- Cisco Community
- Technology and Support
- Security
- Network Security
- OSPF Setup on L3 switches and firewall?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2023 11:57 PM
Hello, So i'm doing an assignment and i'm interested in doing a routing setup with OSPF on my Layer 3 switches.
I would want to have my layer 3 switches route all the traffic that's supposed to go outside to the closest firewall interface.
However i am not entirely certain on how i should start this setup.
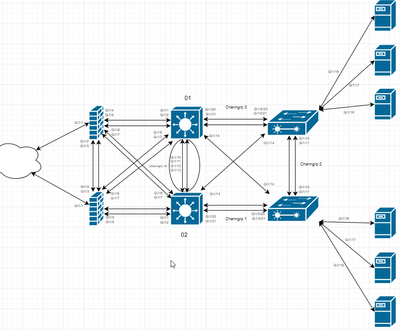
my topology is the following
any help and feedback is very appriciated. if anything further is needed i will add that if requested
Also is it nessecary to setup OSPF on the firewalls too
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:47 AM - edited 10-04-2023 03:50 AM
@thom784e You need a default route to the ASA from the L3 switch and the ASA will need to know the internal routes (via OSPF or statics). The ASA will need NAT rules for VLAN 2 and the rest to communicate with the internet. The switch will need to be configured for IP routing to perform intervlan routing.
If you can now ping between the ASA and the switch you should now also be able to setup OSPF between those devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 04:03 AM
So the following is what you need on the ASA to get things working, you already have some of this in place.
- an IP address, interface name, security level on an interface for interface connected to ISP (set security level to 0)
- an IP address, interface name, security level on an interface for interface connected to LAN (set security level to 100)
- default route towards your ISP
- static route or Dynamic routing towards your internal LAN so that non-directly connected subnets are reachable. You might also want to consider publishing the default route if using dynamic routing.
- dynamic NAT to translate private internal IPs to you outside interface I
On the L3 switch you already have most of what you need configured also.
- uplink port towards the ASA configured as an access port in VLAN 10
- dynamic or static route depending on what you prefer to send internet traffic to the ASA.
- VLAN interfaces configured with relevant IP addresses and, in your case, also HSRP IPs
This is the bare minimum you need to get traffic flowing to the internet.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 12:15 AM
You can not have the traffic to go nearest FW , rather you can use Active /Standby - So the decision made easy to active unit only.
the OSPF only peer with active, standby way for active to fail over.
or is this ASA working standalone then you can make decision to based on the traffic or cost.
(not reviewed your files, just my views)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 12:43 AM
we were told elsewhere that we should setup the firewalls as failover with one primary and one secondary, this means we just config 1 firewall and if that goes down the other one takes over, (maybe this is the active/standby you mentioned)
we want to route ospf to belive that the lowest cost is the one that goes towards FW01 by default, and then if FW01 is inactive or down, it will then go to FW02 that by that point should have taken over as the active one
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 01:04 AM
@thom784e active/standby is failover. Only one unit is active and passing traffic (you don't need a cost in this scenario, there would only be one default route via the active firewall), the active unit will have an OSPF adjacency to the local switch. If the active unit fails, the standby unit will become active with all traffic now routed through that unit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 01:34 AM
in this case, how should we do it with our public IP's
if we have 2, and we set one static on FW-01
when FW-01 does fail during stuff such as an accept test, how do we ensure that FW-02 uses the other public IP (such as if the fw-01 pub ip is the point of failure)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 01:48 AM
@thom784e when you configure ASA failover you define the primary/active IP address and a standby IP address on all interfaces.
Example:-
interface GigabitEthernet0/0
nameif INSIDE
security-level 100
ip address 192.168.250.1 255.255.255.0 standby 192.168.250.2
!
interface GigabitEthernet0/1
nameif OUTSIDE
security-level 0
ip address 1.1.1.1 255.255.255.0 standby 1.1.1.2
You then define one ASA as primary and the other as secondary. The primary unit will process all traffic and have the active/primary IP address and the secondary unit will have the standby IP address.
When the primary ASA fails over to the secondary (standby) unit, this unit takes over the primary IP address and re-uses it. So the active IP address (outside, inside etc) will always be the same regardless of what unit is active.
Example to configure ASA failover:- https://integratingit.wordpress.com/2016/08/12/configuring-cisco-asa-activestandby-failover/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 01:47 AM
What is the purpose of the firewalls? Do you want to filter traffic between the VLANs or just towards the internet?
Without any explanation of what your objective is it will be difficult to come with suggestions. For example, if server / PC group 1 has one subnet and server / PC group 2 has another, you could setup the ASAs in an Active/Active failover setup. This will allow you to send traffic to the closest firewall, but then failover if that ASA fails.
You could also have 2 standalone ASAs and then manipulate traffic using OSPF cost.
If you want to separate the subnets you have configured, you will either need to remove the IPs on the L3 devices and move them to the ASA, or configure VRFs on the L3 devices.
As you can see, there are many possible solutions but it all depends on your requirements. As mentioned by others, Active / Standby is a very common setup and easy to do, but then you will not be sending traffic to the closest ASA.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:01 AM
right now we are trying to get our L3-01 and L3-02 to route all internet traffic to FW-01, and if FW-01 isn't available we want to send it to FW-02.
most VLAN stuff is being done on the L3 switch and the firewalls currently only act as a layer between the L3 and the internet and for the firewall to block the default stuff, so basically just send our internet traffic from the server and pc's to the firewall and then have the firewall send it through.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:09 AM
@thom784e then ASA active/standby failover will achieve this. https://www.cisco.com/c/en/us/td/docs/security/asa/asa919/configuration/general/asa-919-general-config/ha-failover.html#ID-2107-00000429
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:13 AM
alright thank you, i will look into this.
now it's just about how i can tell the L3 switches to route all traffic to the firewall.
for some reason it doesn't want to accept a normal
ip route 0.0.0.0 0.0.0.0 192.168.10.10 (ip on FW-01 interface facing towards L3-01)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:26 AM
@thom784e You will need to provide more information on the problem. What error do you get on the L3 switch? Can you ping the ASA from the switch?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:38 AM - edited 10-04-2023 02:38 AM
no, there appears to be some issues between the asa and the L3.
the ASA can ping 8.8.8.8
but the IP we set on the ASA interface that faces the L3 does not respond when pinging 192.168.10.10 from the L3
if you need more details please tell the details needed and i'll do my best to provide them asap
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:49 AM
@thom784e well it looks like you are trunking multiple VLANs on the L3 switch to the ASA, but you've not defined the VLANs on the ASA. If you don't need to trunk multiple VLANs to the ASA, change it to an access port in VLAN 10. https://www.cisco.com/c/en/us/td/docs/security/asa/asa919/configuration/general/asa-919-general-config/interface-vlan.html
Also your interfaces on the ASA don't appear to be accurate in relation to the diagram and you'd need to connect the ASA's to VSS/VPC/VSW switches, so the two switches act as a single switch, rather than two independant switches https://www.cisco.com/c/en/us/td/docs/security/asa/asa919/configuration/general/asa-919-general-config/interface-echannel.html
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 02:53 AM
yes we have had some issues with the etherchannels, they caused some MAC flapping so we have decided to just directly plug them in to try and get internet access so we can start doing our ESXI and then re-visit the etherchannels at a later point.
currently the L3 G0/1 is directly connected to the ASA G0/4 (or G1/4).
wouldn't setting the asa as an access port on vlan 10 make our vlan 2,3,4 have issues when trying to travel through the firewall?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:00 AM
@thom784e not if the L3 switch is doing the routing, then you just need a route to the ASA from the L3 switch.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide