- Cisco Community
- Technology and Support
- Security
- Network Access Control
- TACACS authentication with a proxy Radius and local authorization done in ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2020 09:58 AM
Hi,
I'm trying together with a DUO engineer to find a solution to create a TACACS policy in ISE where the authentication is done through a proxy-radius, while the authorization is still defined in (and returned by) ISE.
The ultimate goal obviously is to integrate a dual factor with DUO radius-proxy.
Currently, it seems that ISE is doing only an authentication process when the identity database is pointing to a radius server, while the authorization works with a local identity source. It doesn't allow the proper set of rights to be sent back to the network device.
I don't know wether it's an expected behavior, or if there is some particular config to continue with the authorization rules once the authentication is done.
Thanks for any comment,
Jean-Francois
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2020 06:49 PM - edited 05-19-2020 06:54 PM
Hi
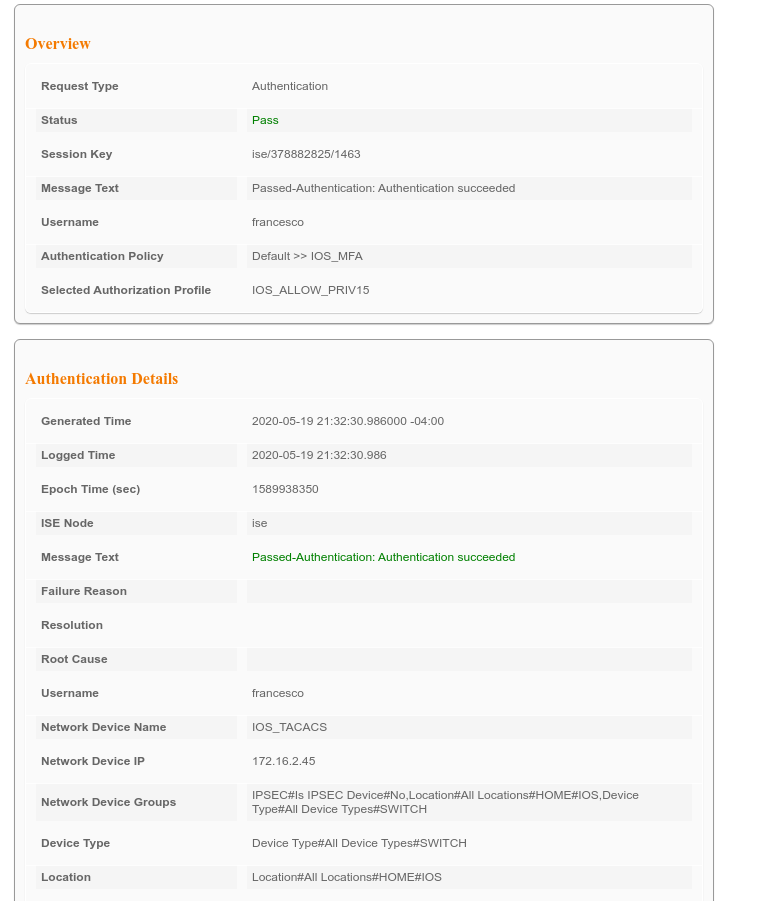
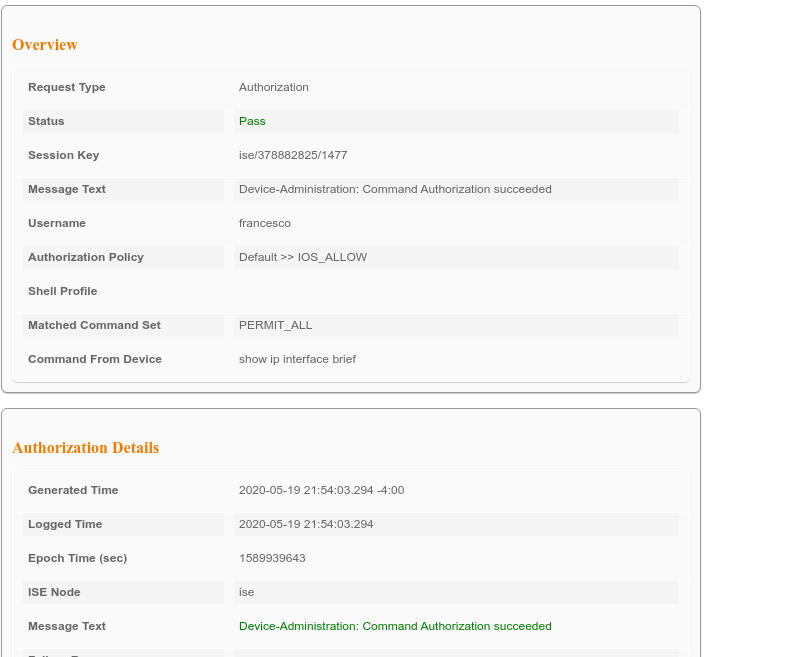
You want to connect on a device using tacacs and getting a push from Duo for authentication and if ok then push a shell profile. If so then it is possible using the proxy radius which I believe you refer to Duo Proxy?
Below my authproxy.cfg
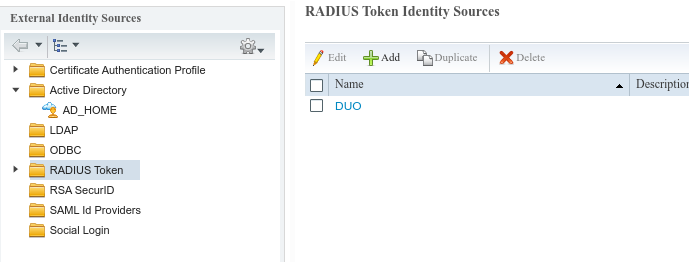
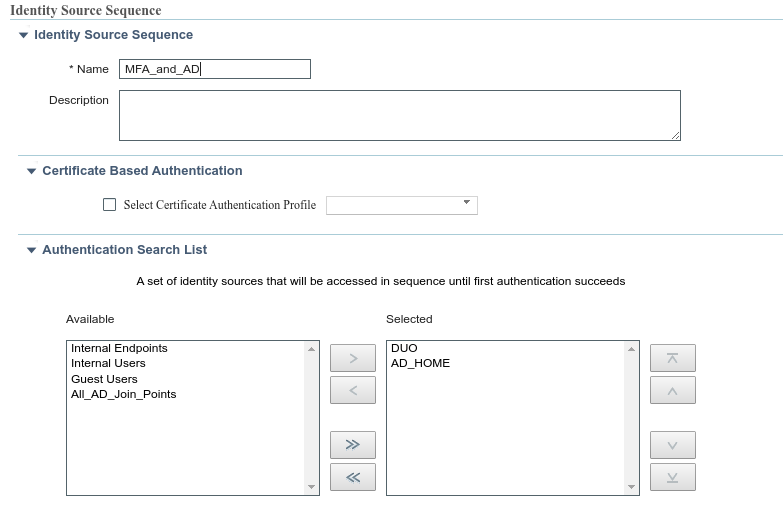
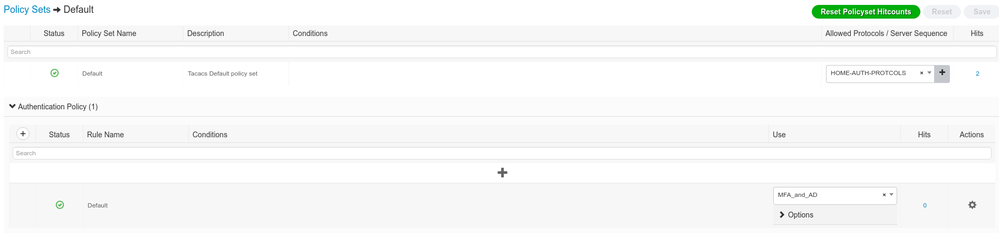
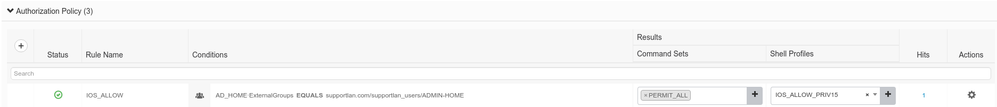
Then on your ISE, configure the Identity source sequence to have both your MFA Proxy Radius and AD and reference it in your authentication policy for tacacs. Rest of the configuration on the authorization side remains the same.
When you connect to your device, you enter your username and password, got a push from Duo you need to accept and you're connected.
You can increase the timeout to avoid any issues.
Hope this answers your question
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2020 06:49 PM - edited 05-19-2020 06:54 PM
Hi
You want to connect on a device using tacacs and getting a push from Duo for authentication and if ok then push a shell profile. If so then it is possible using the proxy radius which I believe you refer to Duo Proxy?
Below my authproxy.cfg
Then on your ISE, configure the Identity source sequence to have both your MFA Proxy Radius and AD and reference it in your authentication policy for tacacs. Rest of the configuration on the authorization side remains the same.
When you connect to your device, you enter your username and password, got a push from Duo you need to accept and you're connected.
You can increase the timeout to avoid any issues.
Hope this answers your question
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2020 11:58 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2020 08:29 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide