- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Applications
- Re: proximity sessionid hijacking
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
proximity sessionid hijacking
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2019 10:42 PM
Hi all,
I am willing to deploy proximity feature to all VC endpoints.
To analysis that in security, I used Burp Suite and faced sessionid is constant for 5 minutes.
if an attacker get this id, what would he do?
When I search on Google, there are some docs related with security issues but no answer for my question.
May I take your suggestions?
Thank you.
- Labels:
-
Other Collaboration Applications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2019 11:12 PM
Hi there
Does this help you?
How Cisco Proximity Works
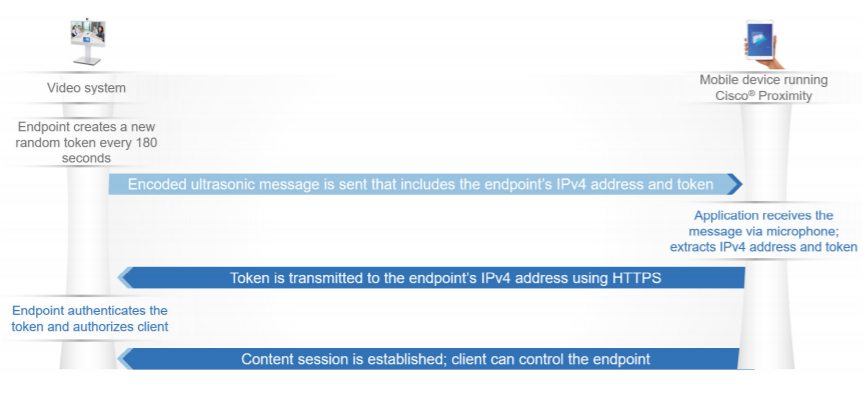
When the Intelligent Proximity services are enabled on a video endpoint, an inaudible ultrasonic sound token will be played through the video system loudspeakers. The Cisco Proximity client application running on the mobile device will record this token through its integrated microphone. The token contains information on how to connect to the video system over the
network.
The mobile device will decode the token and try to establish a secure connection to the video system. To establish the connection, the mobile device needs to be able to reach the IPv4 address of the video system in the room on port 443 (HTTPS).
Hope this Helps
Cheers
Rath!
***Please rate helpful posts***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2019 04:23 AM
Hi Ratheesh,
Thanks for your reply. I followed that guide at the beginning.
But there is no answer for my question.
Yes there is secure connection but session-id is clear and sniffable by Burp.
What would happen if an attacker got that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2019 11:54 AM
Your concern seems predicated on your LAN/WLAN connection being compromised. TBH, this doesn’t strike me as the real concern: if your network traffic is being intercepted you have bigger problems than Proximity.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide