- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Cannot route leased line traffic from third interface to LAN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cannot route leased line traffic from third interface to LAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2018 08:22 AM - edited 02-21-2020 08:08 AM
Hello,
I'm new to the community and hoping someone can shed some light on my issue. I have a leased line coming in to connect two sites, Right now I have an ASA 5508-X that I'm preparing to use for one site.
The sites are set up as follows: SiteA, SiteB SiteC and SiteD
SiteC and SiteD are both connected to SiteB via a Site-To-Site VPN connection. SiteA and SiteB will have the leased line between them. I am working on the ASA for SiteA.
The issue I seem to have is I cannot ping traffic from the inside interface to the SiteC network. I can, (Or at least I could) ping from the leased line interface to SiteC.
Ultimately I'd like to get SiteA to access all the other sites. Here's my config so far:
!
interface GigabitEthernet1/1
nameif outside
security-level 0
ip address 10.0.10.1 255.0.0.0
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
!
interface GigabitEthernet1/3
nameif LeasedLine
security-level 0
ip address 192.168.254.249 255.255.255.252
!
interface GigabitEthernet1/4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/5
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/6
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
nameif mgmt
security-level 0
ip address 192.168.45.45 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name corp.corporate.com
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network SiteB
subnet 192.168.3.0 255.255.255.0
object network LEASE-LeasedLine-GW
host 192.168.254.250
description LEASE LeasedLine GATEWAY
object network SiteC
subnet 192.168.9.0 255.255.255.0
description SiteC-NETWORK
object network SiteD
subnet 192.168.0.0 255.255.254.0
description Core Office
object network inside-network
subnet 192.168.2.0 255.255.255.0
access-list alert-interval 3600
access-list LeasedLine_access_in extended permit ip any any
access-list global_access extended permit ip object inside-network any
access-list global_access extended permit ip object SiteB object inside-network
pager lines 24
logging enable
logging asdm debugging
mtu outside 1500
mtu inside 1500
mtu LeasedLine 1500
mtu mgmt 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
nat (LeasedLine,inside) source static SiteB SiteB destination static inside-network inside-network no-proxy-arp
nat (inside,LeasedLine) source static inside-network inside-network destination static SiteB SiteB no-proxy-arp
!
nat (inside,outside) after-auto source dynamic any interface
access-group LeasedLine_access_in in interface LeasedLine
access-group global_access global
route outside 0.0.0.0 0.0.0.0 10.0.0.1 1
route LeasedLine 192.168.0.0 255.255.254.0 192.168.254.250 1
route LeasedLine 192.168.3.0 255.255.255.0 192.168.254.250 1
route LeasedLine 192.168.9.0 255.255.255.0 192.168.254.250 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
timeout igp stale-route 0:01:10
user-identity default-domain LOCAL
aaa authentication http console LOCAL
aaa authentication login-history
http server enable
http 192.168.1.0 255.255.255.0 inside
http 0.0.0.0 0.0.0.0 inside
http 0.0.0.0 0.0.0.0 mgmt
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
threat-detection statistics tcp-intercept rate-interval 30 burst-rate 400 average-rate 200
dynamic-access-policy-record DfltAccessPolicy
username admin password
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
hpm topN enable
Cryptochecksum:
Thanks for any input.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2018 12:25 AM
Hello,
You can not source the traffic from inside interface of ASA A and ping across any other interface. This is true unless you are running a vpn between site A and site B, which is not the case. This is a security feature.
If you have a host/server connected behind the inside interface of ASA A, you should be able to reach site C or D if the connectivity is established.
HTH
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2018 02:18 AM
inside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 08:25 AM
Right now I have a basic router attached directly to the leased line interface. I can ping from inside the asa over the leased line interface to the SiteA.
My explanation was a little confusing. Since SiteA and SiteB are connected via the leased line, I meant to say that SiteB can be pinged, but I cannot ping from SiteB to SiteA. I also cannot seem to pass traffic from SiteB to SiteA. I can, however initiate a request from SiteA and get to SiteB.
Sites C and D are not important yet, I need to get A and B working, then I can work on the others.
I guess my question would be am I going about this the correct way? Should I be putting other hardware in place instead of just an ASA? Should the MPLS circuit be inside my network and not directly attached to the ASA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-27-2018 11:16 PM
Hello,
Can you please attach a rough topology so that we can understand the topology better.
Thanks,
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 09:54 AM
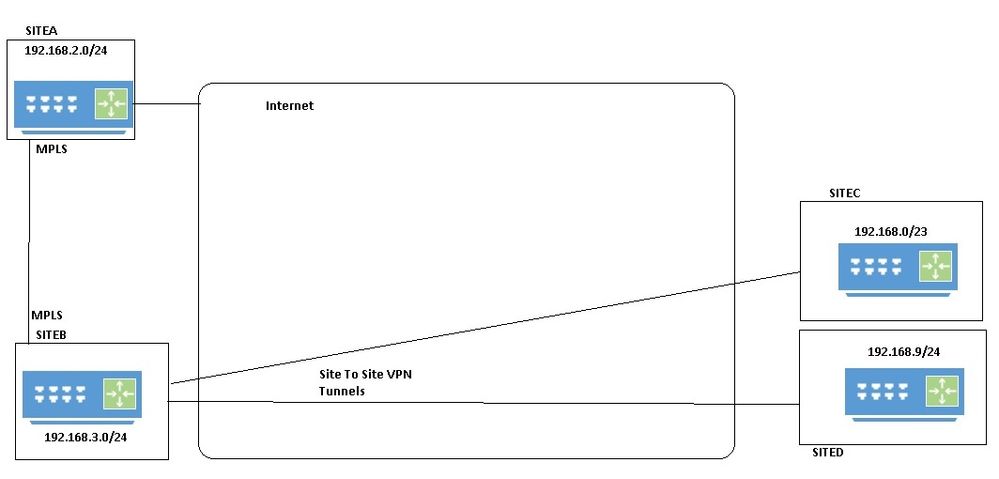
Here is is quick and dirty explanation of the network. MPLS lines are proposed and not working. Everything else is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2018 01:39 PM
Hello,
The way I have in my organization is that MPLS is terminating on a dedicated router and route pointing to to the core switch. The core switch default gateway points to ASA and specific routes point to MPLS router for any traffic that needs to go over the MPLS links. I am not sure if you have a mesh topology.
If this is supposed to be a full mesh topology, better to have a router for this purpose terminating the MPLS links.
In your case, if you need help, please provide the complete config for all the device from site A and site B and the source and destination ip addresses. We need to troubleshoot this hop by hop.
Thanks,
AJ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-30-2018 03:08 PM
This is not a true mesh topology.
At this point I don't mind putting a router behind the ASA and handling the routing there. I was reading an article that appears to be appropriate:
http://wiki-see.info/wp/category/firewalsl/cisco-asa/page/2/
I was looking at the article titled "TCP State bypass on a Cisco ASA" This seems to apply to my situation.
The remote networks are flat. No layer-3 and there is no way to put in a layer 3 network (budgets!).
If anyone has an opinion on this, please share it.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide