- Cisco Community
- Technology and Support
- Security
- Network Access Control
- AVAYA phone does not authenticate with the attribute to LLDP CISCO ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2021 12:14 PM
Hello, I bring another interesting topic, I have ISE 2.4 and I am trying to authenticate avaya phones using the LLDP attribute, however it does not work. I leave the configuration and see if it is possible that the same thing happened to someone
interface GigabitEthernet1/0/20
switchport access vlan 58
switchport mode access
switchport voice vlan 158
authentication event fail action next-method
authentication host-mode multi-domain
authentication order mab dot1x
authentication priority dot1x mab
authentication port-control auto
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast
device-sensor filter-list lldp list lldp-list
tlv name system-name
tlv name system-capabilities
device-sensor filter-spec lldp include list lldp-list
device-sensor accounting
device-sensor notify all-changes
ISE
Solved! Go to Solution.
- Labels:
-
Buying Recommendation
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2021 03:17 PM
One often overlooked feature that is missed is DHCP Snooping which solved my problem with profiling data not making its way to ISE.
https://community.cisco.com/t5/network-access-control/ise-and-dhcp-snooping/td-p/2473425
Its not to tricky to configure on an Access Switch but should fix your problem if you have ISE configured correctly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2021 12:36 PM
Do you have aaa accounting configured correctly? Please provide the output of "show run aaa"
Take a packet capture on ISE, filter on the NAD the phone is connected to. Check the output to confirm the switch sends the information.
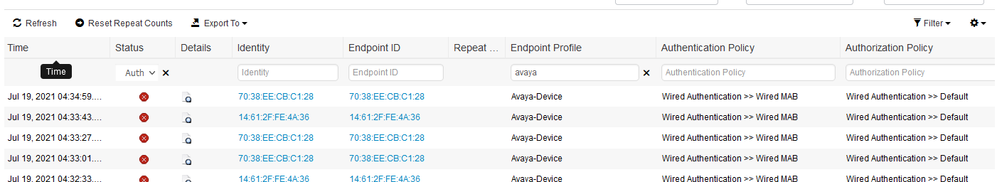
Go to the endpoint database and find the mac address of a profiled avaya phone, what Endpoint Policy has been applied?
And what was the "Total Certainy Factor"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2021 12:39 PM - edited 07-19-2021 12:40 PM
check below thread may help you : ( what you see ISE Live Logs ?) and what model of the switch and IOS ? - is there any phone works ?
https://community.cisco.com/t5/network-access-control/endoint-profile-avaya/td-p/3487509
with out ISE did the phone works?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2021 01:34 PM
Hi,
Just want to understand one more question what happens to the device? does the MAB work? or the avaya phones restarts after 59 secs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-19-2021 02:50 PM - edited 07-19-2021 02:51 PM
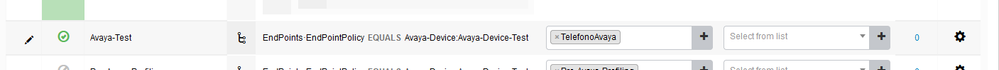
All this started, since a vulnerability came out in which a user could clone their mac from their Avaya phone and with that they could enter the network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2021 10:07 AM
Hi
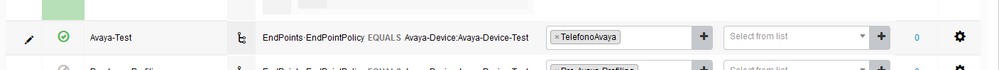
Can you try this policy --> IdentityGroup:Name Equals Endpoint Identity Group:Profiled:Avaya-Devices
Also in the Authorization profile should have voice permission given to do the same.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2021 12:43 PM
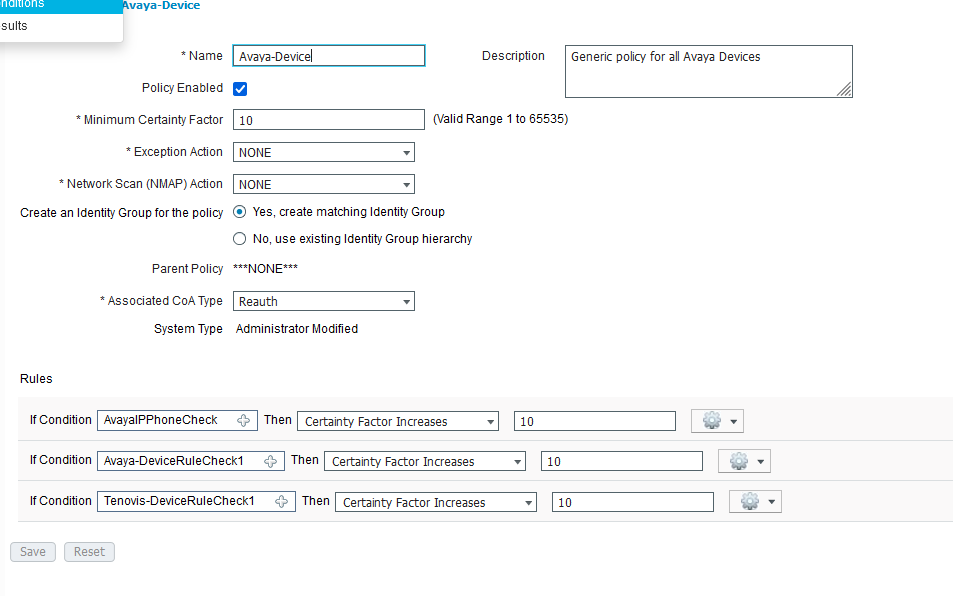
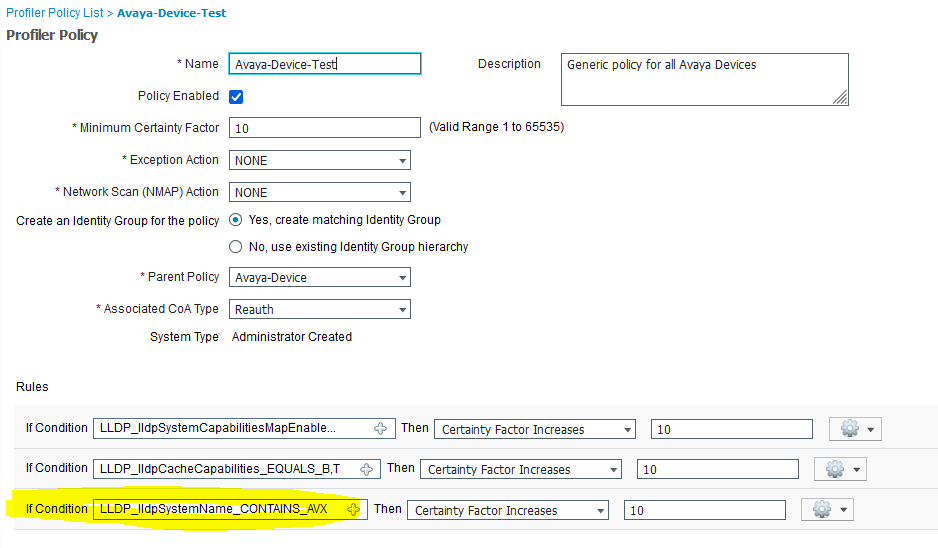
You should try the recommended device-sensor configuration from the ISE Secure Wired Access Prescriptive Deployment Guide :
lldp run ! device-sensor filter-list dhcp list DHCP-LIST option name host-name option name requested-address option name parameter-request-list option name class-identifier option name client-identifier ! device-sensor filter-list lldp list LLDP-LIST tlv name system-name tlv name system-description tlv name system-capabilities ! device-sensor filter-list cdp list CDP-LIST tlv name device-name tlv name address-type tlv name capabilities-type tlv name version-type tlv name platform-type ! device-sensor filter-spec dhcp include list DHCP-LIST device-sensor filter-spec lldp include list LLDP-LIST device-sensor filter-spec cdp include list CDP-LIST ! device-sensor accounting device-sensor notify all-changes !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-04-2021 03:17 PM
One often overlooked feature that is missed is DHCP Snooping which solved my problem with profiling data not making its way to ISE.
https://community.cisco.com/t5/network-access-control/ise-and-dhcp-snooping/td-p/2473425
Its not to tricky to configure on an Access Switch but should fix your problem if you have ISE configured correctly.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide