- Cisco Community
- Technology and Support
- Networking
- IPv6
- IPv4 VPN with IPv6 peers not working
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
IPv4 VPN with IPv6 peers not working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2012 06:01 AM - edited 03-01-2019 05:34 PM
Hi everybody,
I'm running a lab with GNS3 which is composed of 2 ASA's (8.4.2) and one host behind each ASA.
In this lab I want to set up a Lan-to-Lan VPN with both peer in IPv6, and internal networks still IPv4. (both peers are in dual-stack)
According to the Cisco documentation it should works :
"Specifically, the following topologies are supported when both peers are Cisco ASA 5500 series adaptive security appliances: [...]
The adaptive security appliances have IPv6 inside networks and the outside network is IPv4 (IPv6 addresses on the inside interface and IPv4 addresses on the outside interfaces)."
http://www.cisco.com/en/US/docs/security/asa/asa83/configuration/guide/site2sit.html
Here is a sample schema of the lab :
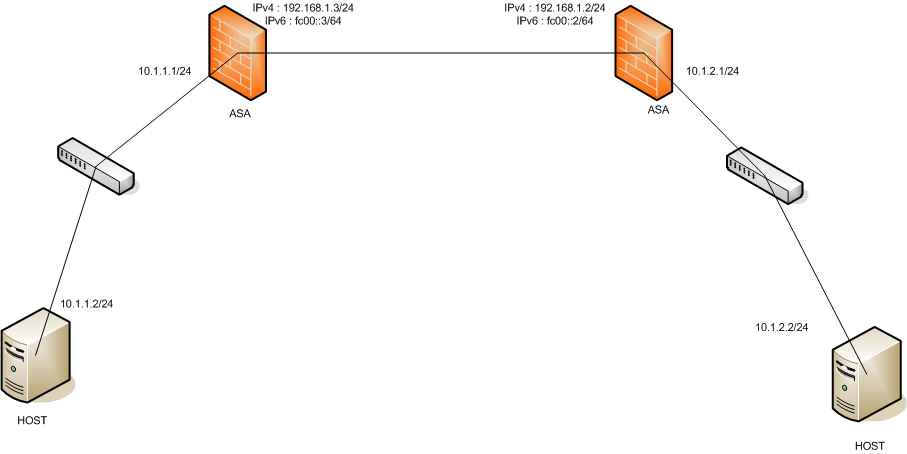
Note that I can ping both peers in IPv6 (ping fc00::2 from fc00::3 and vice-versa).
For the L2L configuration :
When I set the IPv4 address of the peer, everything works fine (both host can ping each others)
When i set the IPv6 address of the peer, the tunnel is up(there is traffic according to the VPN stats) but there is no "trace" of the traffic on the other side.
For example :
When I ping 10.1.2.2 from 10.1.1.2, I can see traffic in the tunnel (VPN stats in asdm), but the host 10.1.2.2 doesn't receive any echo request. ASA (with 10.1.1.1) doesn't see any traffic too.
Any help would be appreciated,
Thanks.
- Labels:
-
IPv6 Configuration
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2012 08:54 AM
Hi Armand Arma,
Do you simulating the
"
I'm running a lab with GNS3 which is composed of 2 ASA's (8.4.2)" in one GNS Instance..
Sorry for that question, if yes.. !
Could you describe how you done that "2 ASA´s" are running in "one GNS3 window" at same time !
Thanks
cturacci
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-12-2012 03:53 PM
It's hard to say without seeing the device configurations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2012 07:59 AM
hi Philipp,
sorry not noticed that your notification placed for the (Armand Arma).. forget my infos.. to you ;-)
Thanks
CT
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2012 01:07 PM
Here are the startup-configs of these two ASA.
cturacci : I don't understand.. Do you want to know how to run 2 ASA's at the same time with GNS 3?
: Saved
: Written by admin at 12:24:50.379 UTC Fri Apr 6 2012
!
