- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: ISE 2.2 FMC user radius authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 05:39 AM - edited 02-21-2020 10:58 AM
Hello everyone,
I'm working to have the user FMC user authentication through cisco ISE (with AD), but I cannot find a proper documentation, just some old stuff like https://www.cisco.com/c/en/us/support/docs/security/firesight-management-center/118541-configure-firesight-00.html .
Does anyone has a proper example about how this must be done?
ISE is on version 2.2 (already integrated with AD0, FMC on 6.2.3.1.
Thank you!
Best regards.
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2019 12:54 AM
I've just configured this on FMC version 6.2.3.8 following this guide: https://goo.gl/pm1e4G
Just a note: under the RADIUS-Specific Parameters section, instead of "Class=User Identity Groups:Sourcefire Administrator" I've set it to "Class=Administrator".
Best regards,
Matteo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 02:00 PM
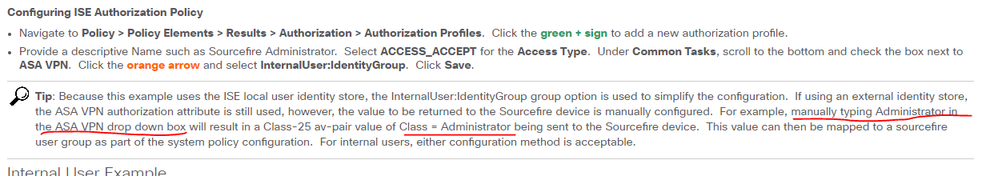
Of course, right after I made my earlier post I figured it out from this document:
Pay close attention to the Tip!
Hopefully this helps someone else!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2019 04:49 AM
I just got this working. Heres how i did it:
In ISE 2.3:
AuthZ profile in Policy results, call your policy "FMC_Admin". When using the ASA VPN checkbox, clicke the dropdown menu and overwrite it with "Administrator", or whatever you want to call it. Lets say "Paladin" to make a point. Just make sure that name is carried over to FMC later.
The bottom of the attritbute details box should now say:
Access Type: ACCESS_ACCEPT
Class = Administrator (or Paladin)
Add this to your Authz policy as usual.
In the authentication conditions on the same policy, select the AD group that your admins will be a member of. This is local only to ISE and AD. FMC has no sight of this.
Now, in the example on the page, for the Administrator role on FMC, that box is filled with "Class = User Identity Groups: Sourcefire Administrator, overwrite this with "Class=Administrator (or Paladin)", where this is the name you created in your authz profile. Note this is local only to ISE and FMC
And away you go!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-18-2018 08:27 AM
Even though it's several years old the basics of using ISE (or any other external RADIUS server) for FMC use authentication haven't changed.
I use the method described in the article you mentioned with my installation (ISE 2.4 and FMC 6.2.3.2) just fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2018 01:44 AM
Hello Marvin,
Thanks for the reply.
The problem I have is the authorization through AD.
check_auth_radius: szUser: XXX
RADIUS config file: /var/tmp/fF3Rri8AVH/radiusclient_0.conf
radiusauth - response: |User-Name=xxx|
radiusauth - response: |State=ReauthSession:0ac7c82cbjeyc4zZNkNstxPVbwVeRV79i9a1aaxK74wxv27M7rQ|
radiusauth - response: |Class=[x.x.x/S-1-5-32-545, S-1-5-21-588942262-2422670607-1746572812-94476]|
radiusauth - response: |Class=CACS:0ac7c82cbjeyc4zZNkNstxPVbwVeRV79i9a1aaxK74wxv27M7rQ:DKIX09INF-ISE-1/313846743/128638|
"xxx" RADIUS Authentication OK
No Access
The authentication is working, though, I'm not able to authorized myself.
Not sure how the Class and Groups needs to be setup in the FMC or what attribute the ASA VPN should have in ISE.
Still working on this.
Best regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 01:59 PM
Not sure if you have found the solution or not but this is how I have set it up.
Apart from setting up ASA VPN attribute to desired role on ISE side.
On FMC under System > Users > External Authentication for Radius-Specific Parameters I have entered the Class=Administrator in the box next to Administrator and so forth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-05-2019 12:54 AM
I've just configured this on FMC version 6.2.3.8 following this guide: https://goo.gl/pm1e4G
Just a note: under the RADIUS-Specific Parameters section, instead of "Class=User Identity Groups:Sourcefire Administrator" I've set it to "Class=Administrator".
Best regards,
Matteo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 09:36 AM
Thanks your reply was helpful.
I have a question, does setting in RADIUS-Specific Parameter overrides the permissions we have set for users on the FMC itself under System>Users>Users?
I had mixed results
on FMC "USER1" was given role of Intrusion Admin
Through ISE USER1 was set to get the Administrator role.
This worked, when USER1 logged on to FMC it got the full access at the same time Role on FMC got updated to Administrator Automatically
On second test
On FMC USER1 was given rule of Administrator
Through ISE USER1 was set to get the Intrusion Admin role.
But it will still get the Administrator role.
Have you run into similar situation before?
Also is it MUST to configure user as external user on FMC for Radius External Authentication to work?
Also How can I give multiple permission to a single user through Radius
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-13-2020 09:15 AM
I would check what the default role is set as on FMC external authentication. It sounds like you have set it to administrator
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2020 01:46 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2020 03:07 AM
As far as I know, a given username can only be one role or another. They would have to have unique usernames if you want different roles to be assigned.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 09:02 AM
@Marvin Rhoads , Thanks for your response.
I found the workaround, on the FMC I created the custom role which has permission for both Security Analyst and Intrusion Admin, and used that to assign permission to users via Authz profile Cisco VPN attribute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-27-2020 09:35 AM
Ah - good idea. I answered your question literally and hadn't considered the approach you used.
Thanks for sharing your solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 01:28 PM
For what it's worth, I am having the very same problem/frustration.
I'd like to know the exact strings to enter into the FMC's RADIUS-Specific Parameters Administrator field, and exactly what to use for the corresponding av-pair in the ISE authorization profile.
I have tried User-Category=Administrator on the FMC and Access Type = ACCESS_ACCEPT
cisco-av-pair = User-Category=Administrator in ISE, as well as replacing the = with a :.
Also tried Class=Administrator and cisco-av-pair = Class=Administrator (as well as replacing = with :) but those don't work either.
Authentication is successful, but the user role assignment is NOT working. I always end up with the default role of Security Analyst read-only.
Can someone please clear this up once and for all??? So frustrated!
Thanks very much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 02:00 PM
Of course, right after I made my earlier post I figured it out from this document:
Pay close attention to the Tip!
Hopefully this helps someone else!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2019 04:49 AM
I just got this working. Heres how i did it:
In ISE 2.3:
AuthZ profile in Policy results, call your policy "FMC_Admin". When using the ASA VPN checkbox, clicke the dropdown menu and overwrite it with "Administrator", or whatever you want to call it. Lets say "Paladin" to make a point. Just make sure that name is carried over to FMC later.
The bottom of the attritbute details box should now say:
Access Type: ACCESS_ACCEPT
Class = Administrator (or Paladin)
Add this to your Authz policy as usual.
In the authentication conditions on the same policy, select the AD group that your admins will be a member of. This is local only to ISE and AD. FMC has no sight of this.
Now, in the example on the page, for the Administrator role on FMC, that box is filled with "Class = User Identity Groups: Sourcefire Administrator, overwrite this with "Class=Administrator (or Paladin)", where this is the name you created in your authz profile. Note this is local only to ISE and FMC
And away you go!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-02-2019 06:34 AM
Hello,
I have configured today Cisco FMC 6.2.3.10 with Aruba Clear Pass with Radius.
All went good until I had to pick the authentication method. I ended up with PAP. Does anyone know how can I "convince" FMC to agree for MSCHAP at least? How can I edit / choose Radius AUTH methold on Firepower Management Center?
Thanks,
Florin.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide