- Cisco Community
- Technology and Support
- Security
- Network Security
- i want it to be placed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Needs basic help with asa5505
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2017 04:03 AM - edited 03-12-2019 01:48 AM
Hello!
I just started my new job at a company ( finally made it to change my line of work it IT )!
Here's the problem, They have already setup a working network before me and my boss wants to keep that network working but i need to set up a basic switch to asa5505 to connect a ( atm only one but will be more hence the switch ) ftp server to it and grant it access to internet but im new to this kind of gear *still learning*.
SO i was hoping someone has a bit of free time over and can guide me to open that switch to the internet but still closed off to the rest of the network without f'ing up the old config.
Yeah and btw, would be easiest / best if i could do it from COM port because thats how it's connected atm
Sincerely New guy!
- Labels:
-
NGFW Firewalls
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2017 01:54 PM
Do the FTP servers need to be accessed from the internet or do they just need access to the internet? Also, what license is your ASA running (Base license or security plus license). Issue the show version command to get this info.
is it a layer 3 switch or layer 2. and how many subnets do you have in your network. Do they just need to be seperated from the FTP servers or also from eachother?
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2017 04:12 AM
the ftp servers is going to be used as online storage for all employees so i guess only accessed from the internet.
Base License
Is there a command i issue to get you all the info you need?
Sincerely
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2017 04:52 AM
Are you going to place the server in a DMZ so you can filter traffic for internal users also or will it be placed on the inside network?
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-23-2017 06:37 AM
i want it to be placed outside all networks for security reasons and there is no reason to have it internal since the company server computer will have another network cable going to the internal network on differnet subnet, But ill try to not make a fool of myself by making this:
Server 1 will be for employees only
Server 2,3 will be for renting out etc.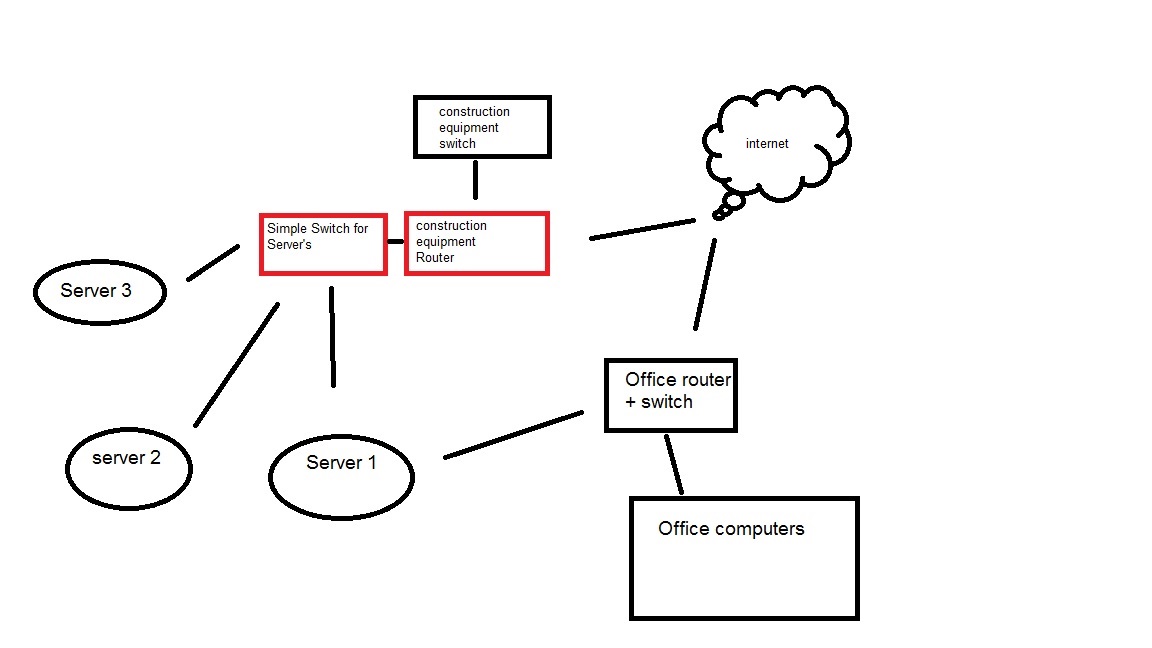
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2017 12:20 PM
Where is the ASA coming into play in your network diagram here? I am assuming the red boxes?
If the ASA is just going to sit between the internet and the servers and not route or touch any traffic from the office computers then you could do a simple configuration like the following just remember to change the interfaces, IPs passwords, host names, etc. as needed. Also, be sure to use passive FTP, not active.
hostname ciscoasa
domain-name home.local
enable password PASSWORD
!
interface Ethernet1/1
description Internet
nameif outside
security-level 0
ip address dhcp setroute
!
interface Ethernet1/2
description Office Computers
nameif Inside
security-level 100
ip address 10.1.2.1 255.255.255.0
object network OFFICE_SERVER1_Private
host 10.1.2.10
object network OFFICE_SERVER2_Private
host 10.1.2.11
object network OFFICE_SERVER1_Public
host 11.11.11.10
object network OFFICE_SERVER2_Public
host 11.11.11.11
object network OFFICE_COMPUTERS
subnet 10.1.2.0 255.255.255.0
object network OFFICE_COMPUTERS
nat (inside,outside) dynamic interface
nat (inside,outside) source static OFFICE_SERVER1 OFFICE_SERVER1_Public
nat (inside,outside) source static OFFICE_SERVER2 OFFICE_SERVER2_Public
access-list outside_access_in permit tcp any host 10.1.2.10 eq 21
access-list outside_access_in permit tcp any host 10.1.2.11 eq 21
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 11.11.11.1
username NAME password PASSWORD
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
aaa authentication serial console LOCAL
ssh 10.1.2.0 255.255.255.0 inside
http server enables
http10.1.2.0 255.255.255.0 inside
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2017 05:23 AM
i think you missunderstood, i just want to configure a port on the asa 5505 router that i can plug into a switch and have all the ftp servers on. and its atm configured alrdy so i just want to "add" to the config to a physical port on the router, can i write something in the terminal and copy here that shows how's it configured?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-27-2017 06:30 AM
Ok, Then the interface configuration you want would be something like this just replace the vlan in the no forward command to your inside network, and change the interface vlan do the desired VLAN number. NAT and ACL configuration will differ depending on if you are running ASA version 8.2 or earlier or 8.3 and higher. Here is an example of what you could do to grant access to FTP servers from the internet.
interface vlan3
no forward interface vlan 1
description SERVERS
nameif DMZ
security-level 50
ip address 10.1.2.1 255.255.255.0
no shut
object network SERVERS_privarte
host 10.1.2.10
nat (inside,outside) static interface service tcp ftp ftp
access-list outside_access_in permit tcp any host 10.1.2.10 eq ftp
access-group outside_access_in in interface outside
--
Please remember to select a correct answer and rate helpful posts
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2017 05:26 AM
Cisco Adaptive Security Appliance Software Version 8.4(2)
VLAN Name Status Ports
---- -------------------------------- --------- -----------------------------
1 inside up Et0/1, Et0/2, Et0/3, Et0/4
Et0/5, Et0/6, Et0/7
2 outside up Et0/0
any other command i should type and post ? since im worried im gonna break something in the existing config for the equipment already connected to it *im not allowed to change so that dosnt work*
a thousand thanks so far mate, you are gold!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2017 05:33 AM
I am getting emails that there have been updates to the discussion but when I come to the discussion page I do not see any updates. I have sent a mail to support and asked them to check this.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2017 05:07 AM
Did you delete your reply ? :(
EDIT: nvm.. the forum bugged out
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-29-2017 05:05 AM
Cant help :/ ?
Sincerely
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


