- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: ASA Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2018 12:34 AM
Hello,
I have asked a few questions during the past few months and there are still many issues with it.
I have always tried to configure the device via its ASDM software but there are just too many settings which don't make sense to me so I thought it might be a good idea to start over from scratch.
For example there are Network objects, that I don't even know what they are. They are IP addresses I have never seen before. But the ASA says they are in use. Very, very strange.
Is there a way to remove all nat rules? Then again what is the difference between access rules and nat rules, or maybe I should better ask: Why do we need NAT rules if the access rules already say that an interface with higher security level can access an interface with a lower security level?
OK, let's start with my objective:
I need at least 3 interfaces (I would call them networks):
1) Outside
2) Inside
3) DMZ
but since I have the security plus license, maybe we can configure 2 DMZs (for different VMs and other things) and one dedicated Wifi for guests.
Now, we need at least 2 VPN groups:
One for the Main Network and one for a DMZ network.
I am confident I can this up.
The issue is with the NAT. I do understand what NATing does if we talk about a router who needs to translate local IPs to public IPs. But why do we need NATing if say AnyConnect connects already to a DMZ and get a local IP from this network?
Other requirements are: The Main Network (Inside) should be able to connect to DMZ. The Guest Wifi doesn't connect anywhere except for the internet.
The device is an ASA 5505 with security plus license.
Could someone please help me with a working configuration? I was able to achieve most of the above but it just quit working from one day to the other.
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 03:46 PM
Eric
Thanks for posting the configuration. There are probably some issues which I do not understand very well yet. But I would like to start with these.
You identify that you would like a VPN user to access the Internet using the ASA. This means that an IP packet from the VPN user would arrive on the outside interface and you want the ASA to forward that packet back out the outside interface to access the Internet. This function is sometimes referred to as hair pinning. And by default the ASA does not support hair pinning. To enable this you need to permit same security level intra interface. The syntax would be
same-security-traffic permit intra-interface
You identify that the Guest wifi (dmz1) can access the Internet but the other dmzs can not. The reason for this is that you have configured an address translation for dmz1
nat (dmz1,outside) after-auto source dynamic any interface
but you have not configured any address translation for the other dmz interfaces. If you want the other dmz to access outside then you need to configure translations for them.
In addition to these things I would like to point out an issue with your access list
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
This beginning statement is followed by a number of statements permitting various types of traffic. But since an access list is processed in sequential order the effect of the first statement is to deny all traffic and none of the other access list entries will be processed. I do not see any reference to this access list in the config and so the access list may not have any impact. But if you are trying to use this access list you should correct this logic.
If there are other issues which you would like to address then please provide clarification about what these issues are.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2018 02:38 AM
Hello
Can you post the running configuration of the FW please so it can be reviewed
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2018 06:38 AM
Hello Paul,
I will post the running config tomorrow. Today I have created a second DMZ for the VMs and it behaves as expected, e.g. I can access it from the inside (Main LAN)
and the person who connects via AnyConnect can also access the resources. Only issue now: The VM on the DMZ can not connect to the internet. But since this one is used as a file server and running BSD, it doesn’t require internet most of the time, maybe just twice a year to update the OS. But it would be nice to get this one running as well.
regards,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2018 01:21 PM
If you have created the second DMZ and if you can access it from the LAN and the AnyConnect user can access it then it is working pretty well. There are a couple of things that might prevent devices on the DMZ from accessing the Internet. The most likely problem is that the devices in the DMZ are using private IP addressing and the ASA does not have any NAT configured for these devices. Another possible reason for no Internet access might be something in the access rules that are configured. Without seeing config details it is difficult for us to know what is the problem.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2018 05:20 AM
To Paul and all the others, I am very sorry for the delay, but here is the running config as for now.
The two most important things that I would like to achieve are
1) Allow VPN users (AnyConnect and IPSec) to access the Internet via the ASAs internet connection
→ Example: ASA is in Japan, I travel to another country, connect to a cafe's Wifi and establish an IPSec connection from my mobile phone. I can access the server at home but no internet. And I would like the phone to use the secure internet connection at home and not the cafe's potentially unprotected one. I search on the net suggested that
crypto isakmp nat-t
should solve this issue but unfortunately it doesn't.
2) As you can see from the running config, there are a few DMZs now. Currently the guest WiFi can connect to the internet. Which is good. The inside interface can connect to the DMZs. Which is good too. Now the newly created DMZs can not connect to the outside. I remember that I had to create a rule, an object, or whatever it is named in Cisco language to make that happen for the DMZ in which the guest WiFi is located. Before creating the other DMZs, most VMs were actually in the this DMZ which had a connection to the outside. But this caused troubled when I tried to remote into this VM as explained in the opening thread. So the choice was either allow connection to the outside or allow internal connection (from VPN to VM) but not both at the same time.
OK, long story. Here's the run-config of the device:
Result of the command: "show running-config"
: Saved
:
: Serial Number: JMX1XXXUY
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
:
ASA Version 9.1(7)23
!
hostname <hostname>
enable password Fggdfgfdggdggq5fzL encrypted
xlate per-session deny tcp any4 any4
xlate per-session deny tcp any4 any6
xlate per-session deny tcp any6 any4
xlate per-session deny tcp any6 any6
xlate per-session deny udp any4 any4 eq domain
xlate per-session deny udp any4 any6 eq domain
xlate per-session deny udp any6 any4 eq domain
xlate per-session deny udp any6 any6 eq domain
passwd 2KFQnbNIdI.2KYOU encrypted
names
ip local pool pool1 192.168.1.50-192.168.1.60 mask 255.255.255.0
ip local pool pool2 192.168.4.50-192.168.4.60 mask 255.255.255.0
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
switchport access vlan 13
!
interface Ethernet0/2
switchport trunk allowed vlan 1,3,23
switchport mode trunk
!
interface Ethernet0/3
!
interface Ethernet0/4
switchport access vlan 23
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
switchport trunk allowed vlan 1,3
switchport mode trunk
!
interface Vlan1
description LAN
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2
description OCN
nameif outside
security-level 0
pppoe client vpdn group ISP
ip address pppoe setroute
!
interface Vlan3
description DMZ, Guest Network
no forward interface Vlan1
nameif dmz1
security-level 50
ip address 192.168.2.1 255.255.255.0
!
interface Vlan13
description DMZ, GENERAL
nameif dmz2
security-level 50
ip address 192.168.3.1 255.255.255.0
!
interface Vlan23
description DMZ, VMs
nameif dmz3
security-level 50
ip address 192.168.4.1 255.255.255.0
!
boot system disk0:/asa917-23-k8.bin
ftp mode passive
clock timezone JST 9
dns domain-lookup inside
dns domain-lookup outside
dns domain-lookup dmz1
dns server-group DefaultDNS
name-server 1.1.1.1
name-server 8.8.8.8
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network NETWORK_OBJ_192.168.1.48_28
subnet 192.168.1.48 255.255.255.240
object network NETWORK_OBJ_192.168.4.48_28
subnet 192.168.4.48 255.255.255.240
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group network DMZ
network-object 192.168.2.0 255.255.255.0
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq lpd
access-list AnyConnect_Client_Local_Print remark IPP: Internet Printing Protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 631
access-list AnyConnect_Client_Local_Print remark Windows' printing port
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 9100
access-list AnyConnect_Client_Local_Print remark mDNS: multicast DNS protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.251 eq 5353
access-list AnyConnect_Client_Local_Print remark LLMNR: Link Local Multicast Name Resolution protocol
access-list AnyConnect_Client_Local_Print extended permit udp any4 host 224.0.0.252 eq 5355
access-list AnyConnect_Client_Local_Print remark TCP/NetBIOS protocol
access-list AnyConnect_Client_Local_Print extended permit tcp any4 any4 eq 137
access-list AnyConnect_Client_Local_Print extended permit udp any4 any4 eq netbios-ns
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu dmz1 1500
mtu dmz2 1500
mtu dmz3 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-781.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
nat (inside,outside) source static any any destination static NETWORK_OBJ_192.168.1.48_28 NETWORK_OBJ_192.168.1.48_28 no-proxy-arp route-lookup
nat (dmz3,outside) source static any any destination static NETWORK_OBJ_192.168.4.48_28 NETWORK_OBJ_192.168.4.48_28 no-proxy-arp route-lookup
!
object network obj_any
nat (inside,outside) dynamic interface
!
nat (dmz1,outside) after-auto source dynamic any interface
nat (any,any) after-auto source static DMZ DMZ destination static DMZ DMZ unidirectional inactive
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication http console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
crypto ca trustpoint ASDM_Launcher_Access_TrustPoint_0
enrollment self
fqdn none
subject-name CN=192.168.1.1,CN=ciscoasa
keypair ASDM_LAUNCHER
crl configure
crypto ca trustpool policy
crypto ca certificate chain ASDM_Launcher_Access_TrustPoint_0
certificate 9eaXXef9
308201c9 30820132 a0030201 020204c6 b82c5b30 0d06092a 864886f7 9eaXXef9
9eaXXef9 3111300f 06035504 9eaXXef9 6973636f 61736131 14301206 03550403
130b3139 322e3136 382e312e 9eaXXef9 0d313830 36323231 9eaXXef9 325a170d
32383036 31393134 9eaXXef92 5a302931 11300f06 03550403 13086369 73636f61
73613114 30120603 9eaXXef9 0b313932 2e313638 2e312e31 30819f30 0d06092a
864886f7 0d010101 05000381 8d003081 89028181 00b66a38 1c317465 e686271e
7b3947be 8301438a 90413d6e cae023bf 6071e5d7 9baec4da 9eaXXef9 e655d06d
9eaXXef9 e4b7f4d0 bc421679 35639f58 4feb2b36 024ff7e5 9eaXXef9 48552319
02c3f043 e3f0e0b4 07a2d652 9eaXXef9 25f9cdce 008f06e3 573022c5 9eaXXef9
9eaXXef9 d0d45fdf 01010505 01010505 73790b14 55020301 0001300d 06092a86
4886f70d 01010505 00038181 00a273bb 0101050590e6cdaf d5869d62 e571ad42
3035ab2c 9eaXXef9 6064ecfb cd6880c1 2d942f5e e029fe61 1f77fc0b 01010505
8fd8c098 9eaXXef9 01010505 c909f264 e5e85dd7 24bfeeeb 9fc80577 9eaXXef9
01010505 e7771083 7ffe0e92 01010505 99f9336d 1f777baa ed6b3890 27cfffb6
b3346809 d5b6576e e0ac3de1 1a
quit
no crypto isakmp nat-traversal
<<IMPORTANT: I don't know if the above entry was there before but I tried to enter crypto isakmp nat-traversal, I didn't do anything good for me, so I tried to revert it back to the previous setting - That's why I would like to use ASDM whenever possible>>
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication rsa-sig
encryption aes-256
hash sha
group 2
lifetime 86400
crypto ikev1 policy 40
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 50
authentication rsa-sig
encryption aes-192
hash sha
group 2
lifetime 86400
crypto ikev1 policy 70
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 80
authentication rsa-sig
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 100
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 110
authentication rsa-sig
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 130
authentication pre-share
encryption des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 140
authentication rsa-sig
encryption des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
management-access inside
vpdn group ISP request dialout pppoe
vpdn group ISP localname ??????@???.ocn.ne.jp
vpdn group ISP ppp authentication pap
vpdn username ??????@???.ocn.ne.jp password *****
dhcpd dns 1.1.1.1 8.8.8.8
dhcpd update dns both override
!
dhcpd address 192.168.1.??-192.168.1.?? inside
dhcpd enable inside
!
dhcpd address 192.168.2.??-192.168.2.?? dmz1
dhcpd enable dmz1
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
tftp-server inside 192.168.1.?? /
webvpn
enable outside
anyconnect image disk0:/anyconnect-win-4.4.03034-webdeploy-k9.pkg 1
anyconnect enable
tunnel-group-list enable
cache
disable
group-policy GroupPolicy_main_users internal
group-policy GroupPolicy_main_users attributes
wins-server none
dns-server value 1.1.1.1 8.8.8.8
vpn-tunnel-protocol ssl-client
default-domain none
group-policy GroupPolicy_dmz_users internal
group-policy GroupPolicy_dmz_users attributes
wins-server none
dns-server value 1.1.1.1 8.8.8.8
vpn-tunnel-protocol ssl-client
default-domain none
group-policy IPSecTunnel internal
group-policy IPSecTunnel attributes
dns-server value 1.1.1.1 8.8.8.8
vpn-tunnel-protocol ikev1
username<USERNAMEhere> password HGTHYxxwDZaf encrypted
username <USERNAMEhere> password YHNSTYj.O77lA encrypted
tunnel-group main_users type remote-access
tunnel-group main_users general-attributes
address-pool pool1
default-group-policy GroupPolicy_main_users
tunnel-group main_users webvpn-attributes
group-alias main_users enable
tunnel-group dmz_users type remote-access
tunnel-group dmz_users general-attributes
address-pool pool2
default-group-policy GroupPolicy_dmz_users
tunnel-group dmz_users webvpn-attributes
group-alias dmz_users enable
tunnel-group <HereIsATunnelName> type remote-access
tunnel-group <HereIsATunnelName> general-attributes
address-pool pool2
default-group-policy <HereIsATunnelName>
tunnel-group <ThisIsATunnelName> ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:XXXXXXXXXX18000XXXXXXXXXXf2bce
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 03:46 PM
Eric
Thanks for posting the configuration. There are probably some issues which I do not understand very well yet. But I would like to start with these.
You identify that you would like a VPN user to access the Internet using the ASA. This means that an IP packet from the VPN user would arrive on the outside interface and you want the ASA to forward that packet back out the outside interface to access the Internet. This function is sometimes referred to as hair pinning. And by default the ASA does not support hair pinning. To enable this you need to permit same security level intra interface. The syntax would be
same-security-traffic permit intra-interface
You identify that the Guest wifi (dmz1) can access the Internet but the other dmzs can not. The reason for this is that you have configured an address translation for dmz1
nat (dmz1,outside) after-auto source dynamic any interface
but you have not configured any address translation for the other dmz interfaces. If you want the other dmz to access outside then you need to configure translations for them.
In addition to these things I would like to point out an issue with your access list
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
This beginning statement is followed by a number of statements permitting various types of traffic. But since an access list is processed in sequential order the effect of the first statement is to deny all traffic and none of the other access list entries will be processed. I do not see any reference to this access list in the config and so the access list may not have any impact. But if you are trying to use this access list you should correct this logic.
If there are other issues which you would like to address then please provide clarification about what these issues are.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 11:39 PM
Richard,
First of all let me thank you for your detailed explanation.
There are a few settings that I don't know what they are for. For example the "Network Object" ending in ".48_24"
In ASDM it says it is used, however, there is no device in the network that has an IP ending in 48.
Disabling this entry in ASDM does render any VPN connection unusable so I turned it back on again.
I also don't know what the line "
access-list AnyConnect_Client_Local_Print extended deny ip any4 any4
"means. I have no access lists in place and printing is not denied - I can print if I remote into the main network without any problems.
Regarding the internet access, I suppose I used the following line for the guest WiFi. But I am a bit hesitant to aplly it to the DMZ (VMs) because when the VMs were in the guest Wifi DMZ, I had issues connecting to it via AnyConnect (or it filled the ARP table with entries ranging from 192.168.2.1 to 192.168.2.254).
Also, could you please explain what "same-security-traffic permit intra-interface" does exactly? I have asked a similar question some time ago and someone suggest something similar. I have tried it but it didn't work.
Here's the link to that post:
I would really appreciate if you can explain the above to me. Anyways, you have already well deserved that I select your answer as the solution to my question.
Regards,
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 06:34 AM
Eric
As far as your question about "Network Object" ending in ".48_24" it is correct that you do not have any device ending in 48. What you do have are two subnets that have 48 as their subnet address. These two subnets are used for the address pools for your two vpn groups. And if you disable these two subnets then certainly your vpn is going to stop working.
The access list line means that any ip version 4 packet will be denied. The effect of deny any any is that no packets will be permitted by the statements that follow in the access list. This would be a flaw in the construction of the access list. It may not have any impact on your ASA. One thing to remember is that configuring an access list is only the beginning of what you need to do. For the access list to work you also need to apply the access list to something. Since this access list is not applied to anything in the config then it is not doing anything. I point it out so that you would be aware of the potential issue. If you are not using that access list then I would suggest that you remove it from the config. And if it is something that you plan to use at some later time then you need to correct the logic in the access list (deny any any should be the last statement in the access list).
I am not sure what was going on with the nat statement. You indicate that you had attempted to use it for the VMs and it caused problems. I do not know what caused the problems but I do know that without a nat statement for the dmz for VMs that the VMs will not be able to access the Internet.
I remember reading the question you posted and the responses from Karsten. I did not post anything because I thought that Karsten had fairly well covered it. There were responses from some people who wanted to suggest split tunneling. What you asked in that question and are asking in this question is quite clear that you do not want split tunneling. What you want is full tunneling. With full tunneling an IP packet for the vpn arrives at the ASA outside interface and if it is a request for something in the Internet then the ASA needs to forward that packet back out the same outside interface. This is sometimes referred to as hairpinning. By default the ASA does not perform hairpinning and it must be enabled using the same-security command. In and out the same interface is intra interface. In one interface and out a different interface is inter interface. If that is still difficult to understand perhaps this discussion might help
https://learningnetwork.cisco.com/thread/20334
Karsten makes a good point that just permitting same-security traffic is not enough. You also need nat statements to translate the vpn pool addresses when they attempt to access the Internet.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-29-2018 03:25 PM
I do have set up two IP pools for VPN, however, all other devices have static IPs. No device uses 48.
Regarding the deny IPv4 lines, I don’t know where they come from but they obviously don’t make any sense. I do ,however, checked an option to prevent guest wifi users from accessing the inside interface.
I will try to provide more detailed information as soon as I get home from work.
Once again thank you for your help.
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 05:21 AM - edited 08-30-2018 05:25 AM
Rick
I am back home and can access the ASA now. So let's sum up a few things.
1.[Connection from DMZ3 (VMs) to Internet - SOLVED]
You have suggested to issue the following command
nat (dmz3,outside) after-auto source dynamic any interface
which now allows all VMs to access the internet and VPN connections are allowed into that zone. This was exactly what I asked for so I would consider this issue to be solved. Thank you.
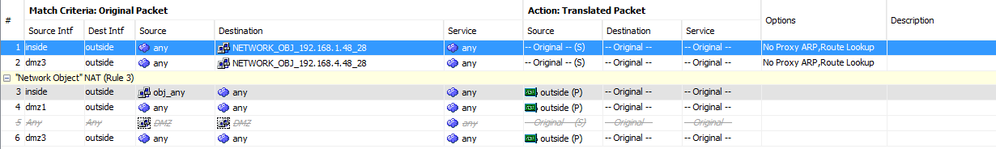
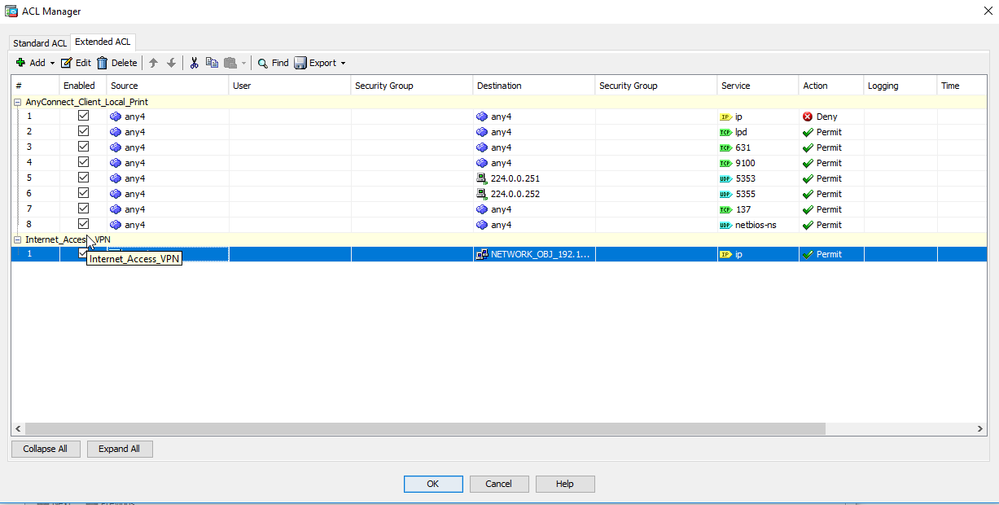
2.[The strange Network Object - OPEN]
As you can see from the picture above, the command to allow DMZ3 access to the internet has created a new NAT rule. In the picture this is #2. The destination is named "NETWORK_OBJ_192.168.4.48_28".
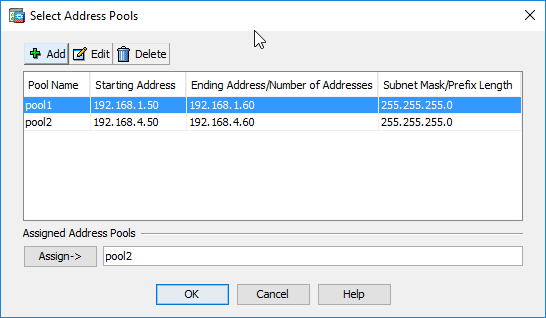
Where does this IP come from? The DMZ3 uses the 192.168.4.XXX range but all machines have their static IP - there is, however, an IP pool reserved for VPN access as shown in the picture below:
So there is no IP address ending in 48 here. All static IPs are ending in 3-digit numbers. Also, DMZ3 does not use DHCP.
ASDM reveals another strange object which is apparently being used for AnyConnect - removing it disables VPN access. It is an IP starting with 224, as you can see in the following picture.
3.[The IPv4 Deny rule - OPEN]
I found it on the system but I still don't know what it is for nor do I know how it got there.
I do have checked a box on the guest Wifi DMZ which says block traffic to inside interface. Guest Wifi is just what it says, just a connection to the internet and it doesn't require access to other networks.
Could it be possible the rule derives from this setting? Otherwise I have no clue. Can you teach me how to safely remove it if it's not used anywhere?
4.[Hairpinning (Internet over VPN) - OPEN]
To be honest, I have not tried your suggestion yet. You suggested the following command:
"same-security-traffic permit intra-interface"
Is this the same as any of the two checkboxes below? If so, I have tried them both in the past but it did not work. If not, is there any way to perform the settings in the GUI?
I would really appreciate if you could help me with these settings and I will do my best to learn more about how the system works. If you require any further information, please don't hesitate to ask me.
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 09:49 AM
Eric
I am glad that we are making progress. I am glad that the issue of access to Internet from dmz3 is solved.
I have tried to explain the strange network object NETWORK_OBJ_192.168.4.48_28 in a previous post but let me try again. There is not any device using an IP of 192.168.4.48 and the network object is not about any specific host. It is about the subnet used for your VPN pool. You have configured a pool of addresses beginning with 192.168.4.50 and ending with 192.168.4.60. That range of addresses is contained in subnet 192.168.4.48 255.255.255.240 (that subnet begins at 192.168.4.48 and ends at 192.168.4.63 so you can see that it does contain the addresses of yourVPN pool. And it is to be expected that no device uses address 48.
You ask about two network objects that are 224 addresses (224.0.0.251 and 224.0.0.252). Those objects are used in the access list
AnyConnect_Client_Local_Print
I have found many configurations for ASA that have this access list and assume that there are some Cisco configuration examples that have this access list and I assume that someone in configuring your ASA included this access list (and they added the deny any4 any4 statement which is not usually part of the config as I have seen it in other references). 224.0.0.251 port 5353 is documented as being for multicast DNS and 224.0.0.252 port 5355 is documented as being for Link Local Multicast Name Resolution. I am surprised that removing these objects disables VPN access but especially if this is the case I suggest that you leave those objects in the config and not worry about them.
I believe that the access deny rules that you ask about are not really the result of your checking the box to deny traffic from wifi dmz to inside. They are there because they define the default behavior of the ASA. That behavior is that a packet received on an interface which is going to a lower security level interface (for example coming into inside interface (security level 100) to dmz (security level 50) is permitted but that traffic going to a higher level interface (for example from dmz (security level 50) to inside (security level 100) would be denied. You should not attempt to remove these rules.
I believe that the second check box would accomplish the hair pinning. You tell us that you tried it before and it did not work. I suggest that the reason it did not work is that it is not the only thing that you need to do to enable Internet access for the VPN client. In the other question that you posted Karsten makes an important point that in addition to the same-security command that you also must configure address translation for the vpn pool addresses when they are going out the outside interface for Internet access.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2018 10:56 PM
Rick,
I want to thank you for your patience. I really do appreciate it.
Let me ask a few more questions, maybe I will eventually understand it.
We both agree that there is no device with an IP of 192.168.4.48 and that there is also no IP pool for the DHCP server that includes this address. So why exactly is this object named after a specific IP address that can never exist? I would maybe understand it if it was called 192.168.4.50...
Also, why was it created after I enabled internet access for DMZ3? This should not even involve VPN since the rule was
nat (dmz3,outside) after-auto source dynamic any interface
It is really confusing.
Regarding the 224.0.0.251 and 224.0.0.252 addresses, I will leave them alone for now.
Let's talk again about the hair pinning. You said that checking this box is not enough to achieve internet access through the tunnel and that I would require address translation. Can you explain me what exactly I would have to do to let an IPsec user who connects to DMZ3 also access the internet on the ASA through the tunnel?
Once again thank you very much for taking your time to try and explain things to me.
Eric
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-01-2018 10:18 AM
Eric
I do not understand why you are bringing the DHCP server into your question about 192.168.4.48. This has nothing to do with DHCP. It has to do with the pool of addresses for your VPN users. I am also a bit puzzled why you keep looking at it as a host address. I have tried multiple times to make the point that this is a subnet. Also it was not created when you enabled Internet access for DMZ3, this subnet is crucial to the operation of your VPN users.
I agree that you should not be concerned about the 224 addresses. Just leave them alone.
Lets talk a bit more about hair pinning. First let me review a couple of basic things about the ASA:
- by default the ASA does allow forwarding of packets from a higher security level to lower security level and does not allow forwarding from a lower security level to a higher security level.
- by default the ASA does not allow forwarding of a packet out the interface on which it was received.
- by default the ASA associates the addresses in the VPN pool with the outside interface.
- by default the ASA does allow packets from a VPN connection to access resources on other interfaces (which is an exception to the first rule above).
With those things in mind let us think of how some processing is done for a user VPN session.
First scenario - access for VPN to DMZ3
- some user in the Internet (with a public IP address from the Internet) establishes a VPN session to your ASA.
- that VPN session is assigned an IP address from the pool, perhaps it is assigned 192.168.4.53.
- The user wants to access some address in DMZ3. The ASA logic sees a packet from the outside interface with source address of 192.168.4.53 (not the user original Internet public IP) going to DMZ3 and this is permitted, so the ASA forwards the packet. The device in DMZ3 processes a packet with source address of 192.168.4.53, and sends a response to that address. The ASA takes the response from DMZ3 and forwards it to the user in the Internet (using the public IP).
- this works fine.
Second scenario - access for VPN to Internet
- some user in the Internet (with a public IP address from the Internet) establishes a VPN session to your ASA.
- that VPN session is assigned an IP address from the pool, perhaps it is assigned 192.168.4.53.
- The user wants to access some resource in the Internet. The ASA logic sees a packet from the outside interface with source address of 192.168.4.53 (not the user original Internet public IP) going to Internet on the outside interface and this is denied by the default behavior that you can not forward a packet back out the interface on which it was received.
- so you solve this issue by enabling same-security intra interface. This is the solution suggested by Karsten and by me.
Third scenario - access for VPN to Internet after enabling same-security intra interface
- some user in the Internet (with a public IP address from the Internet) establishes a VPN session to your ASA.
- that VPN session is assigned an IP address from the pool, perhaps it is assigned 192.168.4.53.
- The user wants to access some resource in the Internet. The ASA logic sees a packet from the outside interface with source address of 192.168.4.53 (not the user original Internet public IP) going to Internet on the outside interface and this is now permitted by the change we made. The ASA forwards the packet to the Internet provider device using source address 192.168.4.53. The Internet provider drops a packet with non routable source address.
- This is why just enabling same-security intra interface is not enough to allow Internet access.
- so you solve this issue by enabling address translation for VPN session attempting to access Internet resources.
I hope this helps you see more clearly what you need to do to permit Internet access for your VPN sessions.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-19-2019 08:33 PM
Hello Rick,
I am really sorry for the late reply, but I have been involved with a few other projects.
What you tried to explain makes sense, however, I still don't know how to make these settings. ASDM/ASA terminology and the UI itself is far away from being intuitive.
Under your last point
"Third scenario - access for VPN to Internet after enabling same-security intra interface"
...
you say
- so you solve this issue by enabling address translation for VPN session attempting to access Internet resources.
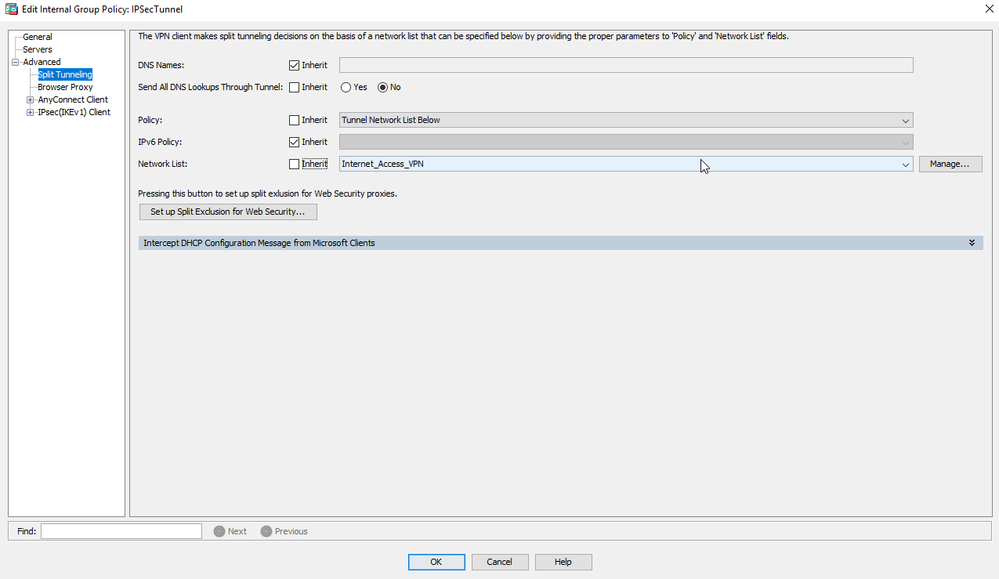
I have tried to do that by
(Even tried with different parameters regarding the DNS settings here)
And I even created a "Network List" as you can see
Please note that the AnyConnect group has always been there and was not created by me, nor do I exactly understand why it is there. But I suppose, it is related to the AnyConnect client.
Thanks in advance,
Eric
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide