- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2017 09:09 PM
Hi,
I was reading an older post that says "you have two options to do that, either import all mac address to ISE and have your policy look into this endpoint group with username or have an MDM"
the MAC address thing doesn't scale and not the best approach for a large environment. if MDM isn't available to me.....
With 2.2 I want to know if there is a way that I can look at the authentication of the windows laptop and if it is performing Machine auth then allow access because that means it is a domain joined laptop.
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 07:19 AM
Fahad,
You are describing a basic Machine Authentication scenario which is based on AD Domain Computers.
This is very easy to do and you do not need to rely on the MAC address or an MDM!
Ensure that you have added the Domain Computers group in your ISE Active Directory Groups tab :
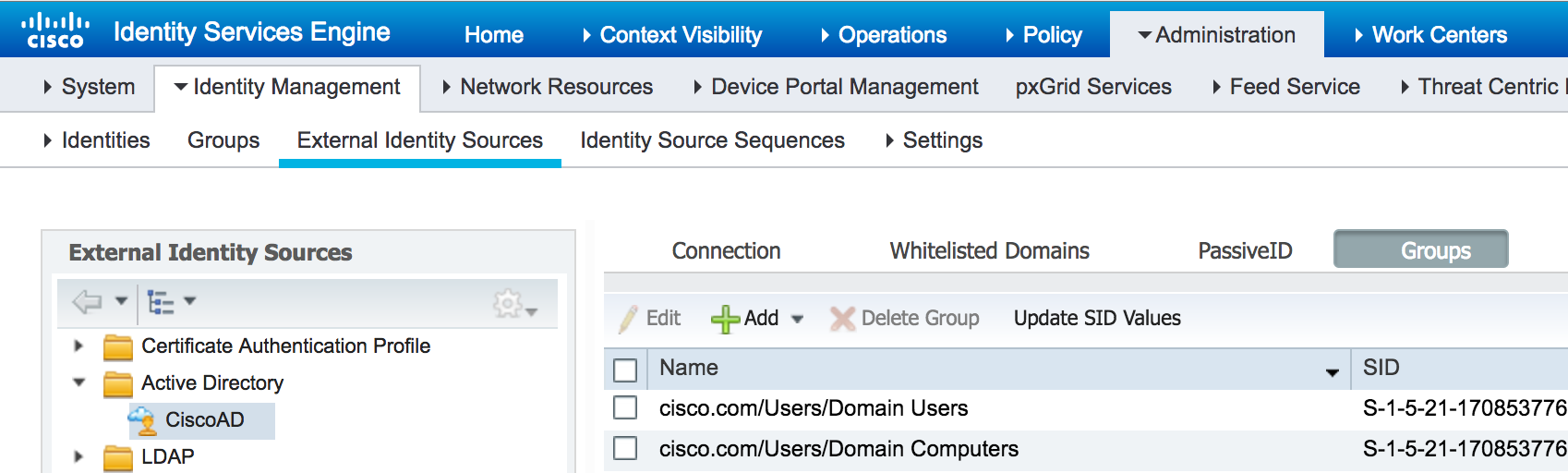
Now simply create an authorization rule that matches your Domain Computers group
<domain>:ExternalGroups Equals <domain>/Users/Domain Computers
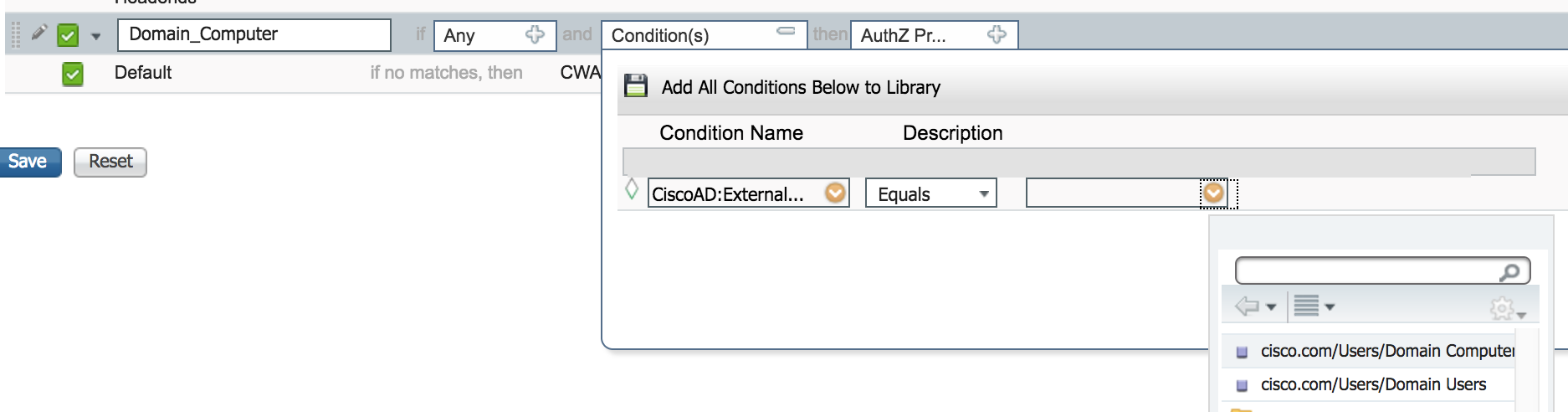
and assign the appropriate Authorization result to provide the appropriate network access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2017 11:20 PM
have a look at the following link. The feature you are looking for is called PassiveID ISE Design & Integration Guides
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-28-2017 07:19 AM
Fahad,
You are describing a basic Machine Authentication scenario which is based on AD Domain Computers.
This is very easy to do and you do not need to rely on the MAC address or an MDM!
Ensure that you have added the Domain Computers group in your ISE Active Directory Groups tab :

Now simply create an authorization rule that matches your Domain Computers group
<domain>:ExternalGroups Equals <domain>/Users/Domain Computers

and assign the appropriate Authorization result to provide the appropriate network access.