Organizations are distributing IT infrastructure, applications, and data between on-premises, Data centers and Cloud-based environments. Applications and workloads can now reside on Private, Public or Hybrid clouds. By moving to the cloud, organizations can take advantage of cloud-based services, such as compute, storage, and networking, that can be scaled up or down as needed, rather than investing in expensive hardware that may not be fully utilized. The benefits include increased flexibility, scalability, and cost savings. At the same time, this poses a challenge to businesses to ensure that their sensitive data and resources are protected irrespective of where they are located (i.e. private, public or Hybrid cloud). In addition to securing the end points in the network, the data that is being transported over these private, public or Hybrid clouds need to be protected as well.
Cisco Catalyst 9000 switches are a family of high-performance, feature rich and highly secure switches designed for enterprise networks. Catalyst 9300X (members of Catalyst 9300 Series) and Catalyst 9400X (members of Catalyst 9400 Series) with UADP 2.0sec and UADP 3.0sec ASIC (Application-specific integrated circuit) respectively can now provide Layer 3 encryption up to 100G to secure the transport and provide cost effective solutions. 9300X and 9400X are equipped with a built in Crypto Engine to deliver this high speed, low latency Layer 3 encryption without compromising on any other features or scale.
With the introduction of IPsec, new use-cases can be achieved leveraging Catalyst 9000 switches. IPsec (Internet Protocol Security) is a protocol suite used to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. IPsec implementation on Catalyst 9000 switches based on IKEv2 standards. Below, we will discuss some of the use cases that can be achieved with the introduction of this new capability on the Catalyst 9000 switches.
Secure Site-to-Site Connections
IPsec encryption/decryption on the Catalyst 9300X & 9400X is performed in the hardware (ASIC) to provide up to 100Gbps of throughput. This provides the capability of provisioning high speed secure tunnels (site-to-site) between multiple locations [ Remote branch to Campus, Campus to Campus) either via a public or private transport without compromising on latency or other features. The implementation of IPsec in hardware renders a highly scalable and secure solution, accommodating the evolving needs of expanding networks. Customers now have the capability of provisioning either Static Virtual Tunnel Interfaces (SVTI) or GRE over IPSec tunnels based on the requirements. IGP (Interior Gateway Protocol [EIGRP/OSPF]) or BGP (Border Gateway Protocol) along with Multicast can be enabled over the IPsec tunnels to provide flexible Unicast and Multicast routing options. This unique capability of low latency, high speed Layer 3 encryption with key software features makes these platforms suitable for secure site-to-site deployments.

Catalyst 9000: Site-to-Site Deployment
Secure Site-to-Colo Connections
Combining COLO (Co-location) facilities and IPsec provides a secure and reliable solution for organizations that need to securely connect their remote locations to their large Campuses, Data Centers, or IT infrastructure. By leveraging Catalyst 9000 switches and IPsec functionality, organizations can establish a secure encrypted tunnel between their remote locations or data center and their servers hosted in the COLO facility. This ensures that data transmitted between the two locations is protected from interception or tampering by unauthorized parties.

Catalyst 9000: Site-to-Colo Deployment
Secure Internet Traffic
With applications residing everywhere (on-prem or cloud), redirecting Internet traffic locally rather than backhauling to a central location for inspection would be ideal. In these scenarios, IPsec can be terminated from Catalyst 9000 switches (9300X/9400X) to Cisco Umbrella or Zscaler or any 3rd party IKev2 complaint provide for inspection. These providers typically include features such as firewall, web filtering, intrusion prevention, and data loss prevention. This model allows customers to transition to pay-as-you-grow model, where they can provision new tunnels seamlessly as and when needed to provide secure internet access to users locally and protect the organization's network from internet-based threats. With 9300X/9400X traffic can be redirected at a selectively at a per-subnet level or can be load shared across multiple tunnels.

Catalyst 9000: Securing Internet Traffic
Secure Access to IaaS
Workloads are also hybrid which means the users need seamless access to these workloads irrespective of their location. To access the workloads hosted on a cloud provider securely, IPsec can be leveraged from the site to access these resources directly without backhauling to a central location. IPsec tunnels can be provisioned on Catalyst 9000 switches (9300X & 9400X) to any of these providers to ensure secure connectivity to these workloads. IPsec tunnels can be terminated natively on these cloud providers or can be terminated on the cloud Gateway offerings which is specific to the provider. Traffic can be redirected to these tunnels via static routing or Border Gateway Protocol (BGP) which provides additional knobs to control inbound and outbound traffic.

Catalyst 9000: Secure Access to Infrastructure as a Service
Secure Fabric
For use cases, where there is a requirement to build multiple Layer 3 overlays at scale, Catalyst 9000 switches (9300X & 9400X) offer unique capability of provisioning BGP EVPN Overlays on top of IPsec tunnels to create a Secure Fabric.
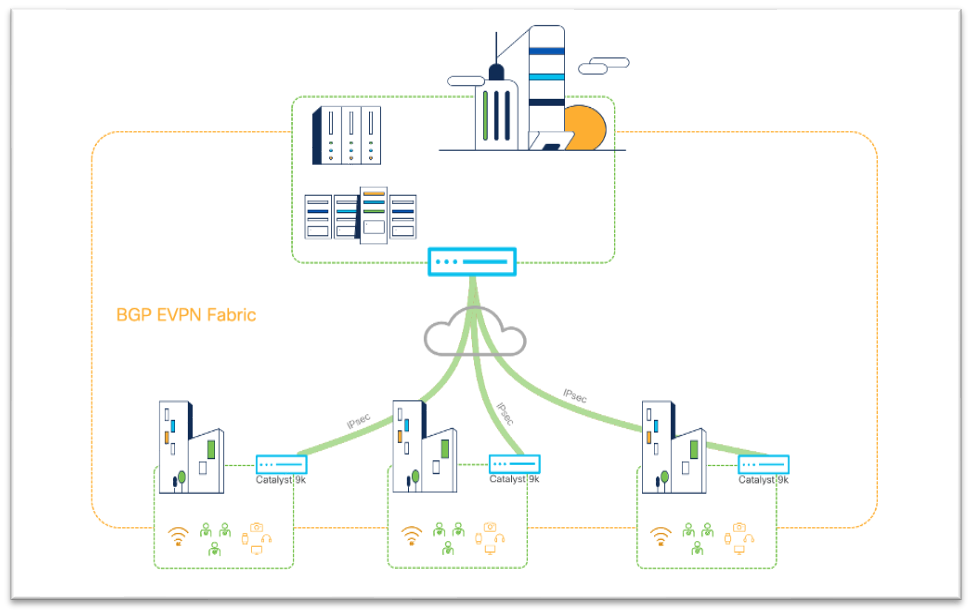
Catalyst 9000: Building Scalable Secure Fabric with IPsec and BGP EVPN
With this unique capability, customers will now be able to scale Layer 3 overlays seamlessly over a secure transport. IPsec tunnels act as an Underlay for the BGP EPVN Fabric that uses BGP for control plane and Vxlan for data-plane. The same fabric can be leveraged to extend Layer 2 connectivity if/when needed to extend Layer 2 connectivity from any of the remote locations to a HQ/Central Location.
Catalyst 9000 switches with programmable ASIC’s and IOS-XE Software have been acting as a foundation for large scale Enterprise networks providing key capabilities with end-to-end connectivity and security. With the addition of these new capabilities, Catalyst 9000 switches are further assisting customers towards their journey to Zero Trust Architecture by securing the transport.