ASA Version 8.4(2)
!
hostname ASA800A
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
description outside interface
nameif outside
security-level 0
ip address 192.168.1.3 255.255.255.0
ipv6 address fc00::3/64
ipv6 enable
ipv6 nd suppress-ra
!
interface GigabitEthernet1
description inside network
nameif inside
security-level 100
ip address 10.1.1.1 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
nameif management
security-level 0
ip address 10.10.10.3 255.255.255.0
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_access_in extended permit ip any any inactive
access-list outside_access_in extended permit ip 10.1.2.0 255.255.255.0 10.1.1.0 255.255.255.0
access-list outside_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.2.0 255.255.255.0
access-list outside_cryptomap_1 extended permit ip 10.1.1.0 255.255.255.0 10.1.2.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
ipv6 access-list outside_access_ipv6_in permit ip any any
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-645.bin
no asdm history enable
arp timeout 14400
access-group outside_access_in in interface outside
access-group outside_access_ipv6_in in interface outside
route outside 10.1.2.0 255.255.255.0 192.168.1.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 10.10.10.2 255.255.255.255 management
http redirect management 80
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto map outside_map0 1 match address outside_cryptomap_1
crypto map outside_map0 1 set pfs
crypto map outside_map0 1 set peer fc00::2
crypto map outside_map0 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map0 interface outside
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication crack
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 40
authentication crack
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 60
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 70
authentication crack
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 90
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 100
authentication crack
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 130
authentication crack
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
group-policy GroupPolicy_fc00::2 internal
group-policy GroupPolicy_fc00::2 attributes
vpn-tunnel-protocol ikev1
username admin password f3UhLvUj1QsXsuK7 encrypted privilege 15
tunnel-group fc00::2 type ipsec-l2l
tunnel-group fc00::2 general-attributes
default-group-policy GroupPolicy_fc00::2
tunnel-group fc00::2 ipsec-attributes
ikev1 pre-shared-key *****
!
!
: Saved
: Written by admin at 13:06:09.109 UTC Fri Apr 6 2012
!
ASA Version 8.4(2)
!
hostname ASA235A
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
description outside interface
nameif outside
security-level 0
ip address 192.168.1.2 255.255.255.0
ipv6 address fc00::2/64
ipv6 enable
ipv6 nd suppress-ra
!
interface GigabitEthernet1
description inside network
nameif inside
security-level 100
ip address 10.1.2.1 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
nameif management
security-level 0
ip address 10.10.10.1 255.255.255.0
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list outside_cryptomap extended permit ip 10.1.2.0 255.255.255.0 10.1.1.0 255.255.255.0
access-list outside_access_in extended permit ip any any inactive
access-list outside_access_in extended permit ip 10.1.1.0 255.255.255.0 10.1.2.0 255.255.255.0
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu management 1500
ipv6 access-list outside_access_ipv6_in permit ip any any
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-645.bin
no asdm history enable
arp timeout 14400
access-group outside_access_in in interface outside
access-group outside_access_ipv6_in in interface outside
route outside 10.1.1.0 255.255.255.0 192.168.1.3 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 10.10.10.2 255.255.255.255 management
http redirect management 80
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto map outside_map0 1 match address outside_cryptomap
crypto map outside_map0 1 set pfs
crypto map outside_map0 1 set peer fc00::3
crypto map outside_map0 1 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map0 interface outside
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication crack
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 30
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 40
authentication crack
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 60
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 70
authentication crack
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 90
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 100
authentication crack
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 120
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 130
authentication crack
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 150
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
group-policy GroupPolicy_fc00::3 internal
group-policy GroupPolicy_fc00::3 attributes
vpn-tunnel-protocol ikev1
username admin password f3UhLvUj1QsXsuK7 encrypted privilege 15
tunnel-group fc00::3 type ipsec-l2l
tunnel-group fc00::3 general-attributes
default-group-policy GroupPolicy_fc00::3
tunnel-group fc00::3 ipsec-attributes
ikev1 pre-shared-key *****
!
!
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
