- Cisco Community
- Technology and Support
- DevNet
- DevNet Networking
- Crosswork Automation Hub
- NSO Developer Hub Discussions
- deploy a docker container in k8s cluster from nso6.1 image
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
deploy a docker container in k8s cluster from nso6.1 image
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2023 03:13 AM
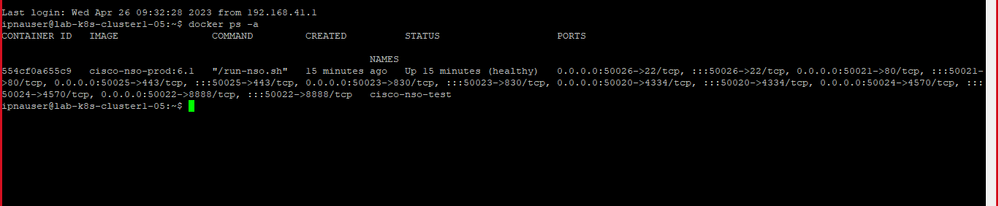
Hi ,I am trying to deploy a docker container in k8s cluster from "nso-6.1.container-image-prod.linux.x86_64.tar". I downloaded this image from cisco. I performed these steps : docker load -i nso-6.1.container-image-prod.linux.x86_64.tar.gz , docker run -itd --name nso-testing2 -p 50130:4334 -p 50131:80 -p 50132:8888 -p 50133:830 -p 50134:4570 -p 50135:443 -p 50136:22 cisco-nso-prod:6.1
so once I perform those commands the container is up and running but I am not able to access the UI or not able to ssh.
Please suggest what is wrong and how to deploy the container successfully ?
Attached the nso guide , please refer page no - 168 for clarity.
attaching screenshot.
- Labels:
-
Developer
-
devops
-
Operations
-
Other NSO Topics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2023 05:07 AM
How are you trying to access the UI and SSH? You need to use the ports exposed, for example port 50026 to reach the container's SSH port (22) and port 50021 to reach the UI port (80).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2023 05:52 AM
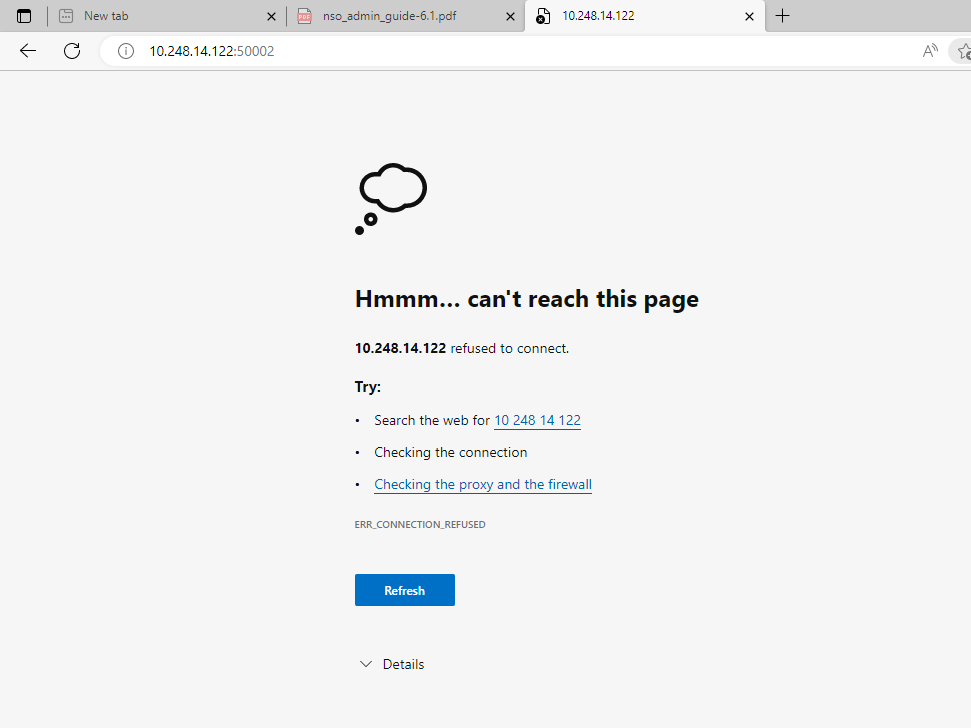
Hi, you can see in the attached image the 50021 is exposes to 80 , hence I should be able to reach the UI with this url- http://10.248.14.122:50021. but not able to reach. Also not able to ssh with 50026. attaching the screen shot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2023 11:24 PM
Great, then you are using the correct port. Can you access the interactive shell on the running container?
docker exec -itnso-testing2 bash
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-26-2023 11:31 PM
Yes I am able to access the interactive shell and i am able to access ncs console. But not able to access from browser.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 03:39 AM
Ok, are the ports open?
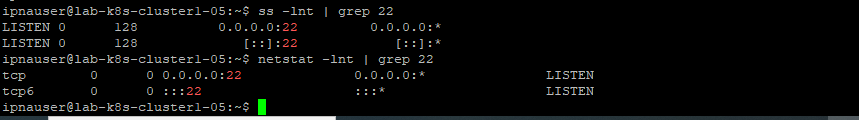
ss -lnt | grep 22
netstat -lnt | grep 22
(Not sure if we use ss or netstat). Maybe check the logs to see if there is anything suspicious? I'm thinking of ncs.log and devel.log especially.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 10:47 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 11:20 PM
Is that in the container or on the docker host?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2023 11:53 PM
The netstat command is performed on docker server but ncs,log and devel.log are from running containers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 12:14 AM
Can you check the open ports in the container too? And if you find nothing, check the ncs.conf settings for CLI and Webui?
Look if we're doing 127.0.0.1, we need to change that to 0.0.0.0 in that case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 01:04 AM
Hi, Please find the details below -
ipnauser@lab-k8s-cluster1-05:~$ docker port bde0282ced02
4334/tcp -> 0.0.0.0:49184
4334/tcp -> :::49184
443/tcp -> 0.0.0.0:49186
443/tcp -> :::49186
4570/tcp -> 0.0.0.0:49183
4570/tcp -> :::49183
80/tcp -> 0.0.0.0:49187
80/tcp -> :::49187
830/tcp -> 0.0.0.0:49185
830/tcp -> :::49185
8888/tcp -> 0.0.0.0:49182
8888/tcp -> :::49182
22/tcp -> 0.0.0.0:49188
22/tcp -> :::49188
ipnauser@lab-k8s-cluster1-05:~$ docker exec -it bde0282ced02 bash
[root@bde0282ced02 /]# ls
Python-3.11.2.tgz boot dev home lib64 lost+found mnt opt root run-nso.sh srv templates usr
bin defaults etc lib log media nso proc run sbin sys tmp var
[root@bde0282ced02 /]# cd /etc/ncs/
[root@bde0282ced02 ncs]# ls
ipc_access ncs.conf ncs.crypto_keys post-ncs-start.d pre-ncs-start.d ssh ssl
[root@bde0282ced02 ncs]# cat ncs.conf
<!-- -*- nxml -*- -->
<!-- Example configuration file for ncs. -->
<ncs-config xmlns="http://tail-f.com/yang/tailf-ncs-config">
<!-- NCS can be configured to restrict access for incoming connections -->
<!-- to the IPC listener sockets. The access check requires that -->
<!-- connecting clients prove possession of a shared secret. -->
<ncs-ipc-access-check>
<enabled>false</enabled>
<filename>${NCS_CONFIG_DIR}/ipc_access</filename>
</ncs-ipc-access-check>
<!-- Where to look for .fxs and snmp .bin files to load -->
<load-path>
<dir>${NCS_RUN_DIR}/packages</dir>
<dir>${NCS_DIR}/etc/ncs</dir>
<!-- To disable northbound snmp altogether -->
<!-- comment out the path below -->
<dir>${NCS_DIR}/etc/ncs/snmp</dir>
</load-path>
<!-- Plug and play scripting -->
<scripts>
<dir>${NCS_RUN_DIR}/scripts</dir>
<dir>${NCS_DIR}/scripts</dir>
</scripts>
<state-dir>${NCS_RUN_DIR}/state</state-dir>
<notifications>
<event-streams>
<!-- This is the builtin stream used by NCS to generate northbound -->
<!-- notifications whenever the alarm table is changed. -->
<!-- See tailf-ncs-alarms.yang -->
<!-- If you are not interested in NCS northbound netconf notifications -->
<!-- remove this item since it does consume some CPU -->
<stream>
<name>ncs-alarms</name>
<description>NCS alarms according to tailf-ncs-alarms.yang</description>
<replay-support>false</replay-support>
<builtin-replay-store>
<enabled>false</enabled>
<dir>${NCS_RUN_DIR}/state</dir>
<max-size>S10M</max-size>
<max-files>50</max-files>
</builtin-replay-store>
</stream>
<!-- This is the builtin stream used by NCS to generate northbound -->
<!-- notifications for internal events. -->
<!-- See tailf-ncs-devices.yang -->
<!-- Required for cluster mode. -->
<stream>
<name>ncs-events</name>
<description>NCS event according to tailf-ncs-devices.yang</description>
<replay-support>true</replay-support>
<builtin-replay-store>
<enabled>true</enabled>
<dir>${NCS_RUN_DIR}/state</dir>
<max-size>S10M</max-size>
<max-files>50</max-files>
</builtin-replay-store>
</stream>
<!-- This is the builtin stream used by NCS to generate northbound -->
<!-- notifications for kicker events. -->
<!-- See tailf-kicker.yang -->
<stream>
<name>kicker-events</name>
<description>NCS event according to tailf-kicker.yang</description>
<replay-support>true</replay-support>
<builtin-replay-store>
<enabled>true</enabled>
<dir>${NCS_RUN_DIR}/state</dir>
<max-size>S10M</max-size>
<max-files>50</max-files>
</builtin-replay-store>
</stream>
<!-- This is the builtin stream used by NCS to generate northbound -->
<!-- notifications forwarded from devices. -->
<!-- See tailf-event-forwarding.yang -->
<stream>
<name>device-notifications</name>
<description>NCS events forwarded from devices</description>
<replay-support>true</replay-support>
<builtin-replay-store>
<enabled>true</enabled>
<dir>${NCS_RUN_DIR}/state</dir>
<max-size>S10M</max-size>
<max-files>50</max-files>
</builtin-replay-store>
</stream>
<!-- This is the builtin stream used by NCS to generate northbound -->
<!-- notifications for service state changes. -->
<!-- See tailf-ncs-plan.yang and tailf-ncs-services.yang -->
<stream>
<name>service-state-changes</name>
<description>Service state changes according to
tailf-ncs-plan.yang and tailf-ncs-services.yang
</description>
<replay-support>true</replay-support>
<builtin-replay-store>
<enabled>true</enabled>
<dir>${NCS_RUN_DIR}/state</dir>
<max-size>S10M</max-size>
<max-files>50</max-files>
</builtin-replay-store>
</stream>
</event-streams>
</notifications>
<!-- Where the database (and init XML) files are kept -->
<cdb>
<db-dir>${NCS_RUN_DIR}/cdb</db-dir>
<!-- Always bring in the good system defaults -->
<init-path>
<dir>${NCS_DIR}/var/ncs/cdb</dir>
</init-path>
</cdb>
<!--
These keys are used to encrypt values of the types
tailf:des3-cbc-encrypted-string, tailf:aes-cfb-128-encrypted-string
and tailf:aes-256-cfb-128-encrypted-string.
For a deployment install it is highly recommended to change
these numbers to something random (done by NCS "system install")
-->
<encrypted-strings>
<external-keys>
<command>${NCS_DIR}/bin/ncs_crypto_keys</command>
<command-argument>${NCS_CONFIG_DIR}/ncs.crypto_keys</command-argument>
</external-keys>
</encrypted-strings>
<logs>
<audit-network-log>
<enabled>false</enabled>
<file>
<name>${NCS_LOG_DIR}/audit-network.log</name>
<enabled>false</enabled>
</file>
</audit-network-log>
<syslog-config>
<facility>daemon</facility>
</syslog-config>
<ncs-log>
<enabled>true</enabled>
<file>
<name>${NCS_LOG_DIR}/ncs.log</name>
<enabled>true</enabled>
</file>
<syslog>
<enabled>true</enabled>
</syslog>
</ncs-log>
<developer-log>
<enabled>true</enabled>
<file>
<name>${NCS_LOG_DIR}/devel.log</name>
<enabled>true</enabled>
</file>
</developer-log>
<developer-log-level>info</developer-log-level>
<audit-log>
<enabled>true</enabled>
<file>
<name>${NCS_LOG_DIR}/audit.log</name>
<enabled>true</enabled>
</file>
</audit-log>
<netconf-log>
<enabled>true</enabled>
<file>
<name>${NCS_LOG_DIR}/netconf.log</name>
<enabled>true</enabled>
</file>
</netconf-log>
<snmp-log>
<enabled>true</enabled>
<file>
<name>${NCS_LOG_DIR}/snmp.log</name>
<enabled>true</enabled>
</file>
</snmp-log>
<webui-access-log>
<enabled>true</enabled>
<dir>${NCS_LOG_DIR}</dir>
</webui-access-log>
<!-- This log is disabled by default if ncs is installed using -->
<!-- the 'system-install' flag. It consumes a lot of CPU power -->
<!-- to have this log turned on, OTOH it is the best tool to -->
<!-- debug must expressions in YANG models -->
<xpath-trace-log>
<enabled>false</enabled>
<filename>${NCS_LOG_DIR}/xpath.trace</filename>
</xpath-trace-log>
<error-log>
<enabled>true</enabled>
<filename>${NCS_LOG_DIR}/ncserr.log</filename>
</error-log>
<progress-trace>
<enabled>true</enabled>
<dir>${NCS_LOG_DIR}</dir>
</progress-trace>
</logs>
<aaa>
<ssh-server-key-dir>${NCS_CONFIG_DIR}/ssh</ssh-server-key-dir>
<!-- Depending on OS - and also depending on user requirements -->
<!-- the pam service value value must be tuned. -->
<pam>
<enabled>true</enabled>
<service>system-auth</service>
</pam>
<external-authentication>
<enabled>false</enabled>
<executable>my-test-auth.sh</executable>
</external-authentication>
<local-authentication>
<enabled>false</enabled>
</local-authentication>
<expiration-warning>prompt</expiration-warning>
</aaa>
<!-- Hash algorithm used when setting leafs of type ianach:crypt-hash, -->
<!-- e.g. /aaa/authentication/users/user/password -->
<crypt-hash>
<algorithm>sha-512</algorithm>
</crypt-hash>
<!-- Disable this for performance critical applications, enabling -->
<!-- rollbacks means additional disk IO for each transaction -->
<rollback>
<enabled>true</enabled>
<directory>${NCS_RUN_DIR}/rollbacks</directory>
<history-size>500</history-size>
</rollback>
<cli>
<enabled>true</enabled>
<!-- Use the builtin SSH server -->
<ssh>
<enabled>false</enabled>
<ip>0.0.0.0</ip>
<port>2024</port>
</ssh>
<prompt1>\u@ncs> </prompt1>
<prompt2>\u@ncs% </prompt2>
<c-prompt1>\u@ncs# </c-prompt1>
<c-prompt2>\u@ncs(\m)# </c-prompt2>
<restricted-file-access>true</restricted-file-access>
<show-commit-progress>true</show-commit-progress>
<suppress-commit-message-context>maapi</suppress-commit-message-context>
<suppress-commit-message-context>system</suppress-commit-message-context>
</cli>
<webui>
<enabled>true</enabled>
<transport>
<tcp>
<enabled>false</enabled>
<ip>0.0.0.0</ip>
<port>8080</port>
</tcp>
<ssl>
<enabled>false</enabled>
<ip>0.0.0.0</ip>
<port>8888</port>
<key-file>${NCS_CONFIG_DIR}/ssl/cert/host.key</key-file>
<cert-file>${NCS_CONFIG_DIR}/ssl/cert/host.cert</cert-file>
<!-- <ha-primary-listen> -->
<!-- <ip>0.0.0.0</ip> -->
<!-- <port>28888</port> -->
<!-- </ha-primary-listen> -->
</ssl>
</transport>
<cgi>
<enabled>true</enabled>
<php>
<enabled>false</enabled>
</php>
</cgi>
</webui>
<restconf>
<enabled>true</enabled>
</restconf>
<netconf-north-bound>
<enabled>true</enabled>
<transport>
<ssh>
<enabled>false</enabled>
<ip>0.0.0.0</ip>
<port>2022</port>
<!-- <ha-primary-listen> -->
<!-- <ip>0.0.0.0</ip> -->
<!-- <port>22022</port> -->
<!-- </ha-primary-listen> -->
</ssh>
<tcp>
<enabled>false</enabled>
<ip>127.0.0.1</ip>
<port>2023</port>
</tcp>
</transport>
</netconf-north-bound>
<netconf-call-home>
<enabled>false</enabled>
<transport>
<tcp>
<ip>0.0.0.0</ip>
<port>4334</port>
</tcp>
</transport>
</netconf-call-home>
<!-- <ha> -->
<!-- <enabled>true</enabled> -->
<!-- </ha> -->
<!-- Make sure that debug tools can be made visible. -->
<hide-group>
<name>debug</name>
</hide-group>
<!-- Override parameters in the submodules of the tailf-ncs.yang module,
preventing setting of those parameters via northbound interfaces
from having any effect, even if the NACM access rules allow it. -->
<java-vm>
<start-command>DEFAULT</start-command>
<run-in-terminal>
<terminal-command>DEFAULT</terminal-command>
</run-in-terminal>
<stdout-capture>
<enabled>true</enabled>
<file>${NCS_LOG_DIR}/ncs-java-vm.log</file>
</stdout-capture>
</java-vm>
<python-vm>
<start-command>DEFAULT</start-command>
<run-in-terminal>
<terminal-command>DEFAULT</terminal-command>
</run-in-terminal>
<logging>
<log-file-prefix>${NCS_LOG_DIR}/ncs-python-vm</log-file-prefix>
</logging>
</python-vm>
<smart-license>
<smart-agent>
<java-executable>DEFAULT</java-executable>
<java-options>DEFAULT</java-options>
<production-url>DEFAULT</production-url>
<alpha-url>DEFAULT</alpha-url>
<override-url>
<url>DEFAULT</url>
</override-url>
<proxy>
<url>DEFAULT</url>
</proxy>
</smart-agent>
</smart-license>
</ncs-config>
[root@bde0282ced02 ncs]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 01:13 AM
The "docker port" command lists the mapping for the container, but doesn't say anything about the status of those ports in the running container.
Can you run the netstat/ss commands in the running container?
docker exec -it <container>
$ ss -lnt | grep 22
or if that fails:
docker exec -it <container>
$ netstat -lnt | grep 22
According to the ncs.conf, the webui is configured to listen on port 8080 so change the port mapping of the container to point to 8080 instead of port 80.
docker exec .... -p 50531:8080 ...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 02:16 AM
[root@bde0282ced02 /]# ss -lnt | grep 22
[root@bde0282ced02 /]# netstat -lnt | grep 22
bash: netstat: command not found
ipnauser@lab-k8s-cluster1-05:~$ docker run -itd --name ciso-nso667 -v /data/nso:/nso -v /data/nso/etc:/etc/ncs -v /data/nso-logs:/log -p 50001:4334 -p 50002:8080 -p 50003:8888 -p 50004:830 -p 50005:4570 -p 50006:443 -p 50007:22 cisco-nso-prod:6.1
19340e1be5dd4038b73098811ce5a4db9660c2c2a0d3e7789e8c86ab0d4577a3
ipnauser@lab-k8s-cluster1-05:~$ docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
19340e1be5dd cisco-nso-prod:6.1 "/run-nso.sh" 5 seconds ago Up 4 seconds (health: starting) 80/tcp, 0.0.0.0:50007->22/tcp, :::50007->22/tcp, 0.0.0.0:50006->443/tcp, :::50006->443/tcp, 0.0.0.0:50004->830/tcp, :::50004->830/tcp, 0.0.0.0:50001->4334/tcp, :::50001->4334/tcp, 0.0.0.0:50005->4570/tcp, :::50005->4570/tcp, 0.0.0.0:50002->8080/tcp, :::50002->8080/tcp, 0.0.0.0:50003->8888/tcp, :::50003->8888/tcp ciso-nso667
ipnauser@lab-k8s-cluster1-05:~$
Still not able to access from browser
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 02:20 AM
Right, there's no SSH-server installed so there's no one listening on that port in the container. You can install that yourself if you need it.
And as for port 80, no one listening on that either because the default port is 8080. Here you can change the port mapping as I suggested earlier or you can change the ncs.conf.
If you want you can use another ncs.conf you can mount in an ncs.conf using "-v" with docker.
Mount the ncs.conf you want to use into /etc/ncs/ncs.conf or /nso/etc/ncs.conf.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2023 06:35 AM
Note that there is an example that does not mount ncs.conf or share a volume with the docker host. See https://gitlab.com/nso-developer/nso-examples/-/tree/main/deployment/netsim-sshkey. If the docker image is loaded, just run the "./setup_ncip.sh". Please have a look at the README for details.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide