- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: Route GUEST network to different ISP
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2020 09:12 AM
Hello guys, I need some help on something I'm working on. I'm trying to route the GUEST network to a specific ISP gateway and need some help on how to do this. Currently I have the current network going out to a 3850 then to a PA firewall, then to ISP 1 router. We have a 2nd router (ISP 2) which handles GUEST traffic and the ISP installed their own AP's. I have a GUEST network currently working but going through the ISP 1 router, is there a way i can route the GUEST network to ISP 2 and getting the traffic to go through the 3850 and from there to the firewall to apply URL filtering?
I made some research on this and though on using PBR but wanted to know if there is another way of doing this.
Solved! Go to Solution.
- Labels:
-
Network Management
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2020 08:07 AM
There are a few things that we do not know and they might change some aspects of the answer. Do you want Guest2 to be able to communicate with anything inside your network or does all traffic from Guest2 go to ISP2? You gave us the outbound interface but not the next hop address. But based on what we know so far here are some suggestions that I hope will help.
- first I want to make the point that PBR provides an over ride of the normal routing logic to forward IP packets. It is implemented with a route map that is applied to the interface where the traffic enters the router/switch that is routing the subnet. So assuming that the 3850 is providing routing for Guest2 on vlan 99 the config might look something like this:
- configure an access list to identify the traffic to be forwarded by PBR
access-list 101 permit ip 192.168.99.0 00.0.255 any
- configure a route map to use the acl and set the next hop address
route-map PBR permit 1
match ip address 101
set ip next-hop <next hop address>
- apply the route map to the interface
interface vlan 99
ip policy route-map PBR
Here is a link with additional information which I hope you will find helpful
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2020 12:03 PM
high level - it all depends on how you rouitng the Traffiic, you can route the guest IP address range using PBR(Policy base routing) on Palo to take decision and NAT to ISP2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2020 02:35 PM
Is there something else besides PBR or is that the only solution here?
I just want to see what options I have before I start testing it out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-29-2020 09:38 AM
You can do Static routing also but you will have failure route has other effects, with PBR you can make a routing decesion. how you want to route if the ISP2 fails route to ISP1 if that is the requirement.
spend some time think, how you like to have Traffic engineering for best optimisation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 08:10 AM
The topology of this network is not clear and that impacts our ability to give good advice. The original post describes some network which goes through a 3850 to a PA firewall and then to ISP1. The original post talks about a second router to handle the Guest network and says the Guest network currently goes through the router to ISP1 and asks if it is possible to route the Guest traffic to ISP2. We do not know how the Guest network is set up. Is the Guest network on the same switch as the current network? Or on a separate switch? A separate switch would seem to be pretty easy - can you just move the switch connection to the second router? If both networks are on the same switch perhaps it might be possible to establish an access port on the switch to the second router, configure the second router to route the Guest network, and to remove the SVI for the Guest network from the 3850.
There is one part of the question that I find puzzling: "is there a way i can route the GUEST network to ISP 2 and getting the traffic to go through the 3850 and from there to the firewall to apply URL filtering" Is this the same PA firewall used for the established network? So do you want to send all of the traffic to the PA firewall and then have the PA firewall separate the traffic sending the established network to ISP1 and Guest to ISP2? That would require logic on the PA which we are not in a good position to evaluate.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 08:48 AM - edited 04-30-2020 08:52 AM
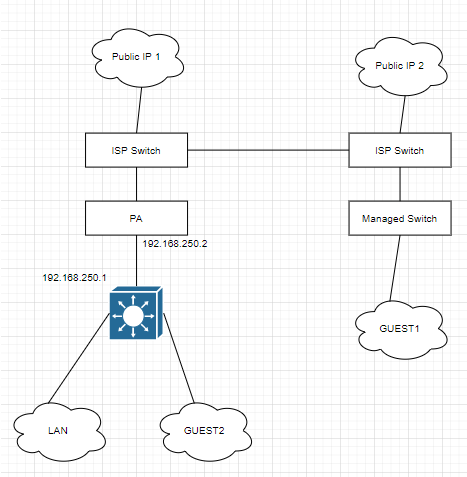
I apologize for the confusion, here is the topology of what I have. The managed switch it's managed by the ISP, the AP's on GUEST1 are also managed by the ISP. I created GUEST2 using our AP's. As you can see we have 2 public IP's, I want to implement only one guest network but keep our internal traffic going to Public IP 1, and GUEST2 traffic to Public IP 2. The PA is capable of NAT and has VR (Virtual Router) which has the IP of 192.168.250.2 which is NATing to Public IP 1. My plan is to create a 2nd VR with 192.168.250.3 and NAT to Public IP 2. My doubt is how can I route say VLAN X (GUEST2) to use that Public IP 2 since on the core switch I'm using EIGRP and the gateway of last resort is pointing to 192.168.250.2.
