- Cisco Community
- Technology and Support
- Security
- Network Security
- Cisco ASA 5506-X PAT to interface problem
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-04-2020 05:10 AM - edited 03-04-2020 06:43 AM
Hi people,
I hope somebody can help me. I don't know what to do =(
Cisco ASA5506-X (9.9(2)36)
I have 3 outside interfaces: two for internet (security level 0) and third one (name 'bft', security level 10, but I tried set 0 as well) connected to corporate network (10.0.0.0/8). + inside interface (192.168.111.0/24, sec.level 100)
When I create PAT to my 'BFT' interface I can't access it from other side of corporate network;
nat (inside,bft) 46 source static 192.168.111.250 interface destination static bft-network bft-network service tcp3389 tcp65123
, where bft-network = 10.0.0.0/8
TCP request discarded from 10.1.36.126/59802 to bft:10.1.11.30/65123
I applied allow any IP traffic on all my interfaces, but without luck.
If I ping 10.1.11.30 or access ASDM/SSH ports - no problems.
packet-tracer input bft tcp 10.1.36.126 59802 10.1.11.30 65123 detailed:
Phase: 1
Type: ROUTE-LOOKUP
Subtype: Resolve Egress Interface
Result: ALLOW
Config:
Additional Information:
found next-hop 10.1.11.30 using egress ifc identity
Phase: 2
Type: NAT
Subtype: per-session
Result: ALLOW
Config:
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac19858c0, priority=0, domain=nat-per-session, deny=false
hits=11579208, user_data=0x0, cs_id=0x0, reverse, use_real_addr, flags=0x0, protocol=6
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=any, output_ifc=any
Phase: 3
Type: ACCESS-LIST
Subtype:
Result: DROP
Config:
Implicit Rule
Additional Information:
Forward Flow based lookup yields rule:
in id=0x2aaac2c6a640, priority=0, domain=permit, deny=true
hits=130, user_data=0xa, cs_id=0x0, use_real_addr, flags=0x1000, protocol=0
src ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any
dst ip/id=0.0.0.0, mask=0.0.0.0, port=0, tag=any, dscp=0x0
input_ifc=bft, output_ifc=any
Result:
input-interface: bft
input-status: up
input-line-status: up
output-interface: NP Identity Ifc
Action: drop
Drop-reason: (acl-drop) Flow is denied by configured rulepacket-tracer input bft icmp 10.1.36.126 8 0 10.1.11.30
Phase: 1 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 10.1.11.30 using egress ifc identity Phase: 2 Type: ACCESS-LIST Subtype: Result: ALLOW Config: Implicit Rule Additional Information: Phase: 3 Type: NAT Subtype: per-session Result: ALLOW Config: Additional Information: Phase: 4 Type: IP-OPTIONS Subtype: Result: ALLOW Config: Additional Information: Phase: 5 Type: CLUSTER-REDIRECT Subtype: cluster-redirect Result: ALLOW Config: Additional Information: Phase: 6 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: Additional Information: Phase: 7 Type: INSPECT Subtype: np-inspect Result: ALLOW Config: Additional Information: Phase: 8 Type: VPN Subtype: ipsec-tunnel-flow Result: ALLOW Config: Additional Information: Phase: 9 Type: FLOW-CREATION Subtype: Result: ALLOW Config: Additional Information: New flow created with id 10969831, packet dispatched to next module Phase: 10 Type: ROUTE-LOOKUP Subtype: Resolve Egress Interface Result: ALLOW Config: Additional Information: found next-hop 0.0.0.0 using egress ifc identity Phase: 11 Type: ADJACENCY-LOOKUP Subtype: next-hop and adjacency Result: ALLOW Config: Additional Information: adjacency Active next-hop mac address 0000.0000.0000 hits 3167600 reference 119 Result: input-interface: bft input-status: up input-line-status: up output-interface: NP Identity Ifc Action: allow
If I make PAT not into BFT interface, but into additional IP address on the interface - PAT works!
I have no problem with PAT to others uplink interfaces.
Tried the same scenario on my second ASA 5506-X version 9.8.2.20 without luck.
Could somebody help please??
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2020 01:13 AM
let me lab this up and i shall get back to you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2020 02:03 AM
Hi,
Sometimes the NAT configuration fails to be pushed correctly for the ASP path. Try the following, to avoid any suspect behaviours (do it for one NAT statement, the one for 192.168.111.250):
- give your objects names which are not IP addresses
-reload the ASA
-test again
If still not working, upgrade to a stable and recommended release, like 9.8.4
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2020 02:17 PM
Hi Cristian,
Thank you for your respond.
I did so already, but without reload ASA.
Now I've tried as you said (with reload):
nat (inside,bft) source static obj_111-244 interface destination static bft-network bft-network service tcp80 tcp45423 nat (inside,bft) source static obj_111-250 interface destination static bft-network bft-network service tcp3389 tcp65123 no-proxy-arp
both NATs above don't work. =(
Tried on 9.8(4)17 and 9.9(2)66 without success.
Awful glitch =(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2020 07:29 PM
Can you attach the actual config as a text file please with a quick drawing and I'll lab it to validate it?
Can you detail what source ip is natted to what? Just to make sure the config is matching what you're expecting.
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 11:55 AM
Hi,
Can you upload the latest config and the output of "packet-tracer" matching the traffic you want to work?
Regards,
Cristian Matei.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 12:24 PM
interesting i lab it up but it was only one nat rule. and its worked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 03:05 PM
I've just created my own LAB. I have spare ASA5506-x.
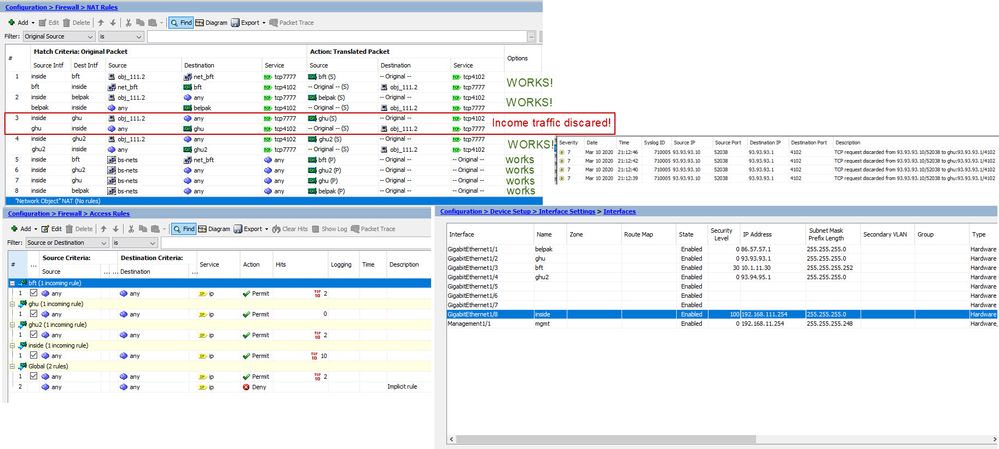
So, I reseted config, upgraded rommon to 1.1.15, asa to 9.9.2.66 and asdm 792.152. Removed BRI and then created step by step interfaces, NATs and ACLs. See attached config.
And I've met the same issue (one of my interfaces 'ghu' discarded traffic), but NAT rules and ACLs were absolutely the same! I created another interface 'ghu2' with different IP address - PAT works.
See screenshots:
So I made conclusion the problem not in NAT, but in interfaces. It's strange glitch.
I tried edit startup config and move 'ghu' to another interface and 'ghu2' to the place of 'ghu' and reboot, but it didn't help. GHU was discarding traffic.
Finally I removed 'ghu' interface and created it again with the same IP address, added NAT,ACLs and now Port-forwards working fine on all my interfaces on test asa.
Now I think how to do the same operation on my production ASA in order to avoid recreating of IPSecs, NATs, ACLs and routes...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 03:54 PM
Recreate interface fixed and all releated objects (IPSecs, NATs, ACLs, Routes and etc.) fixed my glitch.
Thank you very much to anyone who tried to help me!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 11:54 PM
Well done I can feel the joy and the happiness. Well played no doubt you are good trouble shooter
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-11-2020 02:12 AM
Hi,
Not sure about you, but i almost gave up. However, on the funny side, i remember running into this absolute crazy stuff on the ASA: it happen couple times that stuff stopped working, and after thorough investigations, i just defaulted the interfaces and recreated and boom, miracle. However, never found a bug on it, which make the whole thing even more akward.
Life of an engineer, chasing ghosts :)
Regards,
Cristian Matei.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide