- Cisco Community
- Technology and Support
- Security
- Network Security
- Ok...so what do you do if you
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2016 08:05 PM - edited 03-12-2019 06:04 AM
We have a FireSight system with one version 5.4.0.5 Virtual Data Center and several ASA devices. We installed some User Agents to get user logon/logoff information from MS AD servers, and encountered 2 problems:
1) All User Agent servers (window server 2008R2/64/SP1 and Windows server 2012R2) report error 2201. They can pull logon info from AD server correctly and export correct user map, can communicate with Virtual Data Center, but just cannot send data to it. Meanwhile, one User Agent on Windows 2008 STD/SP2 server works perfectly. Have tried 3 other servers, 2 User Agent versions, en-us regional settings, and 2 .Net versions. Nothing changed.
2) We prefer to have only 1 User Agent but 1 User Agent supports 5 DC servers at max. So we configured one central AD server to subcribe security logs from all AD servers successfully to its event log folder 'Forwarded Events', and configured the User Agent to pull data from this central AD server. The User Agent does pull logons, but only from events folder 'Windows Logs - Security', never from 'Forwarded Events'. Is the User Agent designed to read from 'Windows Logs-Security' only?
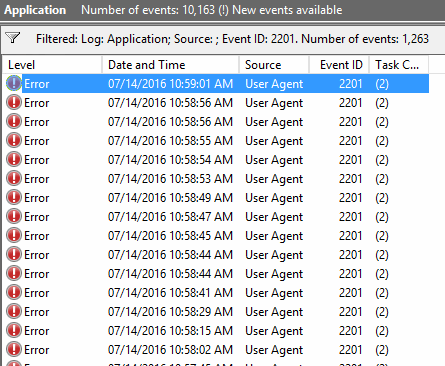
[2201] - Report login information from USER-AGENT-SERVER to 10.xx.xx.xx failed after 07/14/2016 9:08:55 AM. [A call to SSPI failed, see inner exception.].
Solved! Go to Solution.
- Labels:
-
NGIPS
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2016 08:22 PM
This is known issue.
Please uninstall the Microsoft update
KB3161606 and KB3161608
Upon closer inspection, the issue appears to be a specific change to the default Cipher Suites:
https://support.microsoft.com/en-us/kb/3161639
There is bug created for this.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCva32331
Rate if helps.
yogesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2016 08:22 PM
This is known issue.
Please uninstall the Microsoft update
KB3161606 and KB3161608
Upon closer inspection, the issue appears to be a specific change to the default Cipher Suites:
https://support.microsoft.com/en-us/kb/3161639
There is bug created for this.
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCva32331
Rate if helps.
yogesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2016 09:49 PM
Thanks yogdhanu for the right answer. I uninstalled KB3161606 and it works fine now.
Do you know whether the User Agent pulls logons from "Windows Logs - Forwarded Events"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2016 11:05 PM
Hi
User agent reads AD events 4624 logon events.
Rate if helps
Yogesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-14-2016 12:15 AM
Thanks but I meant something else:

My User Agent reads event type 4624 from "Security" (local DC server events) correctly, but seems it doesn't read event type 4624 from "Forwarded Events" (subscribed events from other DC servers). Is it designed to do so, or is there any wrong configuration with my event forwarding?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-01-2016 10:56 AM
From the alternate workaround wording in the bug info:
"Windows, for DH suites has a minimum key length set to 1024, which appears to lead to this issue. You can work around this by changing this to support 512-bit key length."
512-bit really? I assume an update is in the works for this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-03-2016 05:50 AM
Hello
Changing the windows register like it is described in bug workaround helped for me.
The host restart was not necessary.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2016 12:25 AM
Cisco fix this nasty bug in User Agent!!!! I got hit by the same bug!!! FirePOWER 6.0.1.1 & Windows Server 2012 R2!!! I had to uninstall whole patch roll-up to get User Agent working again. Registry hack didn't work for me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-28-2016 04:26 PM
I've just been hit by this bug as well... several hours later I find this thread.
I applied registry fix to Windows 2008 R2 hosting SFUA server & reboot for good measure. Updates to FMC restored.
When can we expect an update to User Agent? Reducing the cipher levels to 512 is not a fix!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2016 09:36 AM
Ok...so what do you do if you have this issue, and do NOT find either of these updates applied in my Windows Server 2012r2?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2016 09:57 AM
Then I would suggest that you go with the solution where you manually change the diffie hellman parameters in the windows registry.
I did that to 4 servers without problems today :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-10-2016 01:55 PM
Microsoft replaced the patches with new ones. Check and see if you have either 3172614 or 3172605.
KB3161606 - https://support.microsoft.com/en-us/kb/3172614
KB3161608 - https://support.microsoft.com/en-us/kb/3172605
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2016 01:47 AM
Okay i guess if you have 3172614 the registry hack doesn't work anymore. You NEED to uninstall 3172614 to get this working again with registry hack.
I mean c'mon Cisco how long do we have to wait to get this permanently fixed??!?!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-15-2016 11:13 AM
Uninstalling 3172614 worked for me. If anyone from Cisco is listening, you REALLY need to fix this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2016 09:15 AM
I did registry hack and it worked for a while, now it died again!!!! when do you plan to fix this?!?!?! i'm on FP 6.0.1.2.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


