- Cisco Community
- Technology and Support
- Security
- Duo Security
- Managing Users
- Re: VPN certificate authenication with ISE and Duo MFA login issues
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2024 09:53 PM - edited 03-17-2024 09:56 PM
Hi all,
I am currently in the process of implementing ASA VPN certificate authentication with Cisco ISE and DUO MFA. However, I have encountered an issue where DUO seems unable to handle authentication without a password.
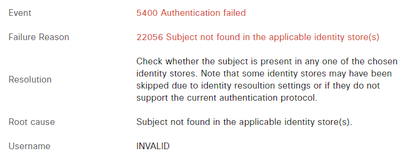
As we are using certificate authentication to identify the user instead of the traditional username and password method, DUO is unable to resolve the AD username via the DUO proxy. This results in the Cisco ISE logs showing an "INVALID username" error.
After reviewing the configuration and troubleshooting steps, it appears that DUO can not handle certificate-based RADIUS authentication. I would greatly appreciate any guidance or assistance on how to configure DUO to support this authentication method.
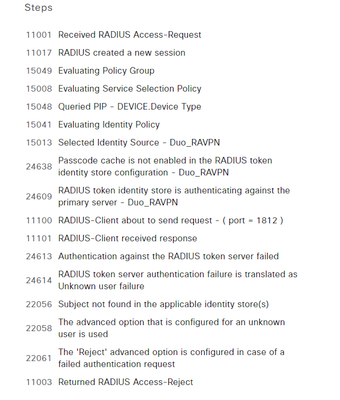
ISE logs
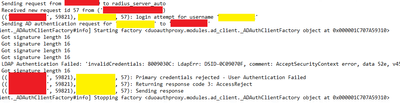
Duo Logs
Yellow = username
Red= ISE-IP
The firewall(FTD) is managed by FMC, and I was able to connect to the VPN without ISE using certificate authentication.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2024 08:07 AM - edited 03-18-2024 08:08 AM
You're right, @chocolate2395777 , Duo needs a username sent to the proxy server in the RADIUS access-request packet.
Take a look at this prior thread: https://community.cisco.com/t5/protecting-applications/anyconnect-certificate-authentication-via-ise-and-duo-proxy/m-p/4883797/highlight/true#M3545
ETA - here is another https://community.cisco.com/t5/protecting-applications/anyconnect-cert-authent-via-ise-and-duo/td-p/4883029
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2024 10:32 PM - edited 03-17-2024 10:35 PM
Hi There,
Compare the username value, as in what is ise expecting, and what is being sent from duo to authenticate. Make sure you are normalizing username in duo application. If above is true, then we may need to look at alias configuration.
Which Duo applications have username normalization enabled by default?
Duo Username Aliases Configuration Guide
Regards,
Pulkit M.
If you find this useful, please mark it helpful and accept the solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-18-2024 08:07 AM - edited 03-18-2024 08:08 AM
You're right, @chocolate2395777 , Duo needs a username sent to the proxy server in the RADIUS access-request packet.
Take a look at this prior thread: https://community.cisco.com/t5/protecting-applications/anyconnect-certificate-authentication-via-ise-and-duo-proxy/m-p/4883797/highlight/true#M3545
ETA - here is another https://community.cisco.com/t5/protecting-applications/anyconnect-cert-authent-via-ise-and-duo/td-p/4883029
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2024 12:59 AM
thankssssssss for your help.
just put [duo_only_client] in the proxy.cgf file and create new RADIUS server in ISE pointing to the proxy.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide