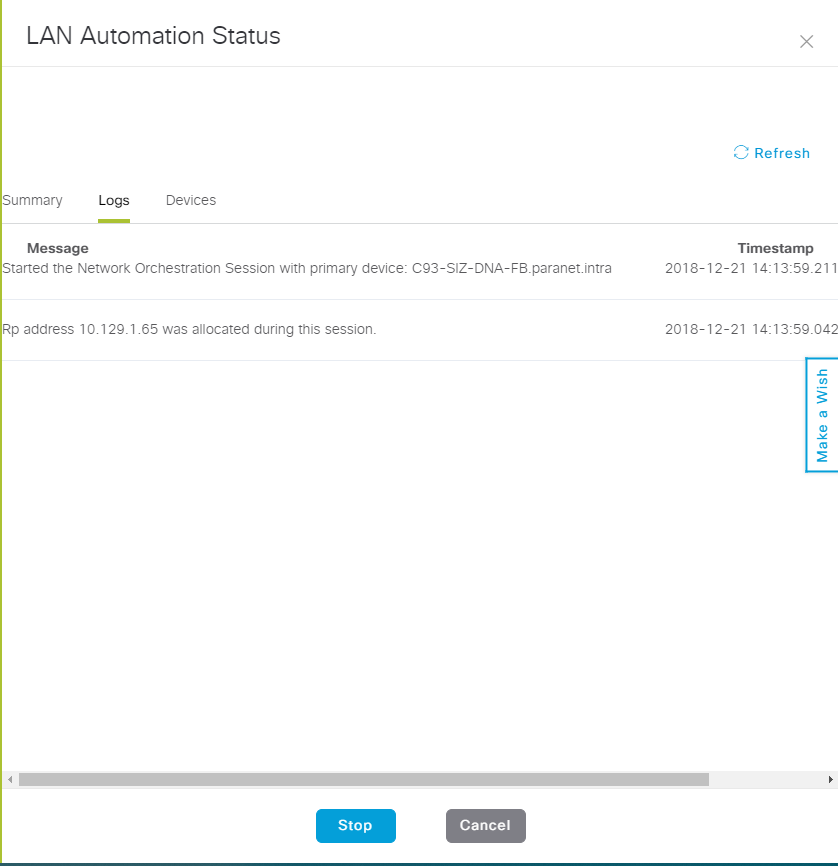
I'm trying to automate my Network Underlay with the DNA Center. I have already configured the Fabric Boarder Switch. When i start the LAN-Automation the DNAC configures the ISIS Router, Creates a DHCP Pool, configures the Interfaces.... But nothing else is happening and following LOG entery is the last shown:
Does someone has a clue wehre the Problem coud be?
Thanks for your replys.
Solved! Go to Solution.
- Labels:
-
Cisco DNA Automation
-
Cisco DNA Center
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2018 01:08 PM
seems like it was running ok, until you did show run, when the discovery stopped, i can be wrong, I am enclosing the logs from my testing, to show you how the expected behavior should be.
in some cases I have seen it take as long as 30 minutes for the automation to finish, after which you will have to manually stop discovery from DNAC for the LAN automation to complete and push some last configs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 04:28 AM
Let me rephrase if I understood it right, assuming the Access is directly connected to Border, you started LAN automation on a specific port with Border as seed, then
did border vlan 1 interface was configured for ISIS as part of LAN Automation or the actual interface where Edge is connected ?
On Edge vlan 1 interface was configured for ISIS as part of LAN Automation or the actual interface where Border is connected ?
do you have a logs from Edge while LAN automation was happening ?
I don't think LAN Automation creates a DHCP pool, it used the pool create by you for LAN automation and reserved under site where you are doing LAN automation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-26-2018 11:20 PM
Hi ammahend
Thanks for youre reply. Below i pasted the configuration wich was greated throug my DNAC Appliance.
I connected the new Switches directly to my Fabric Boarder Switch throug a one Gig Copper Interface.
Here you can see that LAN-Automation created a DHCP Pool:
ip dhcp pool nw_orchestration_pool
network 10.129.1.0 255.255.255.192
option 43 ascii 5A1D;B2;K4;I172.16.255.40;J80;
default-router 10.129.1.1
DNAC created the following Interfaces:
interface Loopback60000
ip address 10.129.1.65 255.255.255.255
ip pim sparse-mode
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
no ip address
speed 1000
negotiation auto
Following the configuration of the interface to my Edge Switch:
interface GigabitEthernet1/0/1
switchport mode access
!
Then there is the following configuration int Vlan 1:
interface Vlan1
ip address 10.129.1.1 255.255.255.192
bfd interval 500 min_rx 500 multiplier 3
no bfd echo
clns mtu 1400
and finaly the isis configuration:
router isis
net 49.0000.0101.2925.5255.00
domain-password cisco
metric-style wide
log-adjacency-changes
nsf ietf
passive-interface Loopback0
default-information originate
bfd all-interfaces
I will check my Edge Switches vor some Logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2018 01:07 AM
*Dec 26 02:17:19.980: %PNPA-DHCP Op-43 Msg: _pdoop.18.ztp=[pnp-zero-touch] host=[] ipad=[172.16.255.40] port=80
*Dec 26 02:17:19.980: %PNPA-DHCP Op-43 Msg: _pors.done=1
*Dec 26 02:17:19.980: %PNPA-DHCP Op-43 Msg: _pdokp.18.kil=[PNPA_DHCP_OP43] pid=285 idn=[Vlan1]
*Dec 26 02:17:19.980: XML-UPDOWN: Vlan1 XML Interface(102) SHUTDOWN(101). PID=285
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: Op43 has 5A. It is for PnP
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: After stripping extra characters in front of 5A, if any: 5A1D;B2;K4;I172.16.255.40;J80; op43_len: 30
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdoon.19.ina=[Vlan1]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _papdo.19.cot=[5A1D;B2;K4;I172.16.255.40;J80;] lot=[5A1D;B2;K4;I172.16.255.40;J80;]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: Process state = READY
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: OK to process message
*Dec 26 14:17:25.003: XML-UPDOWN: PNPA_DHCP_OP43 XML Interface(102) UP. PID=285
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdoon.19.ntf.don=285
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdoop.19.org=[A1D;B2;K4;I172.16.255.40;J80;]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdgfa.19.inp=[B2;K4;I172.16.255.40;J80;]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdgfa.19.B2.s12=[ ipv4 ]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdgfa.19.K4.htp=[ transport http ]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdgfa.19.Ix.srv.ip.rm=[ 172.16.255.40 ]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdgfa.19.Jx.srv.rt.rm=[ port 80 ]
*Dec 26 14:17:25.003: %PNPA-DHCP Op-43 Msg: _pdoop.19.ztp=[pnp-zero-touch] host=[] ipad=[172.16.255.40] port=80
*Dec 26 14:17:25.004: %PNPA-DHCP Op-43 Msg: _pors.done=1
*Dec 26 14:17:25.004: %PNPA-DHCP Op-43 Msg: _pdokp.19.kil=[PNPA_DHCP_OP43] pid=285 idn=[Vlan1]
*Dec 26 14:17:25.004: XML-UPDOWN: Vlan1 XML Interface(102) SHUTDOWN(101). PID=285
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: Op43 has 5A. It is for PnP
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: After stripping extra characters in front of 5A, if any: 5A1D;B2;K4;I172.16.255.40;J80; op43_len: 30
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: _pdoon.20.ina=[Vlan1]
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: _papdo.20.cot=[5A1D;B2;K4;I172.16.255.40;J80;] lot=[5A1D;B2;K4;I172.16.255.40;J80;]
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: Process state = READY
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: OK to process message
*Dec 27 02:17:30.036: XML-UPDOWN: PNPA_DHCP_OP43 XML Interface(102) UP. PID=285
*Dec 27 02:17:30.036: %PNPA-DHCP Op-43 Msg: _pdoon.20.ntf.don=285
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdoop.20.org=[A1D;B2;K4;I172.16.255.40;J80;]
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdgfa.20.inp=[B2;K4;I172.16.255.40;J80;]
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdgfa.20.B2.s12=[ ipv4 ]
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdgfa.20.K4.htp=[ transport http ]
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdgfa.20.Ix.srv.ip.rm=[ 172.16.255.40 ]
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdgfa.20.Jx.srv.rt.rm=[ port 80 ]
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdoop.20.ztp=[pnp-zero-touch] host=[] ipad=[172.16.255.40] port=80
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pors.done=1
*Dec 27 02:17:30.037: %PNPA-DHCP Op-43 Msg: _pdokp.20.kil=[PNPA_DHCP_OP43] pid=285 idn=[Vlan1]
*Dec 27 02:17:30.037: XML-UPDOWN: Vlan1 XML Interface(102) SHUTDOWN(101). PID=285
*Dec 27 09:05:48.313: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named TP-self-signed-245487054 has been generated or imported by crypto-engine
*Dec 27 09:05:48.314: %SSH-5-ENABLED: SSH 1.99 has been enabled
*Dec 27 09:05:48.355: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
*Dec 27 09:05:48.411: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named TP-self-signed-245487054.server has been generated or imported by crypto-engine
*Dec 27 09:05:48.621: %AN-6-AN_ABORTED_BY_CONSOLE_INPUT: Autonomic disabled due to User intervention on console. configure 'autonomic' to enable it.
Switch#
*Dec 27 09:06:12.411: %PNP-6-PNP_DISCOVERY_STOPPED: PnP Discovery stopped (Config Wizard)
Following the output form sh run brief:
version 16.10
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
! Call-home is enabled by Smart-Licensing.
service call-home
no platform punt-keepalive disable-kernel-core
!
hostname Switch
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
!
no aaa new-model
switch 1 provision c9300-48p
!
!
!
!
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
!
!
!
!
!
!
!
!
login on-success log
!
!
!
!
!
!
!
no device-tracking logging theft
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
crypto pki trustpoint TP-self-signed-245487054
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-245487054
revocation-check none
rsakeypair TP-self-signed-245487054
!
!
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
crypto pki certificate chain TP-self-signed-245487054
certificate self-signed 01
!
license boot level network-advantage addon dna-advantage
!
!
diagnostic bootup level minimal
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
redundancy
mode sso
!
!
!
!
!
!
class-map match-any system-cpp-police-ewlc-control
description EWLC Control
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data packets, LOGGING, Transit Traffic
class-map match-any system-cpp-default
description EWLC Data, Inter FED Traffic
class-map match-any system-cpp-police-sys-data
description Openflow, Exception, EGR Exception, NFL Sampled Data, RPF Failed
class-map match-any system-cpp-police-punt-webauth
description Punt Webauth
class-map match-any system-cpp-police-l2lvx-control
description L2 LVX control packets
class-map match-any system-cpp-police-forus
description Forus Address resolution and Forus traffic
class-map match-any system-cpp-police-multicast-end-station
description MCAST END STATION
class-map match-any system-cpp-police-high-rate-app
description High Rate Applications
class-map match-any system-cpp-police-multicast
description MCAST Data
class-map match-any system-cpp-police-l2-control
description L2 control
class-map match-any system-cpp-police-dot1x-auth
description DOT1X Auth
class-map match-any system-cpp-police-data
description ICMP redirect, ICMP_GEN and BROADCAST
class-map match-any system-cpp-police-stackwise-virt-control
description Stackwise Virtual OOB
class-map match-any non-client-nrt-class
class-map match-any system-cpp-police-routing-control
description Routing control and Low Latency
class-map match-any system-cpp-police-protocol-snooping
description Protocol snooping
class-map match-any system-cpp-police-dhcp-snooping
description DHCP snooping
class-map match-any system-cpp-police-ios-routing
description L2 control, Topology control, Routing control, Low Latency
class-map match-any system-cpp-police-system-critical
description System Critical and Gold Pkt
class-map match-any system-cpp-police-ios-feature
description ICMPGEN,BROADCAST,ICMP,L2LVXCntrl,ProtoSnoop,PuntWebauth,MCASTData,Transit,DOT1XAuth,Swfwd,LOGGING,L2LVXData,ForusTraffic,ForusARP,McastEndStn,Openflow,Exception,EGRExcption,NflSampled,RpfFailed
!
policy-map system-cpp-policy
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
no ip address
speed 1000
negotiation auto
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
!
interface GigabitEthernet1/0/6
!
interface GigabitEthernet1/0/7
!
interface GigabitEthernet1/0/8
!
interface GigabitEthernet1/0/9
!
interface GigabitEthernet1/0/10
!
interface GigabitEthernet1/0/11
!
interface GigabitEthernet1/0/12
!
interface GigabitEthernet1/0/13
!
interface GigabitEthernet1/0/14
!
interface GigabitEthernet1/0/15
!
interface GigabitEthernet1/0/16
!
interface GigabitEthernet1/0/17
!
interface GigabitEthernet1/0/18
!
interface GigabitEthernet1/0/19
!
interface GigabitEthernet1/0/20
!
interface GigabitEthernet1/0/21
!
interface GigabitEthernet1/0/22
!
interface GigabitEthernet1/0/23
!
interface GigabitEthernet1/0/24
!
interface GigabitEthernet1/0/25
!
interface GigabitEthernet1/0/26
!
interface GigabitEthernet1/0/27
!
interface GigabitEthernet1/0/28
!
interface GigabitEthernet1/0/29
!
interface GigabitEthernet1/0/30
!
interface GigabitEthernet1/0/31
!
interface GigabitEthernet1/0/32
!
interface GigabitEthernet1/0/33
!
interface GigabitEthernet1/0/34
!
interface GigabitEthernet1/0/35
!
interface GigabitEthernet1/0/36
!
interface GigabitEthernet1/0/37
!
interface GigabitEthernet1/0/38
!
interface GigabitEthernet1/0/39
!
interface GigabitEthernet1/0/40
!
interface GigabitEthernet1/0/41
!
interface GigabitEthernet1/0/42
!
interface GigabitEthernet1/0/43
!
interface GigabitEthernet1/0/44
!
interface GigabitEthernet1/0/45
!
interface GigabitEthernet1/0/46
!
interface GigabitEthernet1/0/47
!
interface GigabitEthernet1/0/48
!
interface GigabitEthernet1/1/1
!
interface GigabitEthernet1/1/2
!
interface GigabitEthernet1/1/3
!
interface GigabitEthernet1/1/4
!
interface TenGigabitEthernet1/1/1
!
interface TenGigabitEthernet1/1/2
!
interface TenGigabitEthernet1/1/3
!
interface TenGigabitEthernet1/1/4
!
interface TenGigabitEthernet1/1/5
!
interface TenGigabitEthernet1/1/6
!
interface TenGigabitEthernet1/1/7
!
interface TenGigabitEthernet1/1/8
!
interface FortyGigabitEthernet1/1/1
!
interface FortyGigabitEthernet1/1/2
!
interface TwentyFiveGigE1/1/1
!
interface TwentyFiveGigE1/1/2
!
interface Vlan1
ip address dhcp
!
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip http client source-interface Vlan1
!
!
!
!
!
!
control-plane
service-policy input system-cpp-policy
!
!
line con 0
stopbits 1
line vty 0 4
login
line vty 5 15
login
!
!
mac address-table notification mac-move
!
!
!
!
!
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2018 01:08 PM
seems like it was running ok, until you did show run, when the discovery stopped, i can be wrong, I am enclosing the logs from my testing, to show you how the expected behavior should be.
in some cases I have seen it take as long as 30 minutes for the automation to finish, after which you will have to manually stop discovery from DNAC for the LAN automation to complete and push some last configs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-29-2018 01:08 PM
seems like it was running ok, until you did show run, when the discovery stopped, i can be wrong, I am enclosing the logs from my testing, to show you how the expected behavior should be.
in some cases I have seen it take as long as 30 minutes for the automation to finish, after which you will have to manually stop discovery from DNAC for the LAN automation to complete and push some last configs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-30-2019 10:57 AM
check the connectivity between the DNA and the EDGE switch.
if you are using DNA connect to the fusion or in DC, advertise the subnet used for LAN automation in BGP prior to starting the automation from the border.
you can use one last ip from that LAN automation subnet and create a loopback interface (temp, can be delated later) and advertise the subnet in BGP,
check by pinging the temp loopback before LAN automation from the DNAC connected network
AMK
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide