- Cisco Community
- Technology and Support
- Collaboration
- IP Telephony and Phones
- Re: CAPF Certificate Signing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2018 12:32 AM - edited 03-17-2019 01:39 PM
Hello All,
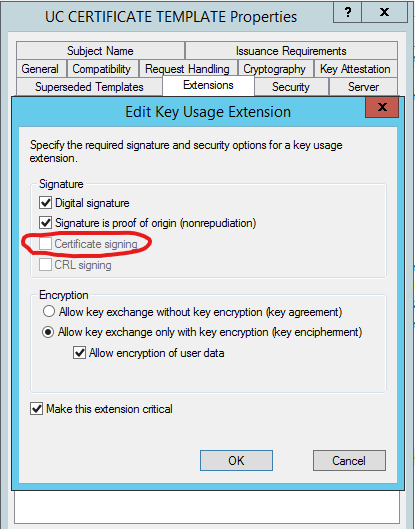
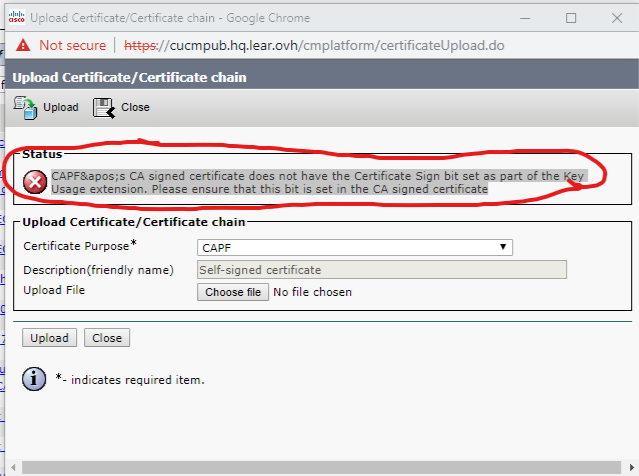
This morning I am have signed my CAPF certificate with Root CA but I am unable to upload to CUCM as the Certificate Signing bit is not checked.
Does anybody know how I can activate this option on my certificate template in windows 2012 R2, at the moment its greyed out and I am unable to check the box ?
Any help would be appreciated :)
Thanks,
Mathew
Solved! Go to Solution.
- Labels:
-
Other IP Telephony
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2018 12:05 AM
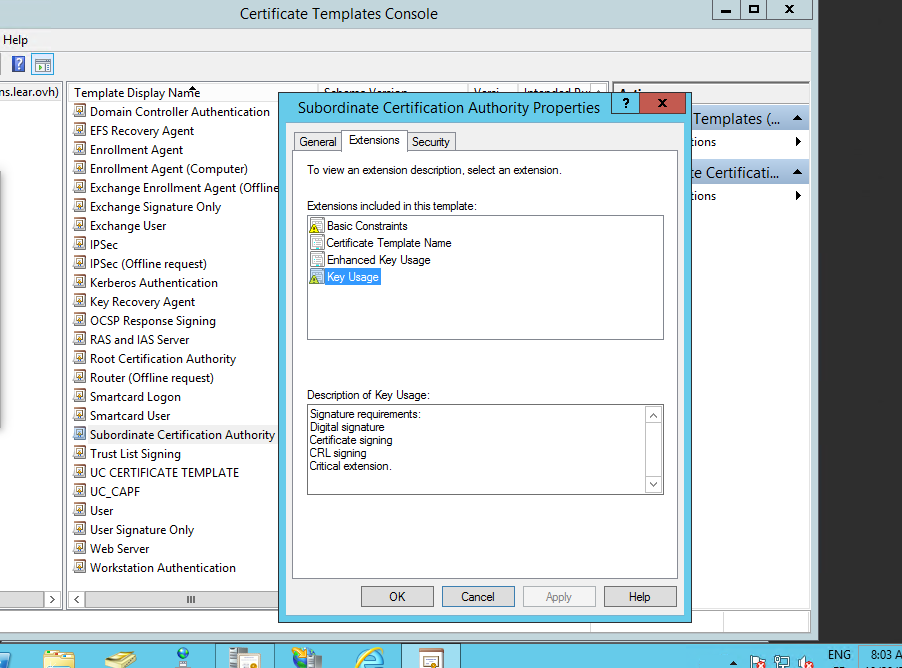
After testing I am able to succesfully sign CAPF and upload to call manager using this certificate template in Windows Server 2012 R2 :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2018 12:54 AM
I think I found it, it seems that the template needed is the "Subordinate Certification Authority".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2018 05:24 AM
thanks for the update Matt, maybe add a screenshot of how you did this for future reference
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2018 12:05 AM
After testing I am able to succesfully sign CAPF and upload to call manager using this certificate template in Windows Server 2012 R2 :

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-28-2018 08:24 AM
If you’re able to share, what was the compelling reason to CA-sign CAPF?
There are ongoing discussions about future design enhancements to CAPF so I would like to cite real-world use cases. The only reason I have seen is for 802.1x certificate-based authentication to AAA/ISE but most customers prefer to install/trust the CAPF certificate on AAA/ISE instead.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2018 09:56 AM - edited 10-29-2018 09:57 AM
Hello Jonathan,
This is my ccnp lab (not production), I signed it because the option was there to sign it.
Is there an advantage to not having a CA signed CAPF ?
Regards,
Mat
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2018 11:07 AM
Here is my "why not" answer, if this was production: On the topic of CUCM crypto-anything my advice is to not add complexity or deviate from the product default that Cisco tested unless you have to. Some of these features aren't used all that often; your chance of hitting a defect is not small. For example, phones can only store ITL/CTL files less than 64KB. The CA adds data/size to a certificate (e.g. the CA's public key signature, CRL/OCSP, etc.) when signing it.
There are other certificates (e.g. TVS or ITLrecovery) that shouldn't be CA-signed since there is never a benefit gained from doing so. Everything the CA adds to the cert can alter the way clients or the server itself handles it. For example, if it adds a CRL/OCSP URL, will clients query it? How will they react to a failure/timeout of that CRL/OCSP? I suspect the way physical phones, which themselves vary in code bases over the generations, will differ in some cases to soft clients such as Jabber. This is especially true when it comes to key/hash length/complexity.
Lastly, InfoSec may not like this from a governance perspective since CAPF lacks a certificate revocation mechanism and making it a subordinate CA extends the trust chain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2018 01:54 PM - edited 10-29-2018 01:55 PM
Many thanks for your reply Jonathan, I will keep in mind your comments when working on prod environments and share your comments with my team :)
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide