- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Cisco 2960X not sending Radius machine authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2023 09:06 PM
Hi All,
We have machine that is joined in AD and supposed to be doing machine auth, we notice for 2960x not sending radius machine authentication, instead it only does mac address. IPPhone/Printer authentication are working fine no issue at all.
We are using Anyconnect network module, and the same XML file we use all throughout deployment, with other switch model we do not encounter the issue.
Does anyone encounter the same issue? Please share your idea
Apr 5 12:59:22.118: RADIUS(00000000): Send Access-Request to 10.62.32.19:1812 onvrf(0) id 1645/123, len 274
Apr 5 12:59:22.118: RADIUS: authenticator 96 97 20 A7 63 28 A9 71 - EA FE 25 86 29 D7 CB 5C
Apr 5 12:59:22.118: RADIUS: User-Name [1] 14 "10E7C67821E8"
Apr 5 12:59:22.118: RADIUS: User-Password [2] 18 *
Apr 5 12:59:22.118: RADIUS: Service-Type [6] 6 Call Check [10]
Apr 5 12:59:22.118: RADIUS: Vendor, Cisco [26] 31
Apr 5 12:59:22.118: RADIUS: Cisco AVpair [1] 25 "service-type=Call Check"
Apr 5 12:59:22.118: RADIUS: Framed-MTU [12] 6 1500
Apr 5 12:59:22.118: RADIUS: Called-Station-Id [30] 19 "6C-41-0E-BD-98-8A"
Apr 5 12:59:22.122: RADIUS: Calling-Station-Id [31] 19 "10-E7-C6-78-21-E8"
Apr 5 12:59:22.122: RADIUS: Message-Authenticato[80] 18
Apr 5 12:59:22.122: RADIUS: 17 88 CA ED AF 58 4F 00 4A A3 F8 A8 93 EE 33 DA [ XOJ3]
Apr 5 12:59:22.122: RADIUS: EAP-Key-Name [102] 2 *
Apr 5 12:59:22.122: RADIUS: Vendor, Cisco [26] 49
Apr 5 12:59:22.122: RADIUS: Cisco AVpair [1] 43 "audit-session-id=0A7106FE00000BA2643F8AEF"
Apr 5 12:59:22.122: RADIUS: Vendor, Cisco [26] 18
Apr 5 12:59:22.122: RADIUS: Cisco AVpair [1] 12 "method=mab"
Apr 5 12:59:22.122: RADIUS: NAS-IP-Address [4] 6 10.113.6.254
Apr 5 12:59:22.122: RADIUS: Nas-Identifier [32] 13 "SEL-SWC-06S"
Apr 5 12:59:22.122: RADIUS: NAS-Port-Id [87] 23 "GigabitEthernet1/0/10"
Apr 5 12:59:22.122: RADIUS: NAS-Port-Type [61] 6 Ethernet [15]
Apr 5 12:59:22.122: RADIUS: NAS-Port [5] 6 50110
Apr 5 12:59:22.122: RADIUS(00000000): Sending a IPv4 Radius Packet
Apr 5 12:59:22.122: RADIUS(00000000): Started 5 sec timeout
Apr 5 12:59:22.387: RADIUS: Received from id 1645/123 10.62.32.19:1812, Access-Reject, len 92
Apr 5 12:59:22.387: RADIUS: authenticator C2 25 DA DB 9F 79 15 6F - E4 24 A3 CB AA EE 6C 9F
Apr 5 12:59:22.387: RADIUS: Message-Authenticato[80] 18
Apr 5 12:59:22.387: RADIUS: 11 80 C2 6C 8E C6 58 99 CD 95 FE 99 4A D3 C1 42 [ lXJB]
Apr 5 12:59:22.387: RADIUS: Vendor, Cisco [26] 54
Apr 5 12:59:22.387: RADIUS: Cisco AVpair [1] 48 "AuthenticationIdentityStore=Internal Endpoints"
Apr 5 12:59:22.391: RADIUS(00000000): Received from id 1645/123
Switch port configuration:
interface GigabitEthernet1/0/10
switchport mode access
switchport voice vlan 2
authentication event fail action next-method
authentication event server dead action authorize vlan 11
authentication event server dead action authorize voice
authentication event server alive action reinitialize
authentication host-mode multi-domain
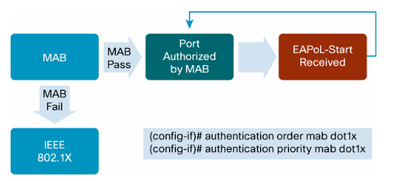
authentication order mab dot1x
authentication priority mab dot1x
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
authentication violation restrict
mab
dot1x pae authenticator
dot1x timeout tx-period 10
spanning-tree portfast edge
Radius/AAA configuration:
aaa group server radius SP-ISE-GROUP
server name VMISE02
server name VMISE01
aaa authentication login CONSOLE local
aaa authentication login THALOGIN group ISE-TACACS local
aaa authentication dot1x default group SP-ISE-GROUP
aaa authorization exec default group ISE-TACACS local if-authenticated
aaa authorization network default group SP-ISE-GROUP
aaa authorization auth-proxy default group SP-ISE-GROUP
aaa accounting send stop-record authentication failure
aaa accounting update periodic 5
aaa accounting dot1x default start-stop group SP-ISE-GROUP
aaa accounting exec default start-stop group ISE-TACACS
aaa accounting network default start-stop group SP-ISE-GROUP
aaa accounting system default start-stop group SP-ISE-GROUP
aaa server radius dynamic-author
client 10.62.x.xserver-key 7 (omitted)
client 10.62.x.x server-key 7 (omitted)
aaa session-id common
ip radius source-interface Vlan11
radius server VMISE01
address ipv4 10.62.x.x auth-port 1812 acct-port 1813
automate-tester username dummy idle-time 5
key 7 (omitted)
radius server VMISE02
address ipv4 10.62.x.x auth-port 1812 acct-port 1813
automate-tester username dummy idle-time 5
key 7(omitted)
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
-
Wired
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2023 11:13 AM
The authentication order and priority in the switchport configuration is "mab dot1x". With this configuration, dot1x will only happen if MAB fails.
Change the authentication priority to "dot1x mab" and you should see switch initiating EAPoL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2023 08:03 AM
I agree with Nancy. Also, i dont see below command for data vlan on this port.
switchport access vlan xx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2023 02:53 PM
@Nancy Saini had a great suggestion and you may compare your configuration with our ISE Secure Wired Access Prescriptive Deployment Guide which has example configurations following best practices.
Also, we always recommend authentication host-mode multi-auth over multi-domain. if you have problems with phones+workstations on the same port, switch to multi-auth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-06-2023 11:13 AM
The authentication order and priority in the switchport configuration is "mab dot1x". With this configuration, dot1x will only happen if MAB fails.
Change the authentication priority to "dot1x mab" and you should see switch initiating EAPoL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2023 08:03 AM
I agree with Nancy. Also, i dont see below command for data vlan on this port.
switchport access vlan xx
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2023 02:53 PM
@Nancy Saini had a great suggestion and you may compare your configuration with our ISE Secure Wired Access Prescriptive Deployment Guide which has example configurations following best practices.
Also, we always recommend authentication host-mode multi-auth over multi-domain. if you have problems with phones+workstations on the same port, switch to multi-auth.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide