- Cisco Community
- Technology and Support
- Networking
- Network Management
- Re: ZBFW - Tunnels with ISAKMP go down
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ZBFW - Tunnels with ISAKMP go down
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2020 10:36 AM
Hello,
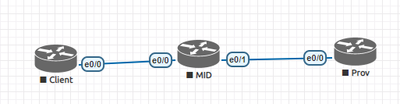
I have a network which the topology is similar to the following:
In the topology there are two tunnels with ISAKMP and IPSec configured between the Client router and the Prov router.
The client asked me to configure ZBFW in the MID router, with the idea of letting the administrator to access from the MID router, or the Prov router, to the Client router using Ping o ssh, with the condition that nobody can use ssh or ping from the Client router to the MID router or from the Client router to the Prov router.
To do this, I have tried to configure the MID routers by two different ways, but in both situations the tunnels go down. I cannot understand why this is happening, and what should I do to solve it.
The following are the two ways to configure the router that I have tried:
First
class-map type inspect match-any Prov-TO-Client-CLASS
match protocol udp
match protocol tcp
match protocol ssh
match protocol icmp
match protocol isakmp
match protocol pptp
!
class-map type inspect match-any Client-TO-Prov-CLASS
match protocol udp
match protocol tcp
match protocol isakmp
match protocol pptp
!
ip access-list extended ISAKMP_IPSEC
permit gre any any
permit udp any any eq isakmp
permit ahp any any
permit esp any any
permit udp any any eq non500-isakmp
!
class-map type inspect match-all CLASS-ACL-Prov-TO-Client
match access-group name ISAKMP_IPSEC
!
class-map type inspect match-all Client-TO-Prov-CLASS-ACL
match access-group name ISAKMP_IPSEC
!
policy-map type inspect Client-TO-Prov-POLICY
class type inspect Client-TO-Prov-CLASS
inspect
class type inspect Client-TO-Prov-CLASS-ACL
pass
class class-default
drop
!
policy-map type inspect Prov-TO-Client-POLICY
class type inspect Prov-TO-Client-CLASS
inspect
class type inspect CLASS-ACL-Prov-TO-Client
pass
class class-default
drop
!
zone security Prov
zone security Client
zone-pair security Prov-TO-Client source Prov destination Client
service-policy type inspect Prov-TO-Client-POLICY
!
zone-pair security Client-TO-Prov source Client destination Prov
service-policy type inspect Client-TO-Prov-POLICY
!
interface Ethernet0/0
zone-member security Client
!
interface Ethernet0/1
zone-member security Prov
!
Second
class-map type inspect match-any Prov-TO-Client-PROTO
match protocol udp
match protocol tcp
match protocol ssh
match protocol icmp
match protocol isakmp
match protocol pptp
!
class-map type inspect match-any Client-TO-Prov-PROTO
match protocol udp
match protocol tcp
match protocol isakmp
match protocol pptp
!
ip access-list extended ISAKMP_IPSEC
permit gre any any
permit udp any any eq isakmp
permit ahp any any
permit esp any any
permit udp any any eq non500-isakmp
!
class-map type inspect match-all CLASS-Prov-TO-Client
match access-group name ISAKMP_IPSEC
match class-map Prov-TO-Client-PROTO
!
class-map type inspect match-all CLASS-Client-TO-Prov
match access-group name ISAKMP_IPSEC
match class-map Client-TO-Prov-PROTO
!
policy-map type inspect Client-TO-Prov-POLICY
class type inspect CLASS-Client-TO-Prov
inspect
class class-default
drop
!
policy-map type inspect Prov-TO-Client-POLICY
class type inspect CLASS-Prov-TO-Client
inspect
class class-default
drop
!
zone security Prov
zone security Client
zone-pair security Prov-TO-Client source Prov destination Client
service-policy type inspect Prov-TO-Client-POLICY
!
zone-pair security Client-TO-Prov source Client destination Prov
service-policy type inspect Client-TO-Prov-POLICY
!
interface Ethernet0/0
zone-member security Client
!
interface Ethernet0/1
zone-member security Prov
!
Thank you for your support,
Franco Riggio
- Labels:
-
Network Management
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2020 11:54 AM
Hello,
Which version your simulator?
BR
Yan Bedia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-02-2020 12:11 PM
Hello,
I have used a simulator to show how is the topology, but for this solution I am using a Cisco 4321 as the MID router.
Thank you for your support,
Franco Riggio
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2020 05:46 AM
Hello,
you need to 'pass' GRE and ESP in both directions. Use the config below:
class-map type inspect match-any PROV-TO-CLIENT-CM
match protocol udp
match protocol tcp
match protocol ssh
match protocol icmp
match protocol isakmp
match protocol pptp
match access-group name ISAKMP-IPSEC-ACL
!
class-map type inspect match-any CLIENT-TO-PROV-CM
match protocol udp
match protocol tcp
match protocol isakmp
match protocol pptp
match access-group name ISAKMP-IPSEC-ACL
!
class-map type inspect match-any GRE-ESP-CM
match access-group name GRE-ESP-ACL
!
ip access-list extended ISAKMP-IPSEC-ACL
permit udp any any eq isakmp
permit ahp any any
permit udp any any eq non500-isakmp
!
ip access-list extended GRE-ESP-ACL
permit gre any any
permit esp any any
!
policy-map type inspect CLIENT-TO-PROV-PM
class type inspect CLIENT-TO-PROV-CM
inspect
class type inspect GRE-ESP-CM
pass
class class-default
drop
!
policy-map type inspect PROV-TO-CLIENT-PM
class type inspect PROV-TO-CLIENT-CM
inspect
class type inspect GRE-ESP-CM
pass
class class-default
drop
!
zone security PROV
zone security CLIENT
zone-pair security PROV-TO-CLIENT-ZP source PROV destination CLIENT
service-policy type inspect PROV-TO-CLIENT-PM
!
zone-pair security CLIENT-TO-PROV-ZP source CLIENT destination PROV
service-policy type inspect CLIENT-TO-PROV-PM
!
interface Ethernet0/0
zone-member security CLIENT
!
interface Ethernet0/1
zone-member security PROV
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-03-2020 07:48 AM - edited 10-27-2020 06:18 AM
Hello Georg,
After a couple of tests in the client's lab, I could configure ZBFW with the idea of letting pass SSH, TCP, UDP or ICMP traffic from the client's side to the Prov side, with the condition that the tunnel configured between the Client router and the Prov router still works!
I have done the following:
class-map type inspect match-any PROV-TO-CLIENT-CM
match protocol udp
match protocol tcp
match protocol ssh
match protocol icmp
match protocol isakmp
match protocol pptp
match access-group name ISAKMP-IPSEC-ACL
!
class-map type inspect match-any CLIENT-TO-PROV-CM
match protocol isakmp
match protocol pptp
match access-group name ISAKMP-IPSEC-ACL
!
class-map type inspect match-any GRE-ESP-CM
match access-group name GRE-ESP-ACL
!
ip access-list extended ISAKMP-IPSEC-ACL
permit udp any any eq isakmp
permit ahp any any
!
ip access-list extended GRE-ESP-ACL
permit gre any any
permit esp any any
!
policy-map type inspect CLIENT-TO-PROV-PM
class type inspect CLIENT-TO-PROV-CM
inspect
class type inspect GRE-ESP-CM
pass
class class-default
drop
!
policy-map type inspect PROV-TO-CLIENT-PM
class type inspect PROV-TO-CLIENT-CM
inspect
class type inspect GRE-ESP-CM
pass
class class-default
drop
!
zone security PROV
zone security CLIENT
zone-pair security PROV-TO-CLIENT-ZP source PROV destination CLIENT
service-policy type inspect PROV-TO-CLIENT-PM
!
zone-pair security MID-TO-CLIENT-ZP source self destination CLIENT
service-policy type inspect PROV-TO-CLIENT-PM
!
zone-pair security CLIENT-TO-PROV-ZP source CLIENT destination PROV
service-policy type inspect CLIENT-TO-PROV-PM
!
zone-pair security CLIENT-TO-MID-ZP source CLIENT destination self
service-policy type inspect CLIENT-TO-PROV-PM
!
interface Ethernet0/0
zone-member security CLIENT
!
interface Ethernet0/1
zone-member security PROV
When I configured it the first time, I made a mistake and I discovered it later.
Thank you for your support,
Franco Riggio
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide