- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Integrating ISE with Azure Intune as MDM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-05-2021 05:57 AM - edited 10-05-2021 05:59 AM
Hello,
I'm trying to use Computer authentication with Azure AD.
As Azure AD only works with SAML, and ROPC only allows EAP-TTLS ie user authentication , I'm looking into Intune as a MDM server.
I've followed all the procedure here :
The certificates are trusted both sides, but when I test the connection I get the following error :
Connection to server failed with:
Unrecognized field "requestId" (Class com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorOdata), not marked as ignorable at [Source: java.io.StringReader@20d9ea84; line: 1, column: 152] (through reference chain: com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorResponse["odata.error"]->com.cisco.cpm.mdm.auto.discovery.MdmAzureDirectoryServiceErrorOdata["requestId"])
Please try with different settings.
Packet capture shows one connection to the token URL, so I guess the token retrieval is ok, then another connection to the discovery URL https://graph.windows.net/<Tenant ID>.
We are running version 3.0 Patch 4.
Does anyone knows how to resolve this ?
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-13-2022 03:37 PM
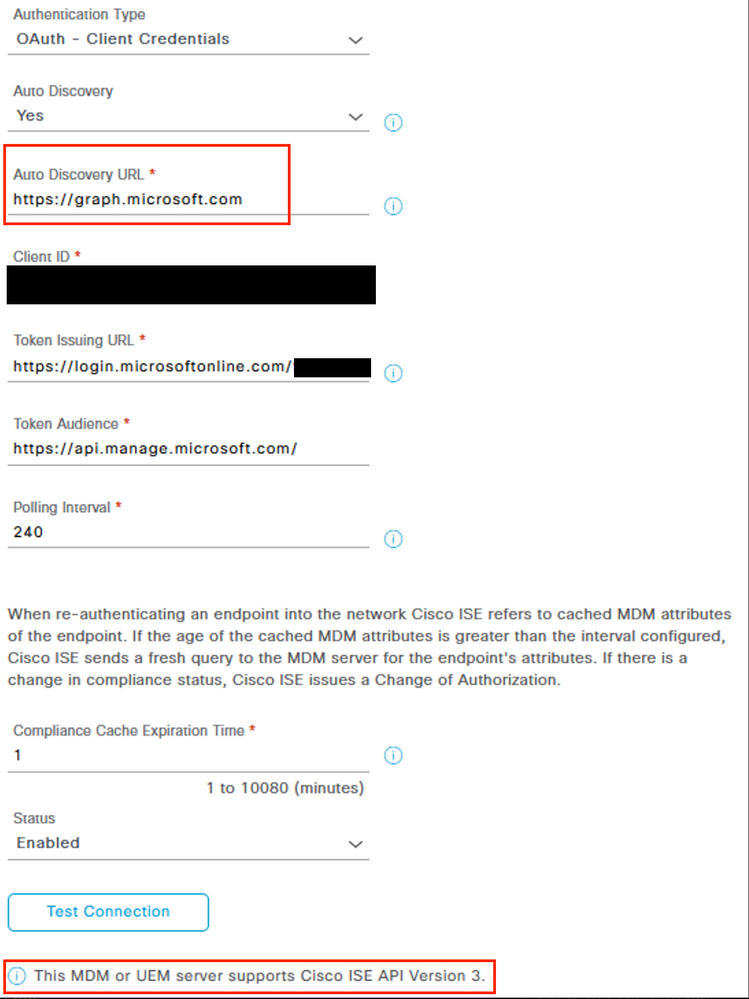
The reference to https://graph.windows.net/<Directory (tenant) ID> in Step 32 of the document is a mistake. The Auto Discovery URL field should be configured as https://graph.microsoft.com. You are likely getting the error as there is no <Directory (tentant) ID> value after this.
Example from my lab:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-15-2022 12:14 AM
Wonderful, thank you Greg, it works!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-06-2025 08:05 PM
hi @Greg Gibbs
When i use https://graph.windows.net i got below error
Then i change to https://graph.windows.com the i got this error
and i have app registration for this
Are you know why?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-12-2025 06:10 PM
Responding to an old post marked as resolved is not an ideal way to get assistance. In the future, please open a new discussion.
As stated in the Intune Integration Guide, the Auto Discovery URL should be "https://graph.microsoft.com"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-21-2022 02:27 AM
Hi all,
In response of all the information, I have got this issue and I cant get why this is happening.
Maybe I'm overlooking something, and you can help me this this.
The External MDM connection is working oke, test connection is oke. And I did a test based on MAC address and this also works oke.
But I want to use the GUID solution.
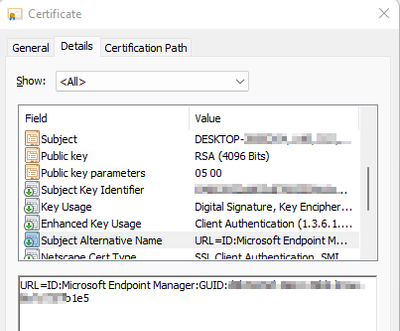
I have got a Machine with a certificate with SAN URI attribute:
URL=ID:Microsoft Endpoint Manager:GUID:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
The GUID is the Intune ID of the Device. I double checked this.
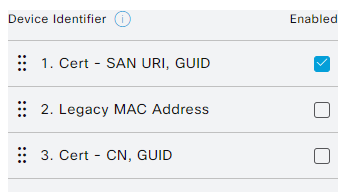
In the ISE configuration I configured the use of Cert - SAN URI, GUID
But it is not working as expected.
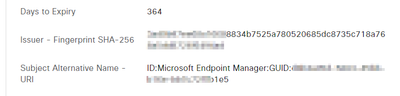
The URI is seen in the live logging of the session, Subject Alternative Name - URI:
In the logging I see this, value is 'null'
2022-12-21 10:23:43,221 DEBUG [Thread-240][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- SESSION IS NOT NULL & CERTIFICATE.CN Field value is - 'null' and CERTIFICATE.SAN DNS Field value is - 'null' and CERTIFICATE.CERT_SANURI_KEY Field value is -'null'
2022-12-21 10:23:43,221 DEBUG [Thread-240][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Actual check of CERTIFICATE.CN Field value is - 'null' and CERTIFICATE.SAN DNS Field value is - 'null' and CERTIFICATE.CERT_SANURI_KEY Field value is -'null'
2022-12-21 10:23:43,221 DEBUG [Thread-240][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- ise db/cache Configured device Identifier source order values are : CERT_SANURI_GUID
2022-12-21 10:23:43,221 DEBUG [Thread-240][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Checking the current deviceIdentifier value : CERT_SANURI_GUID
2022-12-21 10:23:43,221 DEBUG [Thread-240][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- The value for the DeviceIdentifier Source 'CERT_SANURI_GUID' is 'NULL', hence checking the next Device Identifier source..!
2022-12-21 10:23:43,221 INFO [Thread-240][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- The value for the deviceIdentifier type of 'null' is - 'null'
Can anyone point me in the right direction why this is not working?
Thanks, Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2022 01:39 PM
The same question was posted on the ISE Bar Webex space, so copying the responses here for the benefit of others.
In your Intune MDM configuration, do you see the text stating that it supports APIv3? If not, then your App may not be configured correctly in Azure.
If the App and ISE are configured correction, you should also see the GUID in the Live Logs for the session. Are you seeing this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 12:12 AM
Thanks for the reply. Yes, ISE version is 3.2. And ISE is connected by API Version 3. And the Device Identifiers are configurable for all 3 options.
I also checked the logging, but I don't see the GUID in the live logging.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 12:26 AM
Correction, I am seeing the GUID now. This is different from last week when the GUID was not in the logging.
So I will take a look at this and post the outcome.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-27-2022 02:32 AM
Oke, the result is still the same -> From the debug logs: The value for the DeviceIdentifier Source 'CERT_SANURI_GUID' is 'NULL', etc.
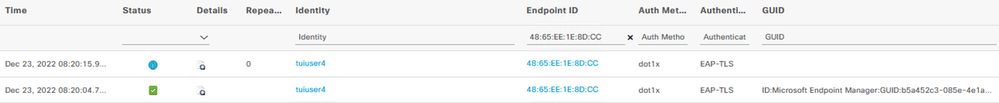
In the live logging I see the GUID -> ID:Microsoft Endpoint Manager:GUID:xxx etc.
But access is denied, because I think ISE is not connecting to the MDM environment because of the DeviceIdentifier Source 'CERT_SANURI_GUID' is 'NULL'
Changed back to MAC -> and this is working.
This is really annoying, can't get this to work as expected.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 07:38 AM
Hi,
I have same issue as you.
My CN is ok but SANURI is null whole time.
23-04-27 13:45:58,002 DEBUG [Thread-76][] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- SESSION IS NOT NULL & CERTIFICATE.CN Field value is - '401bbf6f-4a38-4e31-8e20-cae12be3e003' and CERTIFICATE.SAN DNS Field value is - 'null' and CERTIFICATE.CERT_SANURI_KEY Field value is -'null'
2023-04-27 13:45:58,002 DEBUG [Thread-76][] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Actual check of CERTIFICATE.CN Field value is - '401bbf6f-4a38-4e31-8e20-cae12be3e003' and CERTIFICATE.SAN DNS Field value is - 'null' and CERTIFICATE.CERT_SANURI_KEY Field value is -'null'
2023-04-27 13:45:58,002 DEBUG [Thread-76][] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- ise db/cache Configured device Identifier source order values are : CERT_SANURI_GUID
2023-04-27 13:45:58,002 DEBUG [Thread-76][] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Checking the current deviceIdentifier value : CERT_SANURI_GUID
2023-04-27 13:45:58,002 DEBUG [Thread-76][] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- The value for the DeviceIdentifier Source 'CERT_SANURI_GUID' is 'NULL', hence checking the next Device Identifier source..!
2023-04-27 13:45:58,002 INFO [Thread-76][] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- The value for the deviceIdentifier type of 'null' is - 'null'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 06:19 PM
The only bug I'm aware of related to the MDM APIv3 with Intune GUID is the following:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCwe38610
I've done testing recently with ISE 3.2p1 and am not able to replicate any issues with the Intune MDM compliance checks. If you have ensured you are using the capital case for 'ID' in your SAN URI string, you will likely need to open a TAC case to investigate further.
Some relevant debug/trace logs from my lab:
2023-04-28 11:02:09,899 TRACE [Thread-388][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Session Info attributes: Attrs: {TUI_AzureAD_ROPC.ExternalGroups=[xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx], MdmType=External, Network Access.WasMachineAuthenticated=[false], SavedUserNames=[tuiuser10@domain.onmicrosoft.com], CERTIFICATE.Issuer - Common Name=TUI-CA, Network Access.AuthenticationMethod=[5], Radius.NAS-Port-Type=15, CERTIFICATE.Subject Alternative Name - URI=[ID:Microsoft Endpoint Manager:GUID:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx], Normalised Radius.RadiusFlowType=0, Network Access.EapAuthentication=[2], CERTIFICATE.Subject - Common Name=[tuiuser10@domain.onmicrosoft.com], CERTIFICATE.Subject - Organization Unit=[], __IntIdGrps__=[Ljava.lang.String;@23e29bb7}
IndexValues: {}
2023-04-28 11:02:09,899 DEBUG [Thread-388][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- SESSION IS NOT NULL & CERTIFICATE.CN Field value is - 'tuiuser10@domain.onmicrosoft.com' and CERTIFICATE.SAN DNS Field value is - 'null' and CERTIFICATE.CERT_SANURI_KEY Field value is -'ID:Microsoft Endpoint Manager:GUID:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx'
2023-04-28 11:02:09,899 DEBUG [Thread-388][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Actual check of CERTIFICATE.CN Field value is - 'tuiuser10@domain.onmicrosoft.com' and CERTIFICATE.SAN DNS Field value is - 'null' and CERTIFICATE.CERT_SANURI_KEY Field value is -'ID:Microsoft Endpoint Manager:GUID:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx'
2023-04-28 11:02:09,899 DEBUG [Thread-388][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- ise db/cache Configured device Identifier source order values are : CERT_SANURI_GUID
2023-04-28 11:02:09,899 DEBUG [Thread-388][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- Checking the current deviceIdentifier value : CERT_SANURI_GUID
2023-04-28 11:02:09,899 INFO [Thread-388][[]] cisco.cpm.mdm.pip.MdmPartnerPIPHandler -::::- The value for the deviceIdentifier type of 'SAN_URI' is - 'ID:Microsoft Endpoint Manager:GUID:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxx'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-05-2023 08:22 AM
Hi,
I've manage to resolve problem.
Problem was in URI configuration on SCEP profile in Intune.
BTW
How is 3.2 patch 1 showing. Did you try it in production or only lab env?
We have intention to upgrade from 3.1 to 3.2 and use AZURE AD integration for EAP-TEAP configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2023 03:19 PM
As ISE 3.1 is still the recommended version, I have not had any customers deploy it in Production yet.
If you intend to use Azure AD with ISE, I would suggest reviewing the following document I wrote to understand what can and cannot be done with Azure AD.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-08-2023 03:49 AM
Thanks for responde and link.
I am aware that 3.1 is still recommended version.
BR
Danijel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2023 11:07 PM
Do you mind sharing what you did to fix the issue? Facing the same problem using an Intune pushed SCEP cert profile to mobile devices.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide