- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: Miss configured ZBFW?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Miss configured ZBFW?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 01:11 PM - edited 02-28-2020 01:12 PM
Hi All,
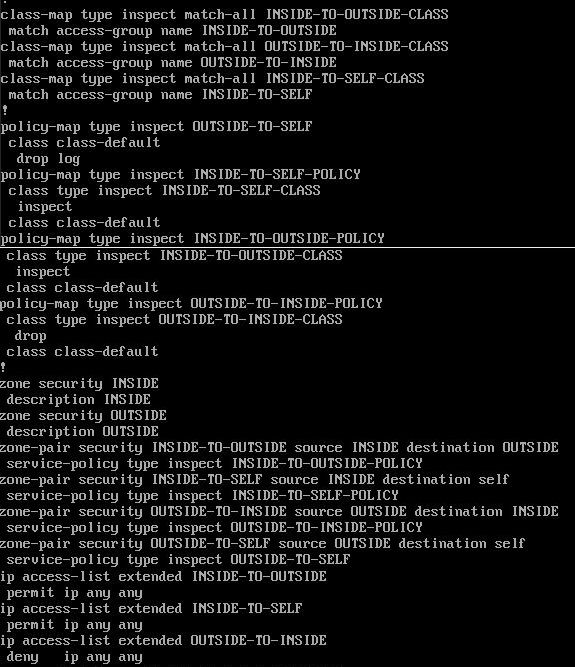
I have a problem with ZBFW (on router). I tried to set it up like (I think) should it be, so Inside can initiate connection to the outside and to router itself but outside cannot initiate connection to inside and to router it self. Based on below configuration can you tell me why it's not working like it should? (I skipped interface configuration in this output but they have properly assigned commands "zone-member security INSIDE" and "zone-member security OUTSIDE"):
- Labels:
-
Other Network Security Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 01:39 PM
What exactly is and is not working in this configuration?
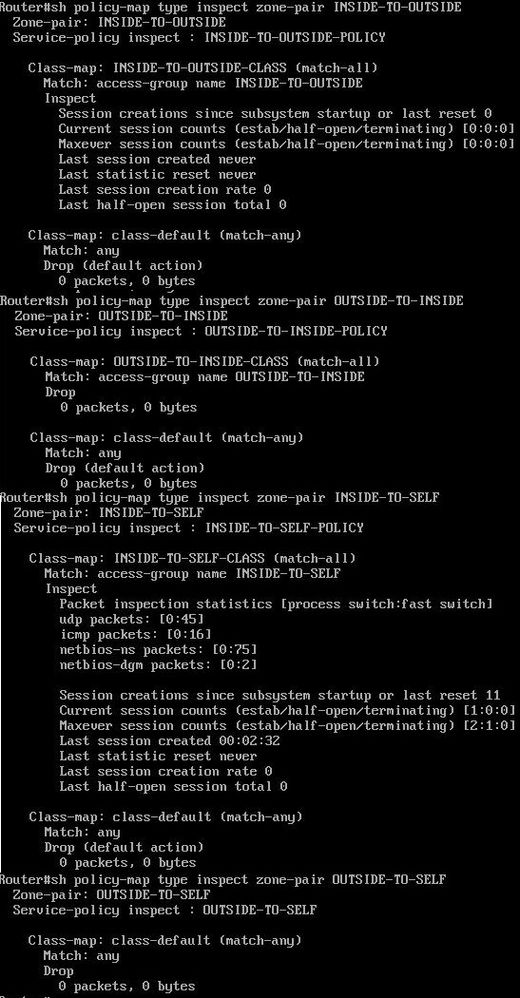
Provide the output of "show policy-map type inspect zone-pair <your zone pairs>"
You'd be better off providing the full configuration, as this might provide other clues as to where the issue lies.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 02:11 PM
What is not working:
I have config PC1->Router1 (PPOE client) -> Router2 (PPPOE server) -> PC2
PC1 can ping Router1 inside interface as well as Dialer interface but cannot ping Router2 so cannot initiate connection outside network. Meanwhile Router1 can ping Router2 loopback as well as internal router2 interface facing PC2. Both router have default gateways as each other.
Here is an output that you asked for and below that there is rest of the configuration that could do anything I skipped things like dhcp or hashes and etc:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 02:20 PM
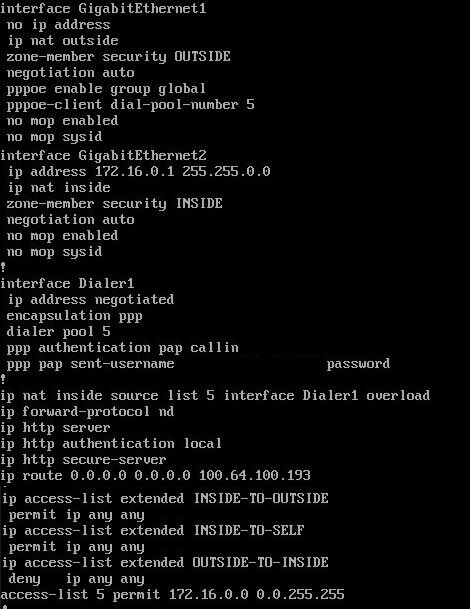
And you don't appear to have defined zone-member OUTSIDE on the dialer interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 02:45 PM - edited 02-28-2020 02:46 PM
Ok I'm dumb :D You are right Dialer should be outside zone for security as well as for NAT. I fixed that, now PC1 can ping router1 and Rotuer2 both external and internal interfaces BUT he cannot ping PC2. PC2 have firewall off and allow ICMPs.
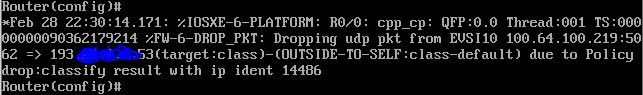
Also Im getting periodic message like this:
100.64.100.219 is the local router so he is the source however he dropping this packet (DNS server 193.X.X.X) based on rule outside-to-self even if this is self-to-outside(I don't have this configured maybe thats the problem?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2020 02:55 PM - edited 02-28-2020 03:11 PM
Good :)
Turn on debug on both routers R1 and R2 "debug ip icmp", then ping PC2, observe the output - I don't know the configuration of R2, but are you pinging the real IP address of PC2 but the return traffic is being natted? Turn on nat debug as well and provide the output of "show ip nat translation"
I imagine that DNS request is NOT related to this issue, but if you wish you could take a packet capture and observe the output to determine what hostname is attempting to be resolved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-29-2020 12:43 PM
To sort it out:
Right now I'm allowing traffic:
-inside to outside
-inside to self
-self to inside
Right now I'm denying traffic:
-outside to inside
-outside to self
-self to outside
Because I want to deny possibility that someone from outside can establish connection to my network I think current setup should work, BUT I have doubt. Router1 have NAT so if I'm not mistaken router sees that he is the source (self) of connection and he initiating connection to outsie. Am I right? If yes then should I create policy and class allowing selft-to-outside?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2020 10:00 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-29-2020 10:51 AM
Hi,
Do a continuous ping from PC1 towards both PC2 and router2, and look on router1 in the connection table (show policy-firewall session); if you see both sessions in there, based on the provided config, there is something wrong on PC2. To ensure that there is nothing wrong with your ZBFW, remove the "zone member security" commands, so like disable ZBFW, and see if you can ping from PC1 to PC2.
Also, you've probably wanted to do NAT, but forgot to enable "ip nat outside" on your Dialer interface.
Regards,
Cristian Matei.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide