- Cisco Community
- Technology and Support
- Networking
- Network Management
- Blocking direction for VLAN ingress router ACL and egress router ACL
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2021 02:12 AM - edited 12-04-2021 02:38 AM
Hi all,
Are the following statements correct on how the different ACL works?
- Router ACL as applied on a VLAN interface either Ingress or Egress
On VLAN Egress Router ACL (e-racl):
- All traffic towards the VLAN is allow (i.e. where destination is vlan)
- We need to craft statements to allow out-going traffic or return traffic (i.e. where source is vlan)
On VLAN Ingress Router ACL (racl):
- All traffic going out from VLAN is allow (i.e. where source is vlan)
- We need to craft statements to allow in-coming traffic (i.e. where destination is vlan)
I tried looking up all cisco documentation but there is no mention how egress/ingress router acl differs in ACL operations. If someone can point to me that location of this document it would be even better.
Many Thanks
Kelvin Wong
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2021 09:26 AM
Perhaps part of the confusion here is related to terminology and not all of us understanding certain terms in the same way. So let me suggest this way of understanding and clarifying terms. A layer 3 interface connects to a local subnet. By default all traffic originated from the local subnet is allowed to pass through the interface on its way to the remote destination. By default all traffic from remote sources is allowed to pass through the interface on its way to the local subnet. If we want to exert control over traffic originating from the local subnet we apply an access list IN on the interface and it permits or denies traffic as it passes through the interface on its way to the remote destinaiton. If we want to exert control over traffic originating from remote sources we apply an access list OUT on the interface and it permits or denies traffic as it passes through the interface on its way to the local subnet.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2021 02:41 AM
high level :
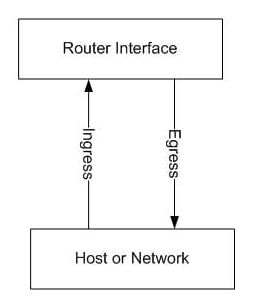
IN–when you are running traffic coming INTO the interface through an ACL.
OUT–when you are running traffic leaving the interface through an ACL.
ingress traffic flows from the network into the interface and egress flows from the interface to the network
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-03-2021 03:44 AM
Thanks for the reply,
Sorry for being really thick here as I am not really a certified CNA. I don't really understand what you mean. I am trying to understand practically how to apply the statements in real-life production systems
Basically I want to confirm the following:
- vlan egress racl --> by default all in-coming to vlan is allowed but out-going from vlan must be permitted in ACL (YES/NO?)
- vlan ingress racl --> by default all out-going from vlan is allowed but in-coming to vlan must be permitted in ACL (YES/NO?)
Assuming that I want to
- allow allowed_host to talk to any devices on the vlan (and vice versa)
- allow allowed_subnets to talk to any devices on the vlan (and vice versa)
- allow icmp ping from 10.10.1.0/24 subnet to any devices on vlan (and vice versa)
Are these correct statements that achieved the above 3 points
VLAN OUT egress RACL
config-if# ip access-group <ACL> out
********************
permit icmp ip 10.10.1.0/24 any echo-reply
permit ip addrgroup allowed_subnets any
permit ip addrgroup allowed_hosts any
deny ip any any
VLAN IN ingress RACL
config-if# ip access-group <ACL> in
********************
permit icmp ip any 10.10.1.0/24 echo-reply
permit ip any addrgroup allowed_subnets
permit ip any addrgroup allowed_hosts
deny ip any any
Many Thanks
Kelvin Wong
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2021 02:44 AM
There is a good reason for this ask. I have had a similar issue with ACLs in the past and NO CNA certified engineer from Cisco themselves could figure out which statements were correct when applied to e-racl. Yes, I repeat NOT A SINGLE engineer from Cisco understood how ingress racl nor egress racl really works after 1 week of escalation work. At the end of the day, it was up to someone like me who is not CNA certified to go back to first principals and figured it out myself.
The reason for this post is really want to confirm my understanding on this matter. I am hoping that there are more knowledgeable engineers out there who knows their stuff well enough to confirm my thoughts.
Many Thanks
Kelvin Wong
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2021 03:57 AM
Hello,
just to make sure: is your question related to Nexus switches and NX-OS ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-04-2021 06:06 PM - edited 12-04-2021 06:06 PM
Sorry about that, yes, I am talking about Nexus 3000 and 9000 series NXOS.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-06-2021 09:20 PM - edited 12-06-2021 09:21 PM
Hello
Routed vlan acl logic -When applied:
IN - traffic is originating from within the vlan
OUT- traffic is originating from outside vlan
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-09-2021 04:26 AM
Hi Paul,
Thanks for the clarifying this, so I guess this is what it means when writing ACL on nexus 3/9ks
IN - traffic is originating from within the vlan
- when writing ACL statement, we need to permit traffic to go out of vlan
- by default traffic is permitted to come into the vlan
OUT- traffic is originating from outside vlan
- when writing ACL statement, we need to permit traffic to come into the vlan
- by default traffic is permitted to exit the vlan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-11-2021 09:26 AM
Perhaps part of the confusion here is related to terminology and not all of us understanding certain terms in the same way. So let me suggest this way of understanding and clarifying terms. A layer 3 interface connects to a local subnet. By default all traffic originated from the local subnet is allowed to pass through the interface on its way to the remote destination. By default all traffic from remote sources is allowed to pass through the interface on its way to the local subnet. If we want to exert control over traffic originating from the local subnet we apply an access list IN on the interface and it permits or denies traffic as it passes through the interface on its way to the remote destinaiton. If we want to exert control over traffic originating from remote sources we apply an access list OUT on the interface and it permits or denies traffic as it passes through the interface on its way to the local subnet.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-13-2021 06:21 PM
I agree with you, but I think my curiosity is why did Cisco could not simply give examples in their docs to make the ACL usage practically especially for newbies and as I have experienced even Cisco support was confused on how the rules should apply. This situation even extends to colleagues within my organization who are experienced networking folks.
My aim was to confirm in a practical way on how ACL statements should be written either the IN or OUT side. However, IMHO, most of all that I got was some text book-like bot-like reply instead of directly answering to my questions. So far, even when I gave examples of how to write a practical statement, NOBODY answered my questions directly, even when I ask for yes/no questions, almost as if everyone is afraid of giving the wrong answer.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide