- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Configuring Type 6 Passwords in IOS XE
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-25-2021 01:51 PM - edited 10-10-2021 01:19 PM
- History
- Requirements
- Configuration Steps
- Managing the Keys
- Changing the Password
- Verification
- These need to be reviewed \ changed.
- These are safe to use.
- FAQ
- References
History
Traditionally Cisco has used several different methods for storing passwords and keys in IOS. The older methods are Type 5 (MD5 hash) & Type7 (Vigenere obfuscation). We enabled Type 7 encryption with the CLI service password-encryption command.
There are some newer methods like Type 8 (SHA256) and Type 9 (SCRYPT). At this time my recommendation is to never use Type 5 or Type 7 and absolutely do not EVER use Type 4.
Today in 2021 the recommendation is to use Type 6, Type 8 and Type 9. Type 6 use strong AES 128-bit encryption for storing passwords. If you interested in the details for Types 0,4,5,6,7,8,9 please check out this other document I wrote. I’d like to make a counting joke here but I won’t.
Note: Using Type 6 has been supported since 2006, IOS 12.3(2)T and possibly earlier!
For a detailed explanation of each password type please see this document I wrote.
Requirements
In this example I’m working with devices that have reset to factory defaults.
- Catalyst 9300 with IOS XE 17.3(3)
Any device that runs modern IOS XE should support Type 6
Configuration Steps
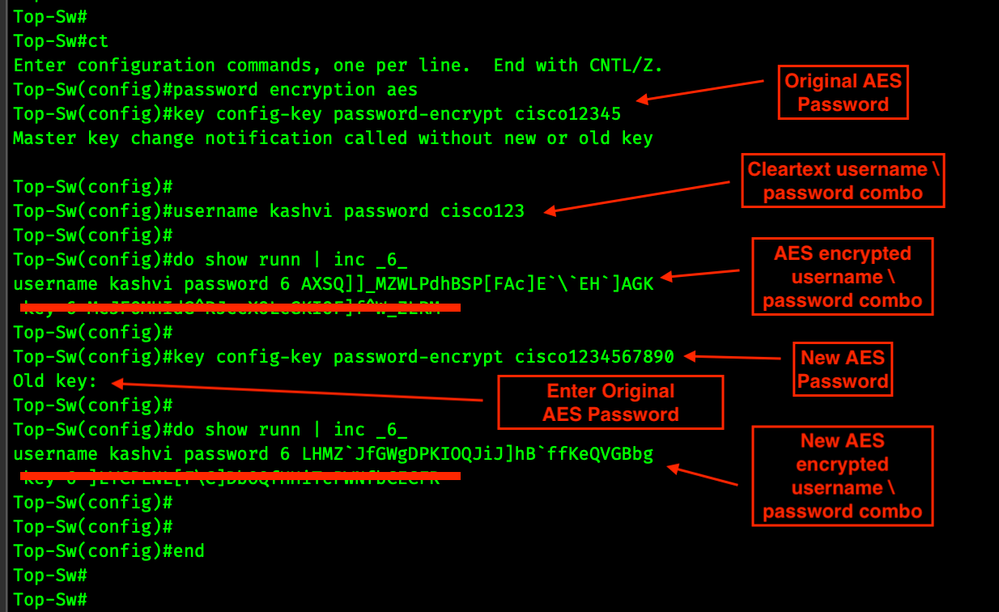
1. Enable AES 128 password encryption
!
configure terminal
password encryption aes
key config-key password-encrypt super-secret-password
end
!
Managing the Keys
The super-secret-password you used is very important. It's very important that you store the key somewhere offline. Be sure to keep in it KeePass, or 1Password or the password vault of your choice. Optimally each device you configure Type 6 on will have a unique Key.
Changing the Password
There shouldn’t be too many reasons to change the password key. However, if you have the old password key, changing it is an easy task with no negative effects.
Verification
These need to be reviewed \ changed.
Look into running config for Type 7 Passwords
show running-config | include _7_
Look into running config for Type 5 Passwords
show running-config | include _5_
These are safe to use.
Look into running config for Type 6 Passwords
show running-config | include _6_
Look into running config for Type 8 Passwords
show running-config | include _8_
Look into running config for Type 9 Passwords
show running-config | include _9_
FAQ
Q: Should we leave service password-encryption in the config?
A: Yes, while it shouldn’t be needed because we’ve enabled Type 6 passwords, leaving service password-encryption in the running config will cause any other Type 5 or Type 7 passwords to be obfuscated instead of being stored in the clear.
Q: Should I store the key ?
A: YES, the key should DEFINITELY be stored. In the event that you need to move this devices config to a new device you will need the key.
Q: What passwords will be converted?
A: According to my tests the following passwords and password types will be converted:
- TACACS server keys (previously in Type 7)
- RADIUS server keys (previously in Type 7)
- vty login passwords (previously in Type 7)
Q: What password types will NOT be converted?
A: According to my tests the following passwords and password types will be NOT be converted:
- enable secret 9
- BGP MD5 authentication password, instead use BGP TCP Authentication Option
- OSPF MD5 authentication password, instead use HMAC Authentication
- HSRP \ VRRP using key-string for authentication, instead use authentication key-chain which will convert to Type 6
Q: Can you revert to non-Type 6 passwords?
A: Reverting to non-Type 6 is a manual process.
First, identify all type 6 passwords
Then issue
no password-encryption aes
Then, revert each of the previously identified Type 6 and reconfigure.
Q: What happens if I need to change the password encryption key?
A: This is typically not needed, however, if you still have the password, good, no problem! Just change it, see the above example.
Q: What happens if I lose the password encryption key?
A: Moving the passwords in their encrypted form to a new box will be impossible.
Q: What happens if I lose the password encryption key and need to change the password encryption key?
A: I'd call Cisco TAC
Q: Where should I look for changes in the running-config?
A: Typically, I’ve seen Type 5 and Type 7 passwords in the following places:
- username kashvi password …
- enable password
- RADIUS key
- TACACS key
- VTY login
- BGP peer password
- MKA preshared key
Q: Can I implement password encryption aes on an existing switch?
A: Yes, of course! Please use the verification commands above to assure that all of your legacy passwords especially Type 5 and Type 7 are converted to the newer Type 6.
Q: I’m deploying a new switch \ router, how should it be configured?
A: Use the configuration script above right from the start. There is no need to use service password-encryption.
Q: In the event I need to use Type 8 or Type 9 which is more secure?
A: Both Type 8 and Type 9 are secure, feel comfortable using either.
Q: I don’t see key config-key password-encrypt in the running config…
A: Yes, you shouldn’t. Keeping the key in clear text would be insecure as it may provide a means to decrypt the passwords. The key is stored in a partition that is not accessible by the administrator.
Q: Can I configure Type 6 encryption on my router if my BGP, OSPF, EIGRP peer router doesn’t support it.
A: Yes! Because the routing protocol’s process on your router will decrypt the password before using it with the peer this should not be a problem.
Q: Should I be using enable password or enable secret?
A: Definitely use enable secret. If both are configured only enable secret is used.
References
Cisco IOS XE Command Reference (key config-key password-encrypt)
Cisco IOS XE Command Reference (password encryption aes)
Encrypt Pre-shared Keys in Cisco IOS Router Configuration
Cisco IOS Command Reference (service password-encryption)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you! This is awesome! (Especially alongside your linked document going over the differences.)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for the compliment @Pierce Vasale ! Glad you like and hope it helps in your network!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you Tim, it´s working perfectly on Cat9XXX Switches.
But have you any idear how to change the password type to 6 on cat 2960X Switch, especially the keys in the Radius and TACACs section? Because it´s working for the username password but not for the Radius and TACACs Key... I have to remove the keys in the section and create a new key 6 entry and the hash I got from a working 9XXX Switch. But I don´t think this is the correct way to do it, right?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@adrian.smithson what IOS version are you using on the 2960X?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Tim Glen I am running 15.2.7E2 on my 2960X
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
No, I don't think the way you are doing it with the 2960 is the way to do it. I'm actually a little surprised it is converting your username password combo. I just tried the same with a 3750X w IOS 15.2(4)E7 and nothing was converted, not the username password and not the RADIUS or TACACS keys.
I've done a little research and I've found this.
https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst2960x/software/15-2_7_e/release_notes/rn-1527e-2960x-xr.html
Features Introduced in Cisco IOS Release 15.2(7)E3
Support for Type 6 AES Encryption password: Beginning with this release, you can specify a Type 6 encrypted key for a TACACS Server. The new command is tacacs server key 6 key-name.
I'm not 100% sure but as far as I can tell from some research, Type 6 was introduced back in mid-2000s to help secure the shared secret in IOS VPN config.
Then as time went on Cisco introduced other encryption algorithms (Type 4,8,9) and slowly rolled the Type 6 into other functions like username password, RADIUS key & TACACS key.
Hope this helps & sorry for the delay in answering.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Tim Glen
Hi Tim,
I had some time to take a closer look on this...
I tested with 2960X 15.2(7)E4 and 15.2(7)E5 and I can confirm with 15.2(7)E5 everything is working as expected like you described for a 9300.
With 2960X 15.2(7)E4 there is no way that the TACACS Key or RADIUS Key get changed to Key 6... Can´t find any information in the release notes but 15.2(7)E5 works great.
Greetings
Adrian S.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Do you have any idea why your instructions do not work on a C1000-8P-E-2G-L with 15.2(7)E6? The switch does not know the command "password encryption aes" nor "key config-key password-encrypt" in config mode.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Tim, great post, very informative. I know there hasn't been any comments on this for a little while, but got a question I'm hoping someone can answer.
I'm wanting to convert all my type 7 password right now and trying to figure out the best way to go about this. I want to use type 8 or 9 for my local "username" passwords and type 6 for my radius shared keys (as type 8/9 is not available for radius shared keys). Is this possible to use both in the same switch config?
If you can use both, and I've already converted my "username" command passwords to type 8 or 9, will entering the "password encryption aes" and "key config-key password-encrypt super-secret-password" commands convert those username password to type 6 or will it continue to use type 8/9 for "username" and only convert the radius shared keys to type 6?
You may have already answered this in the Q&A in you post and pasting below, but just wanted to confirm what to expect. Sounds like it should keep the local "username" passwords as 8 or 9 and only convert my radius server keys?
Q: What passwords will be converted?
A: According to my tests the following passwords and password types will be converted:
- TACACS server keys (previously in Type 7)
- RADIUS server keys (previously in Type 7)
- vty login passwords (previously in Type 7)
Thank you in advance.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Tim Glen neal.gomes@omron.com
hi Tim, and neal,
i have the same interrogation. i want use type 8.
But it doesnt look possible for radius :
TEST(config-radius-server)#key ?
0 Specifies an UNENCRYPTED key will follow
6 Specifies ENCRYPTED key will follow
7 Specifies HIDDEN key will follow
LINE The UNCRYPTED (cleartext) shared key
The problem is that if I configure type 6, it will convert me everything to type 6?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@abtt-39 Type 6 is for reversibly encrypted keys/passwords which need to be used in their original plain-text form - and radius is one of those things which needs the actual key.
Type 8 is a HASH - which cannot be reversed back to the original plain-text and therefore cannot be used for something like radius. Type 8 is suitable for a user secret where the stored hash gets compared to the hash of what a user enters.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
FYI: we've found a bug with type 6 and "subscriber service password"
IOS converts it to type 6 in config but then reads it as type 7 so it breaks service. The workaround is to explicitly configure it with type 7 *after* you have enabled AES encryption and then it keeps working because IOS doesn't convert it.
TAC case in progress ...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this post. Few questions which I am unable to get answer for in any documentation. If there is a need to change the router (RMA , upgrade etc) can the encrypted passwords / PSKs can be simply copied in the encrypted format and pasted onto new box) as long as the master key is known. Does this master key needs to be on the target box prior to pasting in or could it be entered after ? Trying to understand the order of operations. Could there be a situation where a pasted config with encrypted password ends up getting encrypted twice ? Assume a newer or different router model or higher IOS version ? Is there a way to decrypt the keys/password with the master key. Is there a tool on or off box ? Also noticed on ios xe some keys we created for PSKs just go in literally without getting encrypted even though aes password encryption is turned on ? What could be the reason for such behaviour ? Is there a possibility of router getting its config via tftp or some other source with aes password encryption enabled and it never asking the admin interactively for typing in the master key which is typically the case when it’s enabled first time. Thank you !
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@toormehdi ...
> Does this master key needs to be on the target box prior to pasting in or could it be entered after ? Trying to understand the order of operations.
- Yes the encrypted format can be copied and will work as long as and when the same master key is used. It can be entered before or after.
> Could there be a situation where a pasted config with encrypted password ends up getting encrypted twice ? Assume a newer or different router model or higher IOS version ?
- No, IOS will not re-encrypt a key/password already in type 6.
> Is there a way to decrypt the keys/password with the master key. Is there a tool on or off box ?
- Not that I know of although it would be theoretically possible if you had the Cisco algorithm and the key.
>Also noticed on ios xe some keys we created for PSKs just go in literally without getting encrypted even though aes password encryption is turned on ? What could be the reason for such behaviour ?
- AES encryption started with things like VPN keys and has gradually been extended to other passwords and keys in newer IOS versions. You still need "service password-encryption" for everything else.
> Is there a possibility of router getting its config via tftp or some other source with aes password encryption enabled and it never asking the admin interactively for typing in the master key which is typically the case when it’s enabled first time?
- I'm pretty sure this did not work on older IOS but haven't tried it on newer versions. Test thoroughly. But from a security perspective putting your clear text master key in the config with the encrypted literally defeats the purpose of the encryption so just don't even try to do that. If you're going to give away your master key like that then just don't waste your time with encrypting the passwords - leave them in clear text.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I know this thread is old, but I cannot get the conversion of type 7's to type 6's to work on 3750X 15.2(4)E10 switches. The type 7 passwords (i.e. username, TACACS+, RADIUS) do not convert even though both commands take ("key config-key password-encrypt" and "password encryption aes").
What gives?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: