- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE 1.1.1 - Error Code 12521 EAP-TLS failed SSL/TLS handshake after a client alert
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ISE 1.1.1 - Error Code 12521 EAP-TLS failed SSL/TLS handshake after a client alert
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2012 10:36 AM - edited 03-10-2019 07:25 PM
Hello,
Has anyone come across this error code before? I have looked in the 1.1.1 troubleshooting section and there is nothing there. When I click on the link for the description off the error in ISE I get the following error:
I setup 7925 phones for EAP-TLS using MIC. I have uploaded Cisco's Root CA and Manufactoring CA Certificates and enabled "Trust for client authentication". A Certificate Profile is configured matching Common Name and is added to the Identity Sequence. I got some additional attribute information, where there is a error message:
OpenSSLErrorMessage=SSL alert code=0x233=563 ; source=remote ; type=fatal ; message="decrypt error"
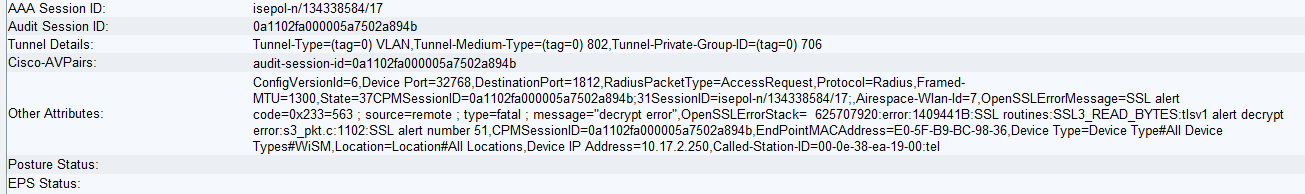
Anyone know what this error means?
- Labels:
-
AAA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2013 07:18 AM
Hi Jatin Katyal,
yes, the ISE suppports SHA-256, but the Phones don't. That's why the log says "12815 Extracted TLS Alert message" and "The request sent by the client was syntactically incorrect" and "12521 EAP-TLS failed SSL/TLS handshake after a client alert".
FIPS mode is disabled anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2013 07:24 AM
In my case the installed Cisco CA Root is Sha1 2048. The phones have the same root and manufactoring certificates installed as well as the MIC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2013 07:31 AM
yes, CiscoRootCA is fine.
But your ISE certificates must be SHA-1 as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2013 05:38 AM
Is the only way to support the SHA-256 is to be in FIPS mode? We currently do not use FIPS, but we do want to use SHA-256 for clients. As for our phones (7925;s), I may have the same issues.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-24-2013 05:58 AM
FIPS mode won't do anything useful, if you try to authenticate your 7925 using EAP-TLS.
Let me try to explain:
When using EAP-TLS, the client (7925 in this case) has to trust your authentication server ca (your ISE) and otherwise. To accomplish this, you install the CiscoRootCA and CiscoManufacturingCA on your ISE and install the ISE's root ca certificates on the phones. As soon as your ISE's root ca certificate (which you have to install on the phones) is based on SHA256 it won't work because the phones don't support any certificate basen on SHA256.
To conclude: The only way to authenticate your 7925 using EAP-TLS, you have to make sure your ISE certificates and the appropriate certificate chain is based on SHA1.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-22-2015 03:27 PM
3 years later and I've run into this issue too. Cisco want us to just use a 2048bit CA cert with SHA-1 when really they should upgrade the firmware of the phone to support 4096 SHA-2
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide