- Cisco Community
- Technology and Support
- Security
- Network Security
- Two ISP connection in my ASA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 07:44 PM
Hi there,
I have 1 ASA 5510 version 8.3 with 4 interfaces. outside1, outside2, inside and DMZ. Both outside1 and outside2 interfaces connected to ISP1 and ISP2 respectively. And core switch connecting my ASA with all my internal users. My current provider is ISP1 and all working well serving 300 users to the internet. Nevertheles, there were new requirement from our decision maker to port in a new ISP provider ISP2 into our network. ISP2 comes with all their own routers. ISP2 purposes is only to serves a few subnets or application for our internal users from their cloud.
In ASA my default route to the internet is to ISP1 routers interface
route outside1 0.0.0.0 0.0.0.0 1.1.1.1 1
My questions is can I route my all my internal users to certain subnets/ip address to ISP2 clouds without interrupting my default route to the internet?
For example I want to route my users to ISP2 for subnets 10.40.88.0/24 or ip addres 10.40.88.35/32
I have already route the subnets in cores switch and route in ASA but have no luck.
route outside2 10.40.88.0 255.255.255.0 2.2.2.2 1
Really appreciate any comments or advises.
Solved! Go to Solution.
- Labels:
-
Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2019 05:22 AM - edited 04-06-2019 01:44 AM
Hi,
Sorry, my option was wrong as PBR on ASA 8.3.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2020 11:54 PM
HI @El Rondo
If you intend to use the new ISP connection for only certain (users, vlans or subnets), then you'd normally use PBR...but your ASA 5510 does not support upgrading to 9.x which supports PBR. You'd have to replace your hardware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2019 09:00 PM
Hi
What you want to achieve is called PBR and this is supported on version 9.4.x. However this version isn't supported on your asa 5510.
You can try a workaround to this by playing with nat. Commands would look like:
sysopt noproxyarp inside
!
object network HOST-ISP2
host 10.40.88.35
!
object network ANY-ISP2
subnet 0.0.0.0 0.0.0.0
!
nat (inside,outside-isp2) source dynamic HOST-ISP2 interface destination static ANY-ISP2 any
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2019 05:22 AM - edited 04-06-2019 01:44 AM
Hi,
Sorry, my option was wrong as PBR on ASA 8.3.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2019 10:47 PM
Thanks
Francesco
PS: Please don't forget to rate and select as validated answer if this answered your question
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2020 08:00 PM
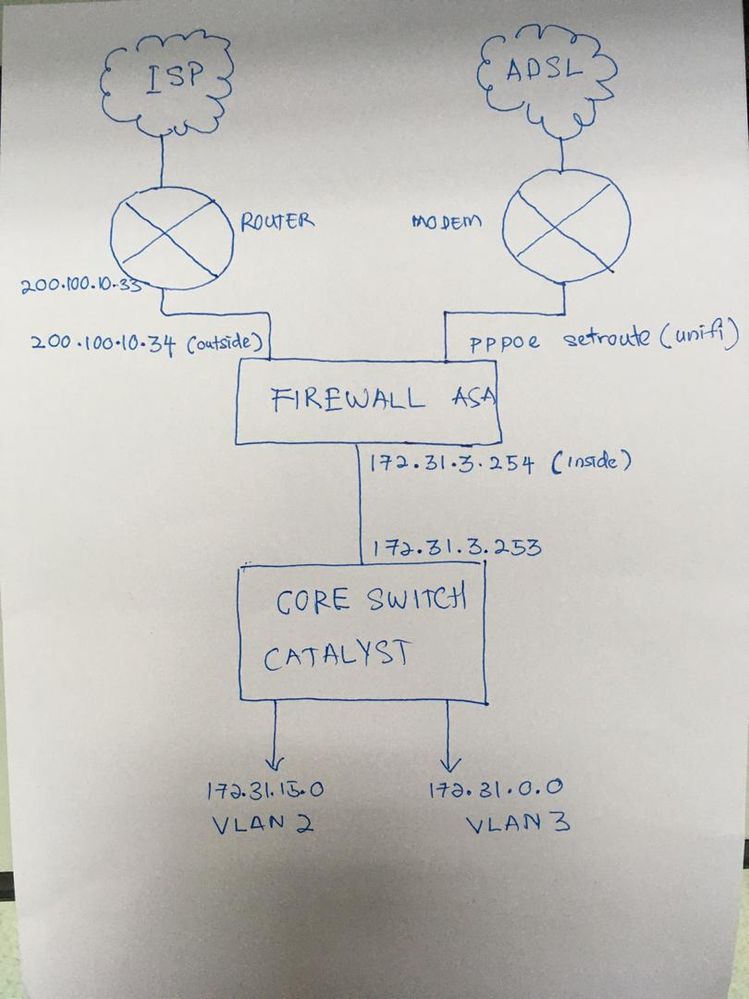
Sorry to raise up this thread again. Regarding to my last year problem was still unresolved due to multiple ISP implementation was postponed for a certain reason. However it has been continued started this year. I would explain briefly about my problem statement.
My company has 1 unit of ASA 5510 ver 7.2. This ASA has been running fine with one existing ISP (fix IP) being connected for all users. We have 1 unit of core switch Cisco Catalyst connected to ASA to work for the routing. Recently my company subscribe new ASDL line and want to port into existing network and intend to provide for only certain (users, vlans or subnets). This ASDL line comes with modem and PPPOE authentication username and password. I have already configured the ASA to meet the requirement and perhaps multiple ISP can be used together but I it seems got a little bit issue where targeted subnets was unable to route to the ASDL line. I attached here with the summary diagram of my current setup and sanitized configuration of ASA. Really appreciate any comments on this. I have been looking forward to solve the issue for almost 3 weeks.
ASA Version 7.2(3)
name 172.31.0.0 All_Subnet
name 172.31.15.0 ADSL_Subnet
interface Ethernet0/0
description *Metro-E*
nameif Outside
security-level 0
ip address 200.100.10.34 255.255.255.224
ospf cost 10
interface Ethernet0/1
description *LAN Gateway*
nameif Inside
security-level 100
ip address 172.31.3.254 255.255.255.248
ospf cost 10
interface Ethernet0/2
description DMZ interface
nameif DMZ
security-level 50
ip address 172.31.2.1 255.255.255.224
ospf cost 10
interface Ethernet0/3
description *Unifi Gateway*
nameif Unifi
security-level 0
pppoe client vpdn group UNIFI
ip address pppoe setroute
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
ospf cost 10
management-only
access-list outside_access_in_unifi extended permit icmp any any echo-reply
access-list outside_access_in_unifi extended permit icmp any any echo
mtu Outside 1500
mtu Inside 1500
mtu DMZ 1500
mtu management 1500
mtu Unifi 1492
global (Outside) 1 200.100.10.35-200.100.10.45 netmask 255.255.255.0
global (Inside) 1 200.100.10.42 netmask 255.255.255.0
global (Unifi) 2 interface
nat (Outside) 1 172.31.3.0 255.255.255.240 outside
nat (Inside) 2 ADSL_Subnet 255.255.255.0
nat (Inside) 1 All_Subnet 255.255.0.0 dns
static (Inside,Outside) 200.100.10.61 172.31.3.2 netmask 255.255.255.255 dns
access-group outside_access_in in interface Outside
access-group Inside_access_in in interface Inside
access-group Inside_access_out out interface Inside
access-group DMZ_to_inside in interface DMZ
access-group outside_access_in_unifi in interface Unifi
route Outside 0.0.0.0 0.0.0.0 200.100.10.33 1
route Inside All_Subnet 255.255.0.0 172.31.3.253 1
vpdn group UNIFI request dialout pppoe
vpdn group UNIFI localname abcd@unifi
vpdn group UNIFI ppp authentication pap
vpdn username abcd@unifi password *********
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect icmp
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-26-2020 11:54 PM
HI @El Rondo
If you intend to use the new ISP connection for only certain (users, vlans or subnets), then you'd normally use PBR...but your ASA 5510 does not support upgrading to 9.x which supports PBR. You'd have to replace your hardware.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2021 07:05 AM
Welcome back everyone. Finally I was successfully able to buy a new unit ASA 5525-X with version 9.8(2).
My intention is to provide dual internet (ISP) for our VLAN users. First ISP is connected to lease line with static public ip and second ISP is connected dialup with dynamic PPPoE.
I had run 3 tests here to simulate the result.
1) First run to show that ISP1 (lease line) connection is working for both vlan IT and WIFI.
interface GigabitEthernet0/0 nameif WAN security-level 0 ip address 10.33.22.11 255.255.255.224 ! interface GigabitEthernet0/1 nameif LAN security-level 100 ip address 172.16.4.253 255.255.254.0 ! object network IT subnet 172.17.4.0 255.255.255.0 description IT Vlan object network WIFI subnet 172.17.7.0 255.255.255.0 description WIFI Vlan mtu WAN 1500 mtu LAN 1500 object network IT nat (LAN,WAN) dynamic 10.33.22.12 object network WIFI nat (LAN,WAN) dynamic 10.33.22.13 route WAN 0.0.0.0 0.0.0.0 10.33.22.11 1
2) Second run to demonstrate that ISP2 (PPPoE) is working for both vlan IT and WIFI
interface GigabitEthernet0/0 nameif WAN security-level 0 ip address 10.33.22.11 255.255.255.224 ! interface GigabitEthernet0/1 nameif LAN security-level 100 ip address 172.16.4.253 255.255.254.0 ! interface GigabitEthernet0/3 no nameif no security-level no ip address ! interface GigabitEthernet0/3.1 description # connected to unifi modem fiberhome vlan 500 nameif UNIFI security-level 0 pppoe client vpdn group GROUP_UNIFI ip address pppoe setroute ! object network IT subnet 172.17.4.0 255.255.255.0 description IT Vlan ! object network WIFI subnet 172.17.7.0 255.255.255.0 description WIFI Vlan ! mtu WAN 1500 mtu LAN 1500 mtu UNIFI 1492 ! object network IT
nat (LAN,UNIFI) dynamic interface
object network WIFI nat (LAN,UNIFI) dynamic interface
! vpdn group GROUP_UNIFI request dialout pppoe vpdn group GROUP_UNIFI localname abcd@unifibiz vpdn group GROUP_UNIFI ppp authentication pap vpdn username abcd@unifibiz password *****
3) On the third run I try to route both vlans to different ISPs. vlan IT to ISP1 (lease line) and vlan WIFI to ISP2 (pppoe). The result is vlan IT was routed to ISP1 and vlan WIFI will also routed to ISP1.
interface GigabitEthernet0/0 nameif WAN security-level 0 ip address 10.33.22.11 255.255.255.224 ! interface GigabitEthernet0/1 nameif LAN security-level 100 ip address 172.16.4.253 255.255.254.0 ! interface GigabitEthernet0/3 no nameif no security-level no ip address ! interface GigabitEthernet0/3.1 description # connected to unifi modem fiberhome vlan 500 nameif UNIFI security-level 0 pppoe client vpdn group GROUP_UNIFI ip address pppoe setroute ! object network IT subnet 172.17.4.0 255.255.255.0 description IT Vlan ! object network WIFI subnet 172.17.7.0 255.255.255.0 description WIFI Vlan ! mtu WAN 1500 mtu LAN 1500 mtu UNIFI 1492 ! object network WIFI nat (LAN,UNIFI) dynamic interface ! object network LEVEL_4 nat (LAN,WAN) dynamic 10.33.22.12 ! route WAN 0.0.0.0 0.0.0.0 10.33.22.10 1 ! vpdn group GROUP_UNIFI request dialout pppoe vpdn group GROUP_UNIFI localname abcd@unifibiz vpdn group GROUP_UNIFI ppp authentication pap vpdn username abcd@unifibiz password *****
I really appreciate how can I achieve to route multiple vlans to dual isp like the above case. I understand that normally PBR can be used to. From what i understand that pbr will route if there is a static ip for example (pppoe fix ip). But my case was quite different where pppoe dont have static ip, it only receive dynamic ip.
Feel free to throw any comment here, I will likely to try any solutions and give feedback.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-28-2020 12:41 AM
Thanks Rob for the clarification. Its sound like I might propose upgrading ASA to the latest model to support PBR. I thought PBR only support on layer 3 switching but to meet company requirement I really need to think about it. Thank you
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide