- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: dot1x and reauth
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 06:31 AM
We are running dot1x and ISE, we only do machine authentication. We have configured reauth every 600 seconds. If we have a skype call going on and the switch is requesting the client to reauth the session "Session timeout: 600s (server), Remaining: 0s" the sound in the call is interrupted for aprox 5 seconds.
Any one suffer from the same problem ? And how did you solved it ?
/Magnus
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 04:24 PM
yes that timeout is a bit extreme. However, it doesn't change the fact that when a session time DOES occur, that your clients will be happy with a 5 second interruption.
There are 802.1X protocol enhancements that can be enabled to allow the EAP process to be sped up. In a non-optimised case, there are around a dozen EAP messages sent from the supplicant to ISE - if there is a lot of latency then this all adds up.
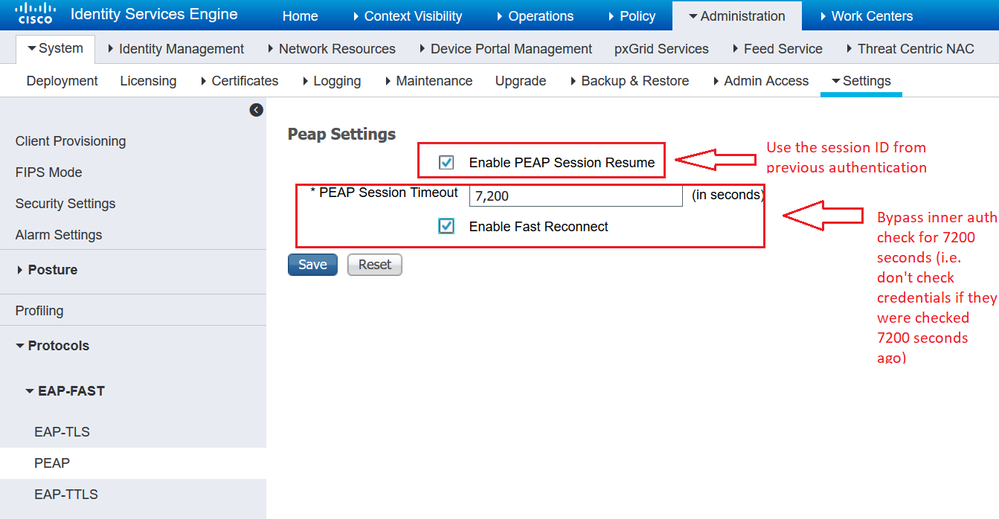
You don't mention which EAP method you're using, but in the case of EAP-PEAP you can enable two things - one at a time ...
Finally, on the wireless level, there are things that could be done to prevent the need to even speak to the radius server. E.g. 802.1r (Fast Transition/Fast Roaming), etc. That's a whole other discussion and it's dependent on the client support. The idea is that the WLC takes care of the keying material without needing a Radius server to keep generating it. You do it for a certain time period, and then involve the radius server again. But it reduces load on radius server, network and also better experience for clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 10:26 AM
A re-auth frequency of 600 seconds (or 10 minutes) is much too often. The best practice is to increase it to 2+ hours (or 7200+ seconds). See the slide 264 in Session Reference from Designing ISE for Scale & High Availability - BRKSEC-3699.
In your case, you might want to adjust it to at least 8 hours.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 04:24 PM
yes that timeout is a bit extreme. However, it doesn't change the fact that when a session time DOES occur, that your clients will be happy with a 5 second interruption.
There are 802.1X protocol enhancements that can be enabled to allow the EAP process to be sped up. In a non-optimised case, there are around a dozen EAP messages sent from the supplicant to ISE - if there is a lot of latency then this all adds up.
You don't mention which EAP method you're using, but in the case of EAP-PEAP you can enable two things - one at a time ...
Finally, on the wireless level, there are things that could be done to prevent the need to even speak to the radius server. E.g. 802.1r (Fast Transition/Fast Roaming), etc. That's a whole other discussion and it's dependent on the client support. The idea is that the WLC takes care of the keying material without needing a Radius server to keep generating it. You do it for a certain time period, and then involve the radius server again. But it reduces load on radius server, network and also better experience for clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2018 11:10 PM
Hi.
We have this quit aggressive reauth time because we will not allow unauthorized clients accessing our network, (not for a long time anyway (600 seconds is enough).
I think you (Arne) might point me to the right direction. We use EAP-TLS, there is a tickbox "Enable Stateless Session Resume" and "Session ticket time to live". If I would like to stay with 600 seconds with reauth what value would you put in the above parameters.
When the reauth occurs the skype call is interrupted for like 3-5 seconds, we had a ping going at the same time and the response time went from 2ms to 6ms.
/Magnus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 07:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 03:45 AM
Hi. Here is the portconfiguration.
interface GigabitEthernet2/0/32
switchport mode access
switchport nonegotiate
switchport block multicast
switchport block unicast
ipv6 nd raguard
ipv6 snooping attach-policy snooping-policy
ipv6 dhcp guard
authentication event fail action next-method
authentication event server dead action authorize vlan 999
authentication event no-response action authorize vlan 999
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
authentication periodic
authentication timer reauthenticate server
mab
no snmp trap link-status
dot1x pae authenticator
dot1x timeout tx-period 3
dot1x max-reauth-req 1
storm-control broadcast level 60.00 40.00
storm-control action shutdown
spanning-tree portfast
spanning-tree bpduguard enable
ip dhcp snooping limit rate 30
end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 07:32 AM
Make sure the ISE is sending both session-timeout value (600) and the terminate-action value (1).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2018 01:09 AM
Hi here are some of the radius attribites that we send. I think Terminate-Action = Radius-Request is the value of 1.
Access Type = ACCESS_ACCEPT
Session-Timeout = 600
Termination-Action = RADIUS-Request
/Magnus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-07-2018 08:55 AM
Can you post the conditions used in the policy rule? Also, the detailed report should provide where the delays are from the ISE side. If no delays seen in the detailed report, then you will have to look into the switch debug logs to find out the root cause of delay.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 02:25 PM
Hey @MAGNUS SVENSSON, I have been meaning to test that in my own lab for some time but just haven't got around to it. Are you able to have a go and let us know how it worked out for you?
In the past I did some tests with PEAP optimisations in ISE and analysed the PSN tcpdumps in wireshark - you can see that the number of radius/EAP messages reduces quite a bit. But I have not tried any of the wireless optimisations - you could start with a modern iPhone and enable all the fancy optimisations, and then work your way backwards until you find a config that supports all the devices in your network. Enabling all the nerd knobs in production is probably a recipe for disaster ;-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-06-2018 03:51 AM
I have a case logged with Cisco.
I will post any result from that.
/Magnus
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-20-2018 05:28 AM
Best regards
Magnus
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide