- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ACS 4.2 tacacs custom attribute for Nexus1000V
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACS 4.2 tacacs custom attribute for Nexus1000V
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2011 02:59 AM - edited 03-10-2019 06:13 PM
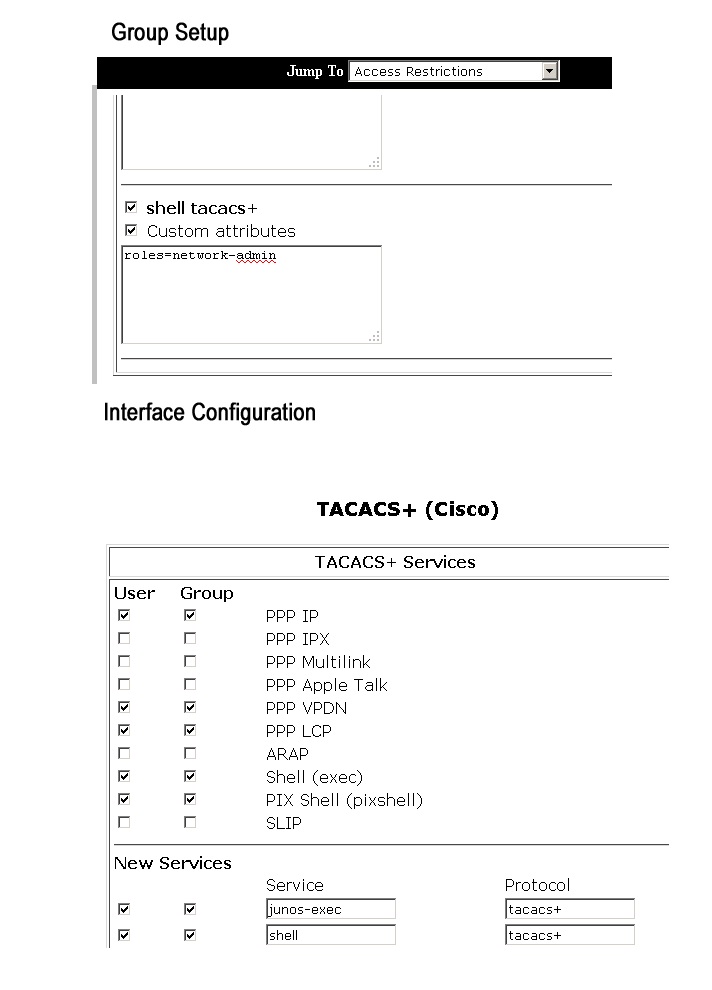
Dear All! Please, explain how to add tacacs custom attribute to ACS 4.2 for Nexus 1000V:
shell:roles="network-admin admin-vdc"
In the interface configuration I've added new service, service - shell, protocol - tacacs+.
In the group settings I've enabled this attribute configuration.
And it is not works. Default privilege level is assigned to any user with access allowed.
Screenshot is attached.
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2011 06:22 AM
Hi,
You should not have to add the shell tacacs service. Here is where you add the custom attributes:
There should be a custom attributes box under the shell (exec) service, enter it there. You only need network-admin for the value.
Thanks
Tarik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2011 06:44 AM
Thank you, but it was not helpful.

User recieves network-operator role:
Nexus1000V# conf t
Enter configuration commands, one per line. End with CNTL/Z.
Nexus1000V(config)# ?
no Negate a command or set its defaults
username Configure user information.
end Go to exec mode
exit Exit from command interpreter
Nexus1000V(config)#
aaa configured on Nexus like this:
aaa group server tacacs+ ACS
aaa authentication login default group ACS
aaa authentication login console local
aaa accounting default group ACS
in the debug I can see that correct attributes are recieved by Nexus:
2011 Jul 19 14:12:37.052510 tacacs: tplus_decode_author_response: attribute 0 service=shell
2011 Jul 19 14:12:37.052649 tacacs: tplus_decode_author_response: attribute 1 cmd=
2011 Jul 19 14:12:37.052789 tacacs: tplus_decode_author_response: attribute 2 shell:roles=network-admin
2011 Jul 19 14:12:37.052927 tacacs: tplus_process_vsa: got VSA attribute:shell:roles=network-admin
2011 Jul 19 14:12:37.053076 tacacs: tplus_process_vsa: got shell: home-dir: roles:network-admin uid:
2011 Jul 19 14:12:37.053223 tacacs: create_tacacs_user_profile: groups network-admin
thanks in advance for help.
UPDATE:
another interesting notification is that correct role is assigned to user, but configuration is not allowed:
sh user-account khabarov.evgeniy
user:khabarov.evgeniy
roles:network-admin
account created through REMOTE authentication
Credentials such as ssh server key will be cached temporarily only for this user account
Local login not possiblenexus1kv-01# where
khabarov@core-nexus1kv-01
core-nexus1kv# conf t
Enter configuration commands, one per line. End with CNTL/Z.
core-nexus1kv-01(config)# ?
no Negate a command or set its defaults
username Configure user information.
end Go to exec mode
exit Exit from command interpreternexus1kv(config)#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2011 11:54 PM
Do you know if someone tampered with the user roles on your nexus? Also do you have the feature privilege enabled? try issueing a show feature to see if it is enabled and remove it and try authenticating again.
thanks,
Tarik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2011 12:34 AM
Hi! There is no such feature:
sh feature
Feature Name Instance State
-------------------- -------- --------
dhcp-snooping 1 disabled
http-server 1 enabled
lacp 1 disabled
netflow 1 disabled
port-profile-roles 1 disabled
private-vlan 1 disabled
sshServer 1 enabled
tacacs 1 enabled
telnetServer 1 disabled
I attempted to remove user from both Nexus and ACS and relogin againt and it was not helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2011 12:58 PM
Can you send the output of the show roles?
Thanks,
Tarik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2011 10:19 PM
Hi!
core-nexus1kv-01# sh role
Role: network-admin
Description: Predefined network admin role has access to all commands
on the switch
-------------------------------------------------------------------
Rule Perm Type Scope Entity
-------------------------------------------------------------------
1 permit read-write
Role: network-operator
Description: Predefined network operator role has access to all read
commands on the switch
-------------------------------------------------------------------
Rule Perm Type Scope Entity
-------------------------------------------------------------------
1 permit read
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2011 09:27 PM
Eugene,
Please open a tac case to have this issue looked at further, we will need to do more analysis.
Thanks,
Tarik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2012 10:26 AM
Hello,
I have exactly the same problem with an ACS 5.2 returning the role attribute to Nexus 1000v. Remote user is authenticated but I can't run any privileged command even if the "show user" is good :
show user-account
user:admin
this user account has no expiry date
roles:network-admin
user:remoteadm
roles:network-admin
account created through REMOTE authentication
Did you manage to make it work ?
Thank you,
Vincent
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide