- Cisco Community
- Technology and Support
- Security
- Network Security
- can not reach dmz
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
can not reach dmz
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 01:37 AM - edited 03-11-2019 05:23 PM
Dear All,
I have the following topology:
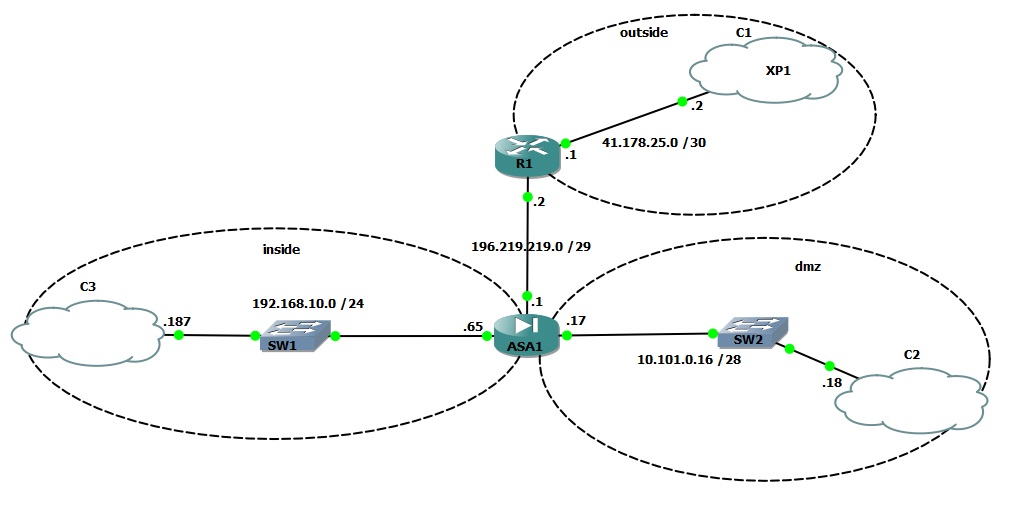
ASA Config as following:
MyASA(config)# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname MyASA
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 196.219.219.1 255.255.255.248
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.10.65 255.255.255.0
!
interface Ethernet0/2
nameif dmz
security-level 70
ip address 10.101.0.17 255.255.255.240
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
boot config disk0:/.private/startup-config
ftp mode passive
access-list inside_acl extended permit icmp any host 196.219.219.3
access-list inside_acl extended permit tcp any host 196.219.219.3 eq https
access-list inside_acl extended permit tcp any host 196.219.219.5 eq www
access-list inside_acl extended permit icmp any host 196.219.219.5
pager lines 24
mtu outside 1500
mtu inside 1500
mtu dmz 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any echo-reply outside
no asdm history enable
arp timeout 14400
nat-control
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) 196.219.219.3 192.168.10.187 netmask 255.255.255.255
static (dmz,outside) 196.219.219.5 10.101.0.18 netmask 255.255.255.255
static (dmz,inside) 192.168.10.50 10.101.0.18 netmask 255.255.255.255
access-group inside_acl in interface outside
route outside 41.178.25.0 255.255.255.0 196.219.219.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
no crypto isakmp nat-traversal
telnet 192.168.10.0 255.255.255.0 inside
telnet timeout 15
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map global_policy
class inspection_default
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
inspect icmp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:a41e50d1e8b70379a3f1a8b47a3ab160
: end
and router Config as following if you need:
R1#sh run
Building configuration...
Current configuration : 1169 bytes
!
upgrade fpd auto
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
ip cef
!
!
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
!
no ip domain lookup
ip domain name lab.local
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
!
!
!
!
!
!
archive
log config
hidekeys
!
!
!
!
!
!
!
!
interface Ethernet0/0
no ip address
shutdown
duplex auto
!
interface GigabitEthernet0/0
no ip address
shutdown
duplex full
speed 1000
media-type gbic
negotiation auto
!
interface FastEthernet1/0
ip address 196.219.219.2 255.255.255.248
duplex auto
speed auto
!
interface FastEthernet1/1
ip address 41.178.25.1 255.255.255.252
duplex auto
speed auto
!
ip forward-protocol nd
no ip http server
no ip http secure-server
!
!
!
logging alarm informational
!
!
!
!
!
control-plane
!
!
!
!
!
!
gatekeeper
shutdown
!
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
stopbits 1
line vty 0 4
login
!
!
end
R1#
from ASA I can ping all these PCs (can be reached), C2 is a web server can be accessed from the outside by the natted IP"196.219.219.5". but, the inside PC can not access, or ping this server by the natted IP "192.168.10.50".. why?
Thanks
Omar Mahmoud
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2012 01:53 AM
Hi Omar,
Please go through the link below:
http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_tech_note09186a0080094aad.shtml
Create a static translation between the entire inside network and the DMZ that does not actually translate inside addresses.
static (inside,dmz) 10.1.6.0 10.1.6.0 netmask 255.255.255.0
Create a static translation to allow one inside host access to the DMZ without actually translating the address of the host.
static (inside,dmz) 10.1.6.100 10.1.6.100 255.255.255.255
If you have a public address on the inside network, and you want the inside hosts to go out to the outside without translation, you can disable NAT. You also need to change the static command.
Using the the nat command changes as this output shows:
nat (inside) 0 175.1.1.0 255.255.255.0
Use these commands if you use ACLs in PIX software versions 5.0.1 and later:
access-list 103 permit ip 175.1.1.0 255.255.255.0 any nat (inside) 0 access-list 103
This command disables NAT for the 175.1.1.0 network. The static command for the web server changes as this output shows:
static (inside, outside) 175.1.1.254 175.1.1.254
This command defines the conduit for the web server.
conduit permit tcp host 175.1.1.254 eq www any
Use these commands if you use ACLs in PIX software versions 5.0.1 and later:
access-list 102 permit tcp any host 175.1.1.254 eq www access-group 102 in interface outside
Please rate helpful posts
Regards
Thanveer
"Everybody is genius. But if you judge a fish by its ability to climb a tree, it will live its whole life believing that it is a stupid."
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
