- Cisco Community
- Technology and Support
- Data Center and Cloud
- Data Center Switches
- Re: Portchannel from Nexus 5672UP to C6807-XL VSS suspend
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2019 06:33 AM
Hello,
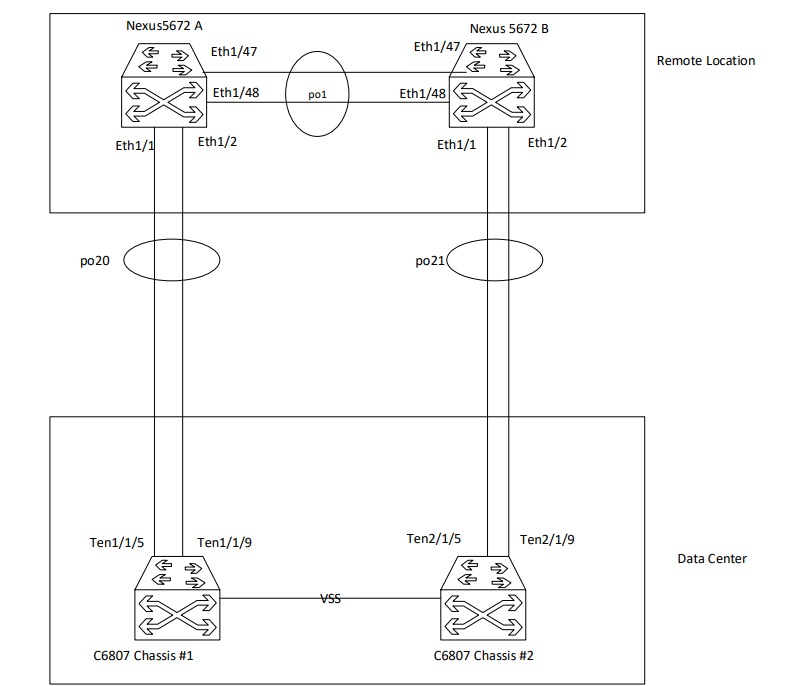
we've a remote location with 2 Nexus 5672 connected via dark fiber to our core C6807-XL as VSS.
If I connect 2 x 10Gig over the same Fiber to the same Chassis of the VSS, the connection (LACP) is fine, but if I connect crosswise (Nexus A eth1/1 to VSS Ten1/1/1 and Nexus A eth1/2 to VSS Ten2/1/1) for redundancy, the Interface eth1/2 on Nexus A goes to suspend.
On Interface-Stats there are no errors.
the Log before this happens:
2019 Dec 16 11:34:18 swi-stu2-brz-20 %ETHPORT-5-SPEED: Interface Ethernet1/2, operational speed changed to 10 Gbps 2019 Dec 16 11:34:18 swi-stu2-brz-20 %ETHPORT-5-IF_DUPLEX: Interface Ethernet1/2, operational duplex mode changed to Full 2019 Dec 16 11:34:18 swi-stu2-brz-20 %ETHPORT-5-IF_RX_FLOW_CONTROL: Interface Ethernet1/2, operational Receive Flow Control state changed to off 2019 Dec 16 11:34:18 swi-stu2-brz-20 %ETHPORT-5-IF_TX_FLOW_CONTROL: Interface Ethernet1/2, operational Transmit Flow Control state changed to off 2019 Dec 16 11:34:23 swi-stu2-brz-20 %ETH_PORT_CHANNEL-5-PORT_SUSPENDED: Ethernet1/2: Ethernet1/2 is suspended
I've nothing configured with Flow-Control so should be default.
any Idea's
Solved! Go to Solution.
- Labels:
-
Nexus Series Switches
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2019 05:11 AM - edited 12-17-2019 05:12 AM
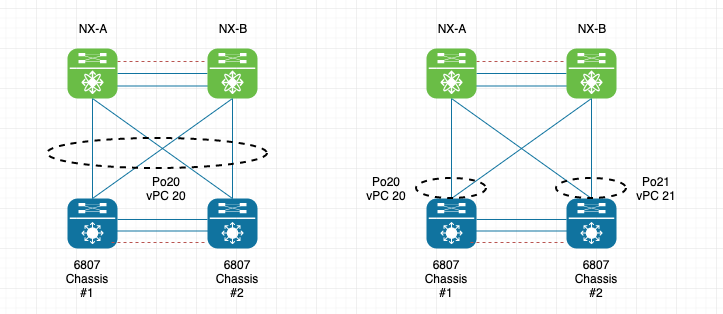
Looks like you're missing the appropriate "vpc X" configuration under Po20/Po21 from the Nexus perspective.
Which one of the two designs below are you trying to achieve (the one on the left would generally be considered best practice since the vPC pair will appear as a single MEC to the VSS pair):
Essentially, to achieve the design on the left, you would place all the interfaces from both the VSS pair and the Nexus pair in Po20, and under Po20 on the Nexus switches, you issue "vpc 20". If this is a production environment, you'd need a window to execute this change as this will be highly disruptive.
If you're trying to achieve the design on the right, then you will have two separate port-channels and two separate vPCs. The config here should be intuitive as well but Im happy to help if it isn't clear. Same caveat as far as scheduling a window for this applies.
P.S: See attached vPC/VSS best practices document for detailed information.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2019 12:56 PM
Can you share a basic diagram of the two Nexus devices along with the VSS Catalyst pair and labeled interfaces of how they are cross-connected?
Then share the following (put it back in the 'broken' state):
show run int ex/y < or gx/x.. For both the Nexus and Catalyst show run int PoX < Where X is the port-channel(s) b/w the devices show vpc show port-channel summary < On NX-OS show etherchannel summary < On IOS show lacp counters
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2019 11:55 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2019 05:11 AM - edited 12-17-2019 05:12 AM
Looks like you're missing the appropriate "vpc X" configuration under Po20/Po21 from the Nexus perspective.
Which one of the two designs below are you trying to achieve (the one on the left would generally be considered best practice since the vPC pair will appear as a single MEC to the VSS pair):
Essentially, to achieve the design on the left, you would place all the interfaces from both the VSS pair and the Nexus pair in Po20, and under Po20 on the Nexus switches, you issue "vpc 20". If this is a production environment, you'd need a window to execute this change as this will be highly disruptive.
If you're trying to achieve the design on the right, then you will have two separate port-channels and two separate vPCs. The config here should be intuitive as well but Im happy to help if it isn't clear. Same caveat as far as scheduling a window for this applies.
P.S: See attached vPC/VSS best practices document for detailed information.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2019 05:36 AM
hello Andrea,
thank's very much.
I planned for the Scenario on the right, but when I configured po20 with vpc 20 I got under "show vpc" the error, that the endpoints of the members are on different devices (don't know exactly the message), so I removed the vpc-config.
So I think I've got to configure an MEC on the VSS, never heard about, so I will read the docs.
thank you and a fine christmas
Karl
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide