- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 05:22 AM
Hi.
I have tried to use the netbox plugin (i guess unofficial) with nso (5.8) to import my devices
I am able to get this working, but I am encountering one little hickup, and wonder if somebody
have a workaround, have tweaked the python code or any other solution
I am using netconf NED to communicate with our equipment.
But, it does not seems that this plugin is supporting netconf, only http, https, telnet and ssh when the device is created in NSO
So, when the import is running:
admin@ncs# netbox-inventory FETCH-DEVICES build-inventory commit true
output # Adding Devices to NSO from NetBox inventory.
devices:
- device: S12341234
address: 14.1.14.1
port: 22
description: mobile-csr
auth-group: CSR-AUTH
device-type:
generic:
ned-id: cisco-iosxr-nc-7.6
protocol: ssh
state: unlocked
source:
context: {"web": "http://79.161.80.21:8000/dcim/devices/5/", "api": "http://79.161.80.21:8000/api/dcim/devices/5/"}
when: 2022-11-29T12:41:47
source: /nso-netbox:netbox-inventory{FETCH-DEVICES}
device-groups:
- NetBoxInventory FETCH-DEVICES
- NetBoxInventory FETCH-DEVICES NCS540
- NetBoxInventory FETCH-DEVICES mobile-csr
- NetBoxInventory FETCH-DEVICES ICE
port 22 is added to the setup, and I have to run the command to attach netconf NED again.
Now, this is not feasible as I am to import 8000 hosts.
using postman, I am able to do this fine
so, i guess it should be possible to configure this with a script. Problem, I am not that good of a developer to make that script, and not even to tweak the netbox plugin python code
Anybody that has encountered this and solved it (the netbox plugin thing)?
Jens
Solved! Go to Solution.
- Labels:
-
Technical product information
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2022 04:50 AM - edited 12-02-2022 04:51 AM
Hi, I testet the code change and the device seems to be imported correctly now with regards to the Netconf NED.
However, the plugin are putting the device in four different groups. Not sure why yet. I did not define any group, so it seems that it is created one group for "tentant, one for Device-Type, one for "Role" and one for "Customer" from Netbox. I guess that is ok, but I would have prefered to define what NSO group I want to add this to. I can have a look at it
Possible completions:
Name for this set of devices. VI-METRO3
which is the
admin@ncs# show devices device-group
NAME MEMBER INDETERMINATES CRITICALS MAJORS MINORS WARNINGS ID
----------------------------------------------------------------------------------------------------------------------------------------------------------
ALL [ S4000TEST-CSR1-CSR1 ] 0 0 1 0 0 cisco-iosxr-nc-7.6
cisco-iosxr-cli-7.43
NetBoxInventory VI-METRO3 [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
NetBoxInventory VI-METRO3 ICE [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
NetBoxInventory VI-METRO3 NCS540 [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
NetBoxInventory VI-METRO3 mobile-csr [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
Anyhow, thanks for the help, below is the imported device:
admin@ncs(config)# show full-configuration devices device S4000TEST-CSR1
devices device S4000TEST-CSR1
address 10.10.10.11
ssh host-key ssh-ed25519
key-data xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
!
ssh host-key-verification none
authgroup CSR-AUTH
device-type netconf ned-id cisco-iosxr-nc-7.6
state admin-state unlocked
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 10:11 AM
Not sure if hpreston (the creator of the code in question) reads the NSO Developer Hub, its probably easier to contact him on github directly.
If you want to take a stab at it yourself you can find the specific code that contains the "protocol" part here
https://github.com/hpreston/nso-netbox/blob/master/python/nso_netbox/netbox_inventory_actions.py
Check line 22.
| # Constancs and Values for use | |
| PROTOCOL_PORTS = { | |
| "ssh": 22, | |
| "telnet": 23, | |
| "http": 80, | |
| "https": 443, | |
| } |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 10:13 AM
ohh and also in the nso-netbox.yang
https://github.com/hpreston/nso-netbox/blob/master/src/yang/nso-netbox.yang
Line 116
leaf connection-protocol {
tailf:info "The type of connection protocol to connect to the device with.";
type enumeration {
enum ssh;
enum telnet;
enum http;
enum https;
}
default ssh;
}
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2022 12:20 AM
Did a quick hack to add netconf as a device-type, also did an unsafe change to disregard the ssl cert. When I have time Ill try to fix it in a better way (the certificate). You can find my changes in my fork https://github.com/hniska/nso-netbox
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-02-2022 04:50 AM - edited 12-02-2022 04:51 AM
Hi, I testet the code change and the device seems to be imported correctly now with regards to the Netconf NED.
However, the plugin are putting the device in four different groups. Not sure why yet. I did not define any group, so it seems that it is created one group for "tentant, one for Device-Type, one for "Role" and one for "Customer" from Netbox. I guess that is ok, but I would have prefered to define what NSO group I want to add this to. I can have a look at it
Possible completions:
Name for this set of devices. VI-METRO3
which is the
admin@ncs# show devices device-group
NAME MEMBER INDETERMINATES CRITICALS MAJORS MINORS WARNINGS ID
----------------------------------------------------------------------------------------------------------------------------------------------------------
ALL [ S4000TEST-CSR1-CSR1 ] 0 0 1 0 0 cisco-iosxr-nc-7.6
cisco-iosxr-cli-7.43
NetBoxInventory VI-METRO3 [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
NetBoxInventory VI-METRO3 ICE [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
NetBoxInventory VI-METRO3 NCS540 [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
NetBoxInventory VI-METRO3 mobile-csr [ S4000TEST-CSR1 ] 0 0 0 0 0 cisco-iosxr-nc-7.6
Anyhow, thanks for the help, below is the imported device:
admin@ncs(config)# show full-configuration devices device S4000TEST-CSR1
devices device S4000TEST-CSR1
address 10.10.10.11
ssh host-key ssh-ed25519
key-data xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
!
ssh host-key-verification none
authgroup CSR-AUTH
device-type netconf ned-id cisco-iosxr-nc-7.6
state admin-state unlocked
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-05-2022 12:24 AM
According to the nso-netbox documentation i
https://github.com/hpreston/nso-netbox
4. In addition to adding the devices that match the inventory, several device-groups are created for the inventory. There will be groups for:
- The entire
netbox-inventoryinstance - The
device-typesof each device - The
device-rolesfor each device - THe
tenantsfor each device
Note: even if the attributes are NOT used as filters in the inventory, the groups are still created
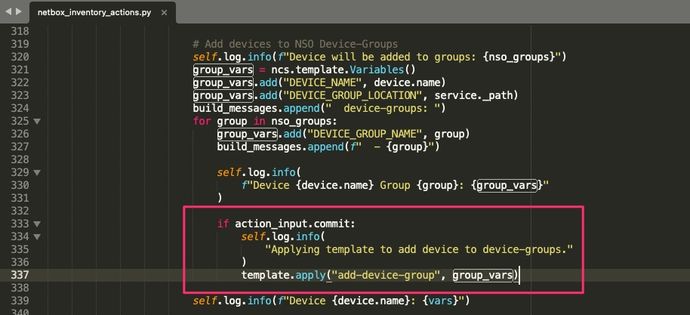
For a quick fix to disable the group adding you can just remove the template.apply(add-device-group)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-04-2023 08:59 PM
I want to use NetBox activ as a inventory for my RFS services…
When operator are creating a new device for core equipment, I want the service to locate in netbox, available linecard, interface, and interface type that are available for this specific device.
so operator x are setting up a new PE.
This is pre defined in netbox with a specific set of interfaces (device is not setup physicaly at this point, I want the device to be prepared for services beforehand). I suppose, I want to preload the hardware in to NSO as an inventory with all interfaces prepared.
usecase: is to preapere a device for device swap from one model to another.
don’t know if this make sense, but I wanted to get some feedback on this.
what would be a good approaches to start with?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide