Introduction
All MPP phones have a Cisco signed client certificate, but they might vary depending on firmware and/or hardware version. The quickest way of establishing which client certificate the phone is using, is to enable HTTPS and check what SSL certificate the phone is presenting.
Enable HTTPS
- Login to http://IP_ADDRESS_PHONE/admin/advanced
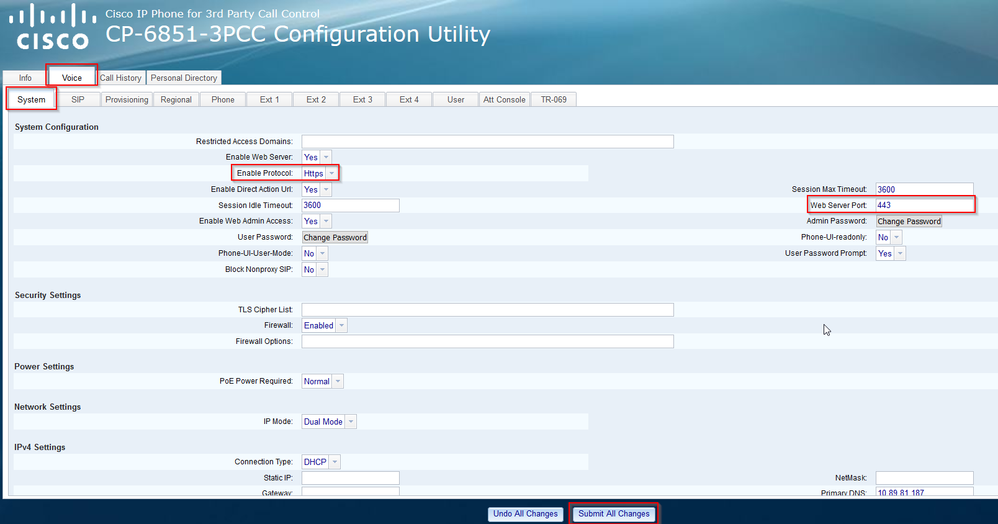
- Navigate to Voice --> System
- Set “Enable Protocol” to “HTTPS
- Change the Web Server Port number (on this case we are using the default HTTPS 443 port) – Note: by changing the protocol to HTTPS, the phone will not change to port 443 automatically, you can to change it manually
- Click on Submit All Changes
Check Client Certificate in Firefox
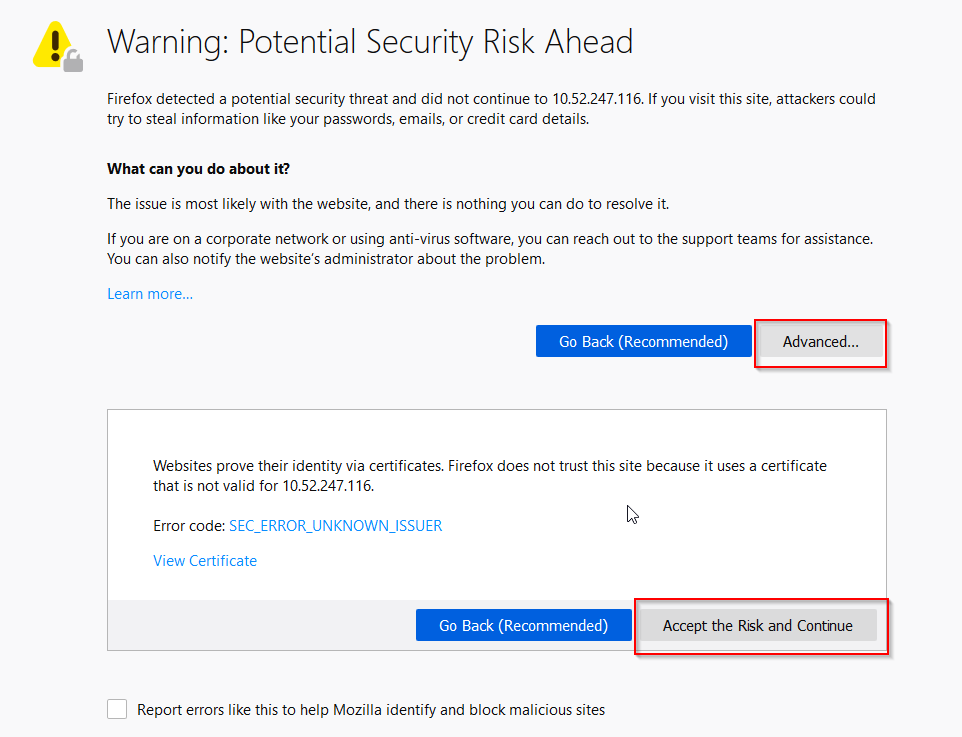
- Login to https://IP_ADDRESS_PHONE/admin/advanced
- Firefox will give you a security warning.
- Click on “Advanced” and “Accept the Risk and Continue”
-
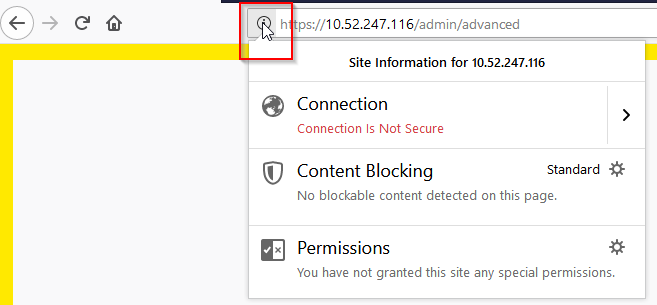
- Click on “Show Site Information"
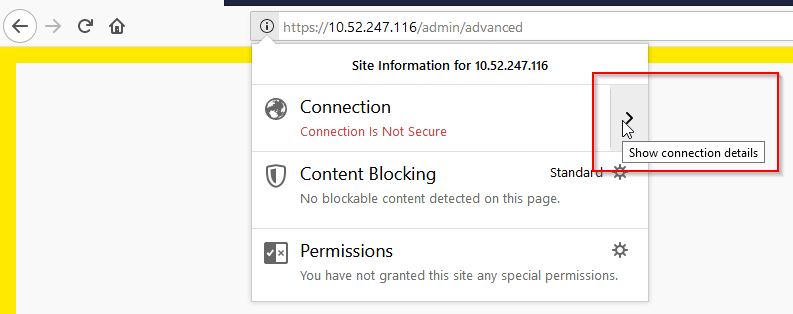
- Click on “Show Connection Details”
- Click on “More Information”
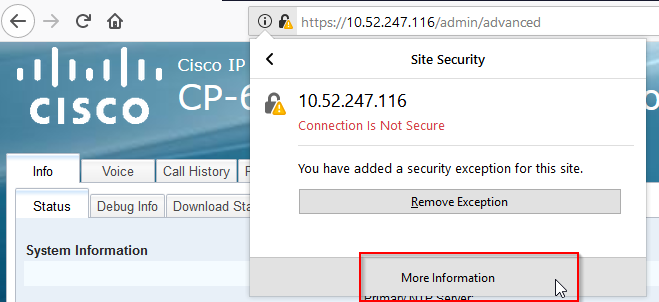
- Click on “View Certificate”
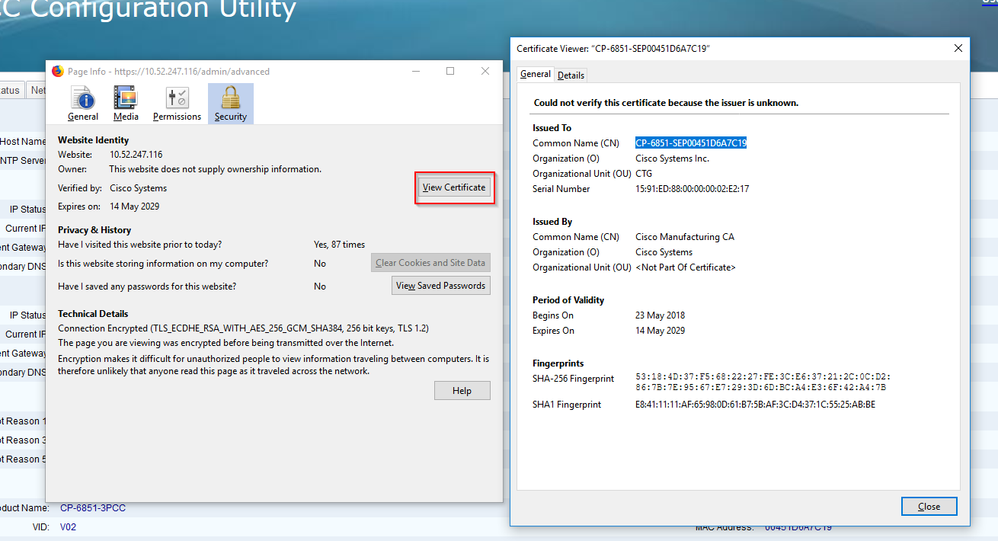
Check Client Certificate in Chrome
- Login to https://IP_ADDRESS_PHONE/admin/advanced
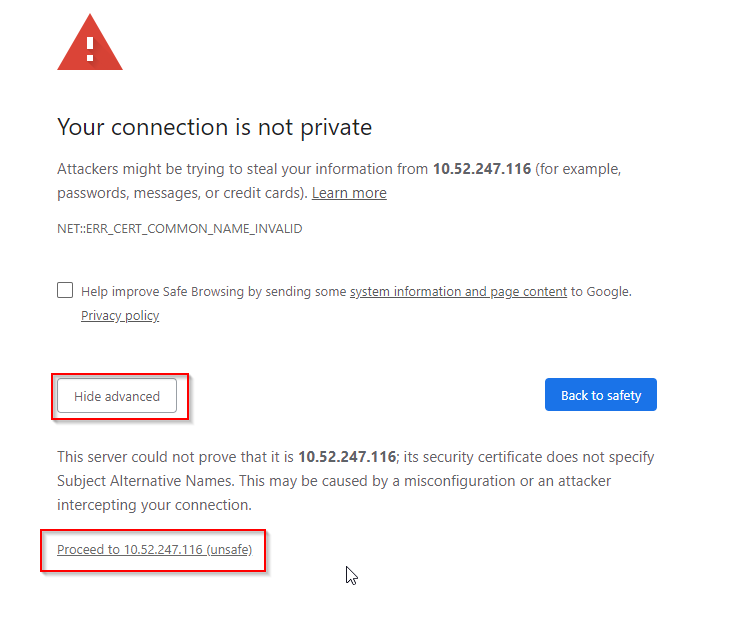
- Chrome will give you a security warning
- Click on “Advanced” and “Proceed”
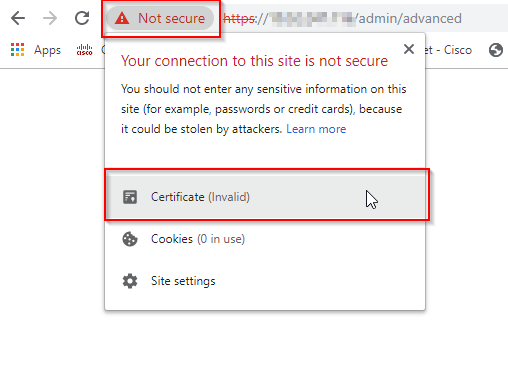
- Click on “Not secure” followed by “Certificate”
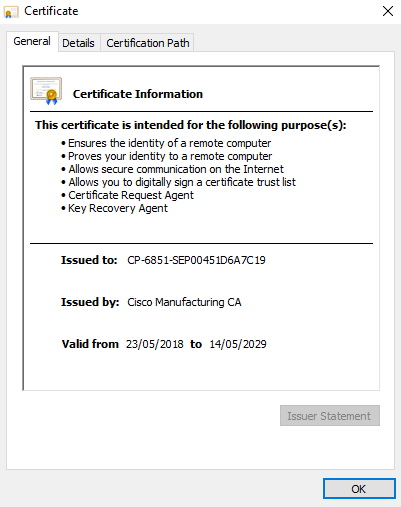
All Cisco root and subordinate certificates can be found at the following URL:
https://www.cisco.com/security/pki/
If web access is not available for any reason, use openssl (s_client -connect) to connect to the phone in order to check the issuer of the phone certificate which will be a subordinate certificate which will correspond to an entry on the PKI site, and to also check the issuer of the subordiniate certificate, which will again be another Cisco certificate on the PKI site.
If the issuer of the subordinate certificate does not appear using the s_client command, then again use openssl (x509 -in [cert_name] -text -noout) to analyse the downloaded subordinate certificate in order to find out which root certificate issued the subordinate certificate. Again, the root certificate will correspond to an entry on the PKI site.