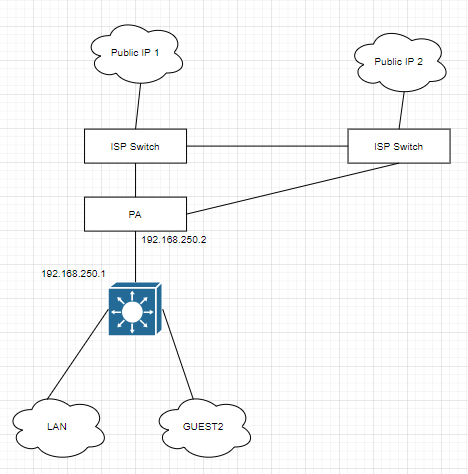
The bottom image is what I'm trying to accomplish, I talked with our ISP and we might be able to use the Left ISP switch for the 2nd Public IP so we can get rid of the 2nd ISP switch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 11:38 AM
Thanks for the additional information. Based on the drawing and making a couple of assumptions it looks like sending Guest1 out using Public IP 2 would be quite possible. But if I understand your explanation correctly Guest1 is going away and you will be using Guest2. That will be a bit more challenging. Achieving your result will depend on what PA can do and I do not have enough expertise with PA to be able to address that part of your requirements. If it were a Cisco device I would say use Policy Based Routing and we should be able to achieve your requirement.
If you get the PA to implement VR2 with 192.168.250.3 it should be possible on your 3850 to use PBR and forward Guest2 traffic to VR2 while your internal traffic continues to use the gateway of 192.168.250.2. Perhaps that might allow PA to nat and forward Guest2 separately from your internal traffic.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2020 02:35 PM
Correct, I'm trying to route GUEST 2 to ISP 2 and will be getting rid of GUEST 1, I just have a few doubts on how to implement PBR.
Do I implement PBR or on the outgoing interface which connects the 3850 to the PA?
Could you give me an example of a PBR config of what I'm trying to do?
Say I have VLAN 99 (GUEST) -> Network 192.168.99.0/24 & ISP 2nd Public IP -> 9.9.9.9
3850 Outgoing Interface Gig 1/0/1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2020 08:07 AM
There are a few things that we do not know and they might change some aspects of the answer. Do you want Guest2 to be able to communicate with anything inside your network or does all traffic from Guest2 go to ISP2? You gave us the outbound interface but not the next hop address. But based on what we know so far here are some suggestions that I hope will help.
- first I want to make the point that PBR provides an over ride of the normal routing logic to forward IP packets. It is implemented with a route map that is applied to the interface where the traffic enters the router/switch that is routing the subnet. So assuming that the 3850 is providing routing for Guest2 on vlan 99 the config might look something like this:
- configure an access list to identify the traffic to be forwarded by PBR
access-list 101 permit ip 192.168.99.0 00.0.255 any
- configure a route map to use the acl and set the next hop address
route-map PBR permit 1
match ip address 101
set ip next-hop <next hop address>
- apply the route map to the interface
interface vlan 99
ip policy route-map PBR
Here is a link with additional information which I hope you will find helpful
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-19-2020 05:06 PM
I am glad that my suggestions were helpful. Thank you for marking this question as solved. This will help other participants in the community to identify discussions which have helpful information. This community is an excellent place to ask questions and to learn about networking. I hope to see you continue to be active in the community.
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide