- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Hairpin public outside traffic to server on vpn tunnel
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Hairpin public outside traffic to server on vpn tunnel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2018 09:47 PM - edited 02-21-2020 08:17 AM
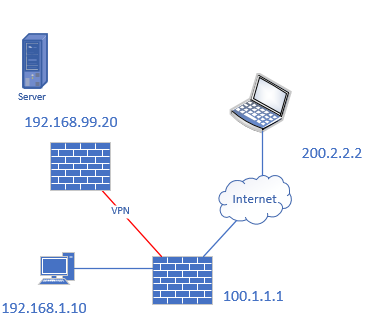
Need some assistance in how to configure ASA to allow hairpin of public Internet traffic across VPN tunnel.
I have a server with an IP of 192.168.99.20 that sits behind an ASA with a VPN tunnel to another ASA with an outside public IP of 100.1.1.1. I need to allow anyone coming in on the Intnernet to reach port 443 on the server via the public IP of 100.1.1.1
Currently, the only traffic mapped to the VPN tunnel between the ASA's is the 192.168.99.0 network and then 192.168.1.0 network.
How can I configure hairpin to allow public traffic on port 443 to reach this server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2018 12:56 AM
This is quite challenging, but there are multiple options to solve that. You have to choose between a more complex setup of your network or some extra work of preparation.
Four ways to solve that in my preferred order when I had a task like this to do:
- Move the server to the main site. Your Network doesn't need any more adjustments.
- Place a reverse-proxy into the DMZ of your HQ, terminate the connection there and the reverse-proxy sends the request to the branch office.
- If the Branch has the same security controls as firewalling/IPS/DMZ and so on as the main site, then use one of the public IPs on the branch.
- Solving that within your VPN is complex as the VPN has to protect "any <-> Branch-Server" on the branch VPN. To make that less complex I would first change the VPN from crypto-maps to tunnel-interfaces and use PBR on the branch to route the server-traffic into the tunnel. But I would consider this a dirty workaround with too much complexity.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide