- Cisco Community
- Technology and Support
- Networking
- Other Network Architecture Subjects
- Re: Routed port versus transit vlan for intervlan routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 09:22 AM
Hi,
I have a network I need to set up for a client. 1 Firewall and 2 Cisco C1000.
On the Cisco C1000, I have created 5 VLANs (VLAN10,20,30,40,50 for Management, Data, Servers, Wireless, and Printers). Each VLAN is an SVI with the following configurations:
interface vlan 10
ip address 192.168.10.1 255.255.255.0
etc... and so on.
Uplink ports are aggregated and directly connected to the Firewall (4 ports). Portchannel1
I currently have my port-channel1 to be configured as a routed port:
interface po1
no switchport
ip address 192.168.255.2 255.255.255.0
and the configuration on the Firewall for the port-channel is 192.168.255.1 255.255.255.0
OR the other option I could create is a transit VLAN and trunk my Cisco C1000 uplink port and create an 802.1Q trunk on the Firewall (for router on a stick design).
I am very curious about the design aspect of a routed port versus creating a transit vlan? What could be the potential complications for both design?
I chose routed port because I read that all layer 2 traffic stays on the switch, so the firewall does not have to worry about STP.
Any suggestions would help me. The last thing I do is set up the network using routed port and it causes more issue later on, so I would like to take everything consideration now.
Thanks for your help!
Solved! Go to Solution.
- Labels:
-
Other Network
-
Other Networking
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 12:00 AM
Perhaps it is just a matter of semantics but I think we have different understanding of what is a transit vlan. My understanding of the term is that a transit vlan is where you are doing inter vlan routing on a L3 switch and you configure a separate vlan which is used to connect to a router and that vlan is used to forward traffic which needs to go to remote destinations. So inter vlan traffic is routed on the switch and remote traffic is forwarded to router using transit vlan. These are similar and would be used if you are doing inter van routing on the switch. Using 802.1Q trunk would be for situations where the switch is doing layer 2 forwarding and the inter vlan routing is done on the upstream router/firewall.
One use case for a transit vlan rather than routed port is if you have multiple switches doing inter vlan routing and you want each switch to be able to forward remote traffic to the upstream router/firewall and you have a single connection to the upstream router/firewall..
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2023 09:56 AM - edited 02-02-2023 03:08 AM
for me both serve same purpose, using L3 between two L3 device but case that we use transit VLAN instead of router port is in DataCenter or enterprise campus
where we use SW and we need to use etherchannel, here some platform (SW) not support L3 etherchannel so the best solution is using
transit VLAN across L2 etherchannel.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 01:19 AM
Hello,
generally speaking, if you can avoid it, a firewall should not be used for routing internal networks. The purpose of the firewall is (obviously) to act as a security device. The C1000 is the router, and should be used as such. Configuring the firewall as a router can become quite tedious, as by default, the firewall denies everything, whereas a router allows everything. That said, I would say your current setup (Vlans on the C1000 and a L3 port-channel to the firewall) is a sound design, and best practice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 02:23 PM
There are several aspects of the original post that I do not understand. Starting with this " Each VLAN is an SVI with the following configurations" If the C1000 is a layer 2 switch then how would it support multiple SVI?
And this statement "Uplink ports are aggregated and directly connected to the Firewall (4 ports). Portchannel1 " If there are 5 vlans then why only 4 ports connecting to firewall?
And this statement "I currently have my port-channel1 to be configured as a routed port". If the port channel is to be carrying 4 (or perhaps 5) vlans why would you configure a single IP address?
I agree with @Georg Pauwen that in general it is not advisable to have a firewall do routing for internal networks. But in the environment described the original post I am not sure that there is any alternative. Unless I am mistaken the C1000 is a layer 2 switch. What other alternative is available if you have a firewall and 2 layer 2 switches?
If we ignore the particular environment described in the original post there is an interesting question "I am very curious about the design aspect of a routed port versus creating a transit vlan?" I believe that this question assumes that inter vlan routing is to be done on the switch and traffic toward outside is to be forwarded to the firewall. In this case there is a real question of benefit of routed port vs SVI. If the connection is a single switch connecting to the firewall then I believe that there is a clear advantage of using a routed port (mostly that it eliminates traffic from BPDU etc.
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 03:09 PM
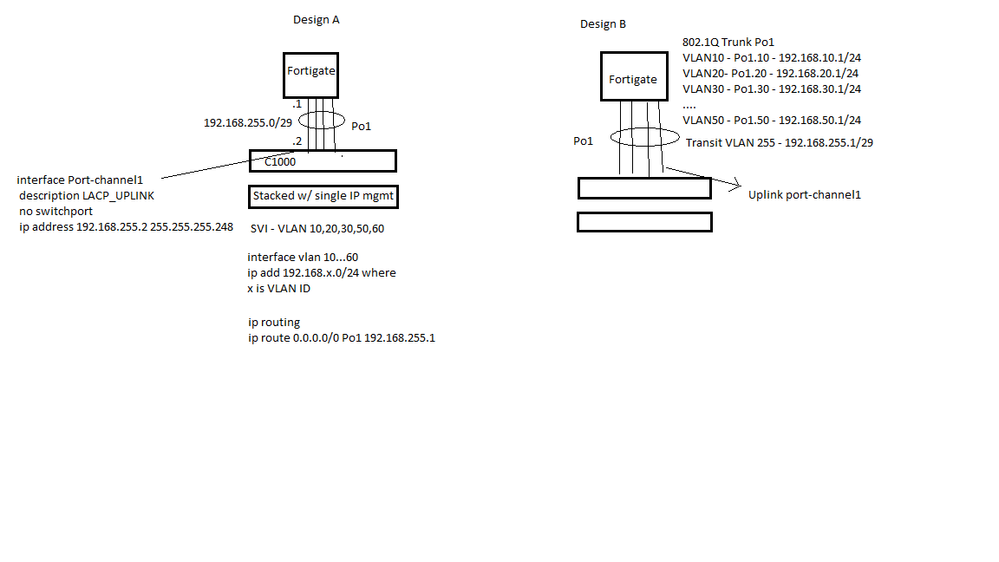
Here is a picture for better clarify of what I was trying to choose between for my client's environment.
Design A - using routed port or Design B - using 802.1Q Trunk with transit VLAN.
I decided to opt for Design A since we only have 1 Fortigate and I do want to keep Layer 2 traffic to stay within the switch. Also, Cisco Catalyst is a Layer 2 with limited Layer 3 capabilities (which is a confusion point), I can create static routes (16 max) and SVI, which is why I opted for Design A, had C1000 been a purely Layer 2 device, I have no option but to use 802.1Q Trunk, router on a stick method.
So with that said, I was always curious why using a "transit vlan" with 802.1Q trunk is an option because you have to use trunk ports, etc. Wouldn't routed port be a less complex method? Then, I was reading into a few articles mentioning that router on a stick method is a good option with a Firewall, because you can put each sub interfaces into their own zones and allow traffic to be inspected and get more visibility on the Firewall. However, all the switching will have to pass through the uplink to be inspected which will require resources on the Firewall.
Reading through the community posts and you guys' response, it seems like we want to keep Layer 2 traffic at Layer 2 due to the switch's higher switching bandwidth capability of 100Gbps versus going to the Firewall of 4 Gbps (4 interfaces for Portchanel 1 gig per interface).
" In this case there is a real question of benefit of routed port vs SVI. If the connection is a single switch connecting to the firewall then I believe that there is a clear advantage of using a routed port (mostly that it eliminates traffic from BPDU etc."
I agree with you on this.
I think I have made a decision. But what I wanted to truly understand is what is a use case for using a "transit vlan" and trunk like for uplink port and its benefit like the design below? is it use in Data centers? and is there a benefit for me to be using it on a 1 branch office.
That is all. Thank you for all your replies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2023 03:13 PM
Thank you. I appreciate that. I was just worried whether it will cause some routing issues or whatever with the routed design, but it seems to be working fine and best practice is what I truly wanted for my client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 12:00 AM
Perhaps it is just a matter of semantics but I think we have different understanding of what is a transit vlan. My understanding of the term is that a transit vlan is where you are doing inter vlan routing on a L3 switch and you configure a separate vlan which is used to connect to a router and that vlan is used to forward traffic which needs to go to remote destinations. So inter vlan traffic is routed on the switch and remote traffic is forwarded to router using transit vlan. These are similar and would be used if you are doing inter van routing on the switch. Using 802.1Q trunk would be for situations where the switch is doing layer 2 forwarding and the inter vlan routing is done on the upstream router/firewall.
One use case for a transit vlan rather than routed port is if you have multiple switches doing inter vlan routing and you want each switch to be able to forward remote traffic to the upstream router/firewall and you have a single connection to the upstream router/firewall..
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2023 07:08 AM
Good that you wrote about it. I was wondering myself what that transit vlan was doing on an 802.1Q trunk.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2023 12:40 AM
I am glad that my explanations have been helpful. Thank you for marking this question as solved. This will help other participants in the community to identify discussions which have helpful information. This community is an excellent place to ask questions and to learn about networking. I hope to see you continue to be active in the community.
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide