- Cisco Community
- Technology and Support
- Security
- Network Security
- Re: OSPF Setup on L3 switches and firewall?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-03-2023 11:57 PM
Hello, So i'm doing an assignment and i'm interested in doing a routing setup with OSPF on my Layer 3 switches.
I would want to have my layer 3 switches route all the traffic that's supposed to go outside to the closest firewall interface.
However i am not entirely certain on how i should start this setup.
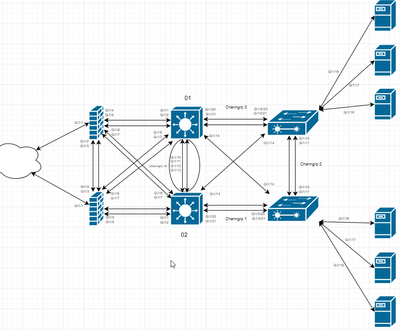
my topology is the following
any help and feedback is very appriciated. if anything further is needed i will add that if requested
Also is it nessecary to setup OSPF on the firewalls too
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:11 AM
could you potentially help point me in the right direction as to how i'm supposed to do that.
currently we have this
ip route 0.0.0.0 0.0.0.0 192.168.10.10, the 192.168.10.10 is the ip on the interface facing the asa.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:23 AM - edited 10-04-2023 03:28 AM
@thom784e change the switch interface that connects to the ASA to an access port. You should then be able to ping between the ASA and the switch.
interface GigabitEthernetX/X
switchport mode access
switchport access vlan 10
I see no NAT configuration on your ASA, you will need to configure this if you want the VLANs to communicate to the internet. There seems to be a considerable amount of configuration this is required to get an overall working solution (as per the topology diagram).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:39 AM - edited 10-04-2023 03:42 AM
yes i am sadly aware of the amount of work that needs to be done.
if i change the port to access and tell it to access vlan 10 i am able to ping between them. but wouldn't that create issues if the vlan2 gateway of 192.168.2.1 tries to send data out FW-01?
i tried editing the port to be a trunk in a couple of different ways since that would allow all vlans over it, but maybe that is barking up the wrong tree and mostly the nat that needs missing for internet access to go out.
Or did you spot any errors in the L3 switches config aswell?
Appriciate the help you've been giving.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:46 AM
This really boils down to where you want to do the inter VLAN routing (on the ASA or on the switches). If you are only doing interVLAN routing on the switches then all you need is a default route pointing to the ASA IP. And as Rob has mentioned the switch interface needs to be an access port and NOT a trunk port. When routing on the switch if you are sending traffic from VLAN 2 to the internet, then the switch routes traffic from VLAN2 to VLAN1 and then forwards the traffic using the default gateway. So you you will not have any issues with routing so long as you have the VLAN interfaces configured correctly.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:59 AM
so if i want to have the L3 do the intervlan routing i need to do the following on the ASA
Setup NAT for Client vlan 2 Management Vlan 3 and for Server Vlan 4
On the switch
Set the interface facing the Firewall to access mode on vlan 10.
ip route 0.0.0.0 0.0.0.0 192.168.10.11 (ip on FW-01 facing L3)
and then what do i do to ensure that the switches properly route vlan 2 traffic to vlan 10 so that it can travel from L3 to FW-01 (is that the OSPF setup that i have that will be doing that for me?)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 03:47 AM - edited 10-04-2023 03:50 AM
@thom784e You need a default route to the ASA from the L3 switch and the ASA will need to know the internal routes (via OSPF or statics). The ASA will need NAT rules for VLAN 2 and the rest to communicate with the internet. The switch will need to be configured for IP routing to perform intervlan routing.
If you can now ping between the ASA and the switch you should now also be able to setup OSPF between those devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 04:03 AM
So the following is what you need on the ASA to get things working, you already have some of this in place.
- an IP address, interface name, security level on an interface for interface connected to ISP (set security level to 0)
- an IP address, interface name, security level on an interface for interface connected to LAN (set security level to 100)
- default route towards your ISP
- static route or Dynamic routing towards your internal LAN so that non-directly connected subnets are reachable. You might also want to consider publishing the default route if using dynamic routing.
- dynamic NAT to translate private internal IPs to you outside interface I
On the L3 switch you already have most of what you need configured also.
- uplink port towards the ASA configured as an access port in VLAN 10
- dynamic or static route depending on what you prefer to send internet traffic to the ASA.
- VLAN interfaces configured with relevant IP addresses and, in your case, also HSRP IPs
This is the bare minimum you need to get traffic flowing to the internet.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 04:18 AM
when you say default route towards your isp,
we have 2 available public IP's for this project do i just choose one of those and make the default route towards that.
and am i supposed to set said public ip on our Firewall interface 1/1 that goes from the FW to the ISP, or am i supposed to set another ip on the firewall interface 1/1 (such as 192.168.10.100) and then route stuff to that, and once it reaches that it will go to the public ip?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 04:38 AM
Ok...a short intro to routing. Network devices can only communicate with directly connected devices that are within the same subnet. so for example, if you connect a switch to the ASA and set its interface to 192.168.1.2/24 and then configure the ASA interface to be 192.168.1.1/24 they will be able to communicate with each other. However, if the ASA interface was set to be 192.168.2.1/24, then communication will fail between the devices.
The IP you configure on your ASA and the IP you configure for your default route depends on what you receive from your ISP to configure. They will either give you a public IP that you configure on your device, and they will also provide their IP which will be the default gateway address. Alternatively they might provide the IP dynamically in which case you would need to configure your device to accommodate that. Now given that you have two public IPs, then I would assume that one of them is the IP that you should configure on your ASA while the other is the ISP side. If you do not know which is which, you need to contact your ISP and have them clarify which IP you configure on your ASA and which is to be used as the next hop for the default route.
Please remember to select a correct answer and rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2023 04:03 AM
like this?
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide