- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center and Cloud Knowledge Base
- Cisco ACI Ask the Experts FAQ: Operations and Component Integration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
06-02-2021
06:39 PM
- edited on
02-15-2023
08:02 PM
by
Vivien Chia
![]()
Contents
- How does ACI optimize flooding?
- What is the difference between Cisco ACI Long and Short lived releases?
- What are Cisco ACI options to implement DevOps Model?
- How Cisco ACI supports ITSM/ITOM scenarios for modern IT Business?
- What is Cisco Nexus Dashboard?
- How does a bad Leaf or Spine impact the overall System health Score of the ACI Fabric?
- If we have a faulty part on a Leaf which is having planned replacement, how can we reduce the its impact to overall System Health to avoid false positive?
- What are the SNMP functions supported by Cisco Application Centric Infrastructure (ACI)?
- What are vzAny Contracts?
Here are some commonly asked questions and answers to help you with the operations and component integration for Cisco Application Centric Infrastructure (ACI). Subscribe (how-to) to this post to stay up-to-date with the latest Q&A and recommended Ask the Experts (ATXs) sessions to attend.
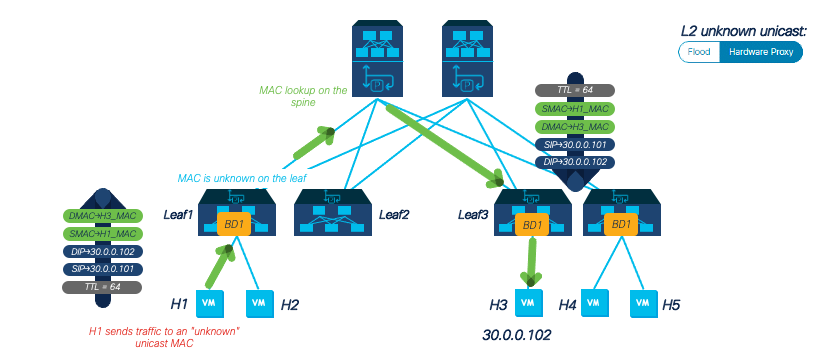
How does ACI optimize flooding?
Recommended ATXs: Installation/Implementation Best Practices: Cisco ACI
What is the difference between Cisco ACI Long and Short lived releases?
A. About Long-Lived Releases: Cisco ACI long-lived releases are software releases intended to help you stay on a given release on a long-term basis (up to approximately 18 months), while benefiting from frequent maintenance drops to ensure quality and stability. Cisco may support two long-lived releases at any given point of time.| Long-Lived Cisco APIC Release Version | Long-Lived Cisco Switch Release Version |
| 5.2(x) | 15.2(x) |
| 4.2(x) | 14.2(x) |
| 3.2(x) | 13.2(x) |
| 2.2(x) | 12.2(x) |
About Short-Lived Releases: Cisco ACI short-lived releases are stable, quality releases delivered for new feature functionalities. These releases have limited maintenance support for a duration of six months after the initial release, after which there will be no active maintenance. In addition, these releases will not have an EOS announcement. Refer to Cisco APIC Installation and ACI Upgrade and Downgrade Guide for further details in ACI upgrade mechanism.
Recommended ATXs: Upgrade Planning & Best Practices: Cisco ACI
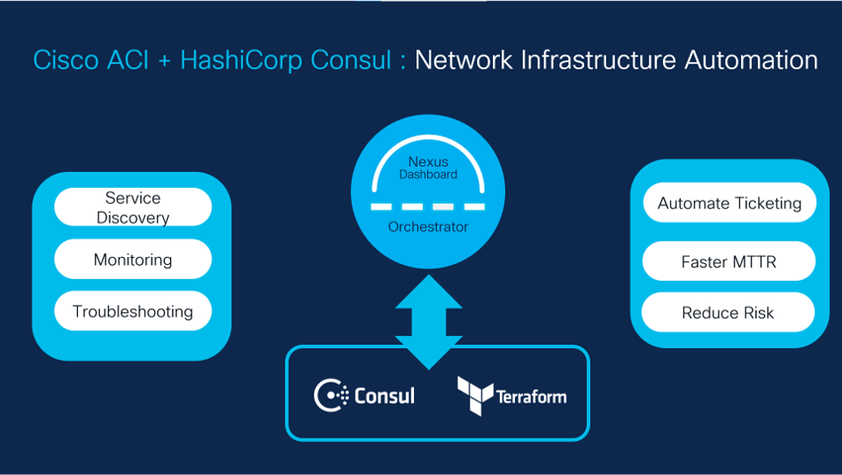
What are Cisco ACI options to implement DevOps Model?
A. Cisco introduced a slew of cloud-native network automation solutions jointly with HashiCorp Terraform and RedHat Ansible. These solutions help customers embrace a DevOps software model and leverage the infrastructure platform in a self-service manner by automating their networks with declarative abstractions.
Cisco ACI – HashiCorp Consul integration:
Achieve service-driven network infrastructure automation with visibility and insights. Cisco ACI, HashiCorp Consul, Terraform, and Consul-Terraform-Sync (CTS) work together to provide end-to-end application infrastructure orchestration. The Consul ACI App provides real-time visibility across the network and application services and makes it easy to diagnose application issues and resolve network outages. The integration allows operators to see which services are running on each ACI endpoint by mapping service-mesh abstractions to intent-based networking abstractions.
Refer to Cisco ACI and HashiCorp Terraform Joint Innovations Introduce Cloud-native Network Automation for more details.
Recommended ATXs: Getting Started ACI and Multi Site Orchestrator Automation with Terraform
How Cisco ACI supports ITSM/ITOM scenarios for modern IT Business?
A. Cisco ACI integration with ServiceNow automates the discovery, application to business service mapping, firmware management, and provisioning of the Cisco ACI fabric from the ServiceNow instance.- Faster troubleshooting and root-cause analysis
- Improved operational efficiency
- Reduced TCO
What is Cisco Nexus Dashboard?
A. Cisco Nexus Dashboard provides a single automation platform to access operational services and tools for the data center and network. Using the Cisco Nexus Dashboard platform, customers can deploy Cisco Nexus Dashboard Orchestrator (NDO), Cisco Nexus Dashboard Insights, and Cisco Nexus Dashboard Data Broker. Reference: Cisco Nexus Dashboard Data Sheet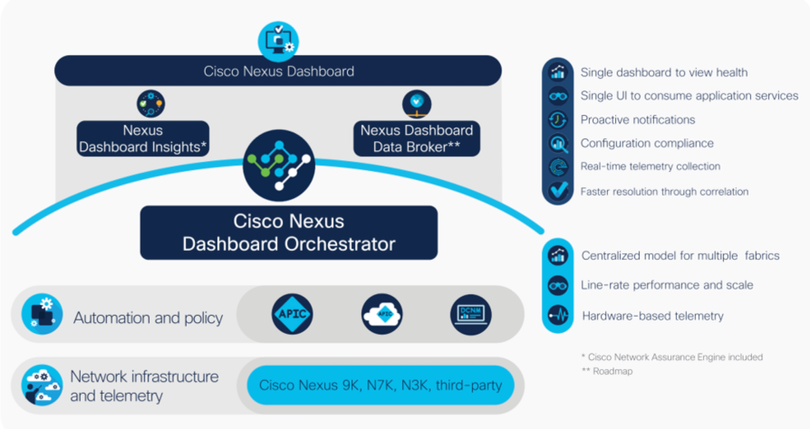
-
Cisco Nexus Dashboard Orchestrator (formerly Cisco Multi-Site Orchestrator) allows operators to push policies and templates and set up intersite connectivity at scale. Besides delivering high-level policies to the local data center controller — also referred to as the domain controller — it enables separation of fault domains, federation of data-center and cloud networks, and business resiliency at a global scale.
-
Cisco Nexus Dashboard Insights (formerly Nexus Insights) allows operators to consume the entire insights and assurance stack as a unified offering but also to take advantage of the integrated services to set up automated workflows such as upgrade assist and automated Splunk SIEM integration.
-
Cisco Nexus Dashboard Data Broker (formerly Nexus Data Broker) is now a part of Cisco Nexus Dashboard, which provides pervasive packet and network visibility for NetOps and SecOps to programmatically manage aggregating, filtering, and forwarding complete workflows to custom analytics tools..
-
Third-party applications: Cisco Nexus Dashboard offers a rich suite of services for third-party developers to build applications. REST APIs allow third-party tools to authenticate and integrate with key services such as Nexus Dashboard Insights and Nexus Dashboard Orchestrator. Currently supported third-party integrations in the Nexus Dashboard ecosystem include ServiceNow ITSM/ITOM, Splunk SIEM, HashiCorp Terraform,[1] and RedHat Ansible.
-
Cisco Nexus Dashboard Fabric Controller: Cisco Nexus Dashboard can also host Cisco NDFC similar to the hosting of operational services. This unified capability gives customers a single touch point on their journey from installation to operations.
Recommended ATXs: Product Overview & Business Value: Cisco Nexus Dashboard
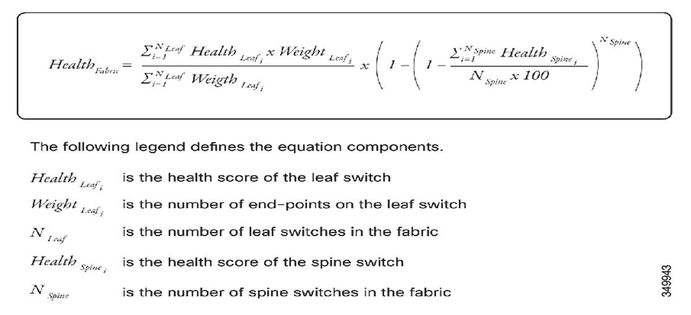
How does a bad Leaf or Spine impact the overall System health Score of the ACI Fabric?
A. The health score is applied on many different objects in the ACI model. Higher level objects scores depend on the score of objects that higher level depend on. So the overall System health score is calculated from the score of the leaf and spines with respect to below formula:
Recommended ATXs: Monitoring Best Practices: Cisco ACI
If we have a faulty part on a Leaf which is having planned replacement, how can we reduce the its impact to overall System Health to avoid false positive?
A. Each health score category is assigned an impact level. The five health score impact levels are Maximum, High, Medium, Low, and None.
The following factors are the various impact levels:
Maximum: 100% High: 80% Medium: 50% Low: 20% None: 0%
As you already have a planned maintenance for the PSU or any other component, in APIC GUI Got to Fabric >> Inventory >> Impacted Device >> Health >> Right Click the child component and “Update Health Score Impact Policy”.
Recommended ATXs: Monitoring Best Practices: Cisco ACI
What are the SNMP functions supported by Cisco Application Centric Infrastructure (ACI)?
A. The Cisco Application Centric Infrastructure (ACI) supports the following SNMP functions:
- SNMP read queries (Get, Next, Bulk, Walk) are supported by leaf and spine switches and by APIC.
- SNMP write commands (Set) are not supported by leaf and spine switches or by APIC.
- SNMP traps (v1, v2c, and v3) are supported by leaf and spine switches and by APIC.
NOTE: ACI supports a maximum of 10 trap receivers. -
SNMPv3 is supported by leaf and spine switches and by APIC.
For further information regarding supported MIBs: ACI MIB Support List
Recommended ATXs: Monitoring Best Practices: Cisco ACI
What are vzAny Contracts?
A. vzAny is an ”EPG Collection” that is defined under a given VRF. vzAny represents all EPGs, including the L3Out EPG in the VRF. The typical usage of vzAny is to allow flows between one EPG and all the other EPGs within the VRF through one contract connection instead of having multiple consumer or provider EPGs. The use of vzAny helps to simplify the configuration and to reduce policy TCAM consumption.
Recommended ATXs: Feature Overview: Security and Segmentation for Cisco ACI using ACI Virtual Edge
|
Need more resources? Access the latest guides, recordings, other FAQs and more via Cisco ACI ATXs Resources. Want to learn more and get real-time Cisco expert advice? Through live Q&A and solution demos, Ask the Experts (ATXs) real-time sessions help you tackle deployment hurdles and learn advanced tips to maximize your use of Cisco technology. View and register for the upcoming Ask the Experts (ATXs) sessions today. [Pro tip: Subscribe to the event listing for new session updates.] |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi All,
Is today Sandboxapicdc down or malfunctioning cause not accepting credentials
Regards,
Vishal
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: