- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: FTD intervlan questioning,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 08:49 AM
Scenario,
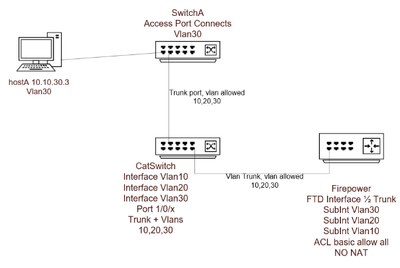
Host-A(10.10.30.3/24) connects to access port on SwitchA with various other vlans also configured via access ports. SwitchA connects on a Trunk port to a CatSwitch. Firepower inside ½ interface trunks to CatSwitch. On The CatSwitch 3 vlans; interfaced as Vlan10(10.10.10.1/24), Vlan20(10.10.20.1/24) and Vlan30(10.10.30.1/24). On FTD ½ interface, 3 Subinterfaces configured Vlan10 (10.10.10.2/24), Vlan20(10.10.20.2/24), and Vlan30(10.10.30.2/24). Vlans can ping only respective Vlans on FTD, but non of which can communicate with the other from hosts to FTD point of contact.
Firewall can ping hostA (10.10.30.3/24); but hostA PC can ping only Vlan30(those on same subnet) FTD. hostA cannot ping any other Vlans configured on FTD that is not Vlan30. However, I believe this to be a functionality by design.
Question, is it possible to configure and associate a 1/3 interface, virtual bridge on a VTP trunk, point trunk to Vlan1 access port on Catswitch to enable intervlan routing btw at FTD and Catswitch? if better pls instruct?
Solved! Go to Solution.
- Labels:
-
Small Business Routers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:53 AM
Now I get it what you meaning when I see your other post'
HostA can ping HostB' each host in different vlan' but hostA can not ping to vpan of hostB in FW.
This not need any acl or config because it not work' fw not like Router you can ping from one interface to other through router' in fw this by defualt can not be done.
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 09:23 AM
Please draw your topolgy' this your second post and I try to help you but I dont get how your topolgy connect.
Thanks alot
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 01:54 PM
Question: is it possible to configure and associate a 1/3 interface, virtual bridge on a VTP trunk, point trunk to vlan1 access port on Catswitch to enable intervlan routing btw at FTD and Catswitch?
[cid:image001.png@01DA8B4B.A85742B0]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 02:31 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2024 11:12 PM
It so clear now,
In CatSW you have Vlan SVI and in FW you have Vlan subinterface.
HostA must have IP of Vlan subinterface of FW as GW and all other host in all vlan must have IP of vlan subinterface of FW as GW.
If some have GW of vlan SVI of CatSW and other have GW of FW vlan subinterface the traffic is asymmetric and drop by FW (drop by inspection not by acl).
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2024 05:23 PM
Thanks for your response MHM. Yes, CatSW Vlan SVI and FW SubIterface are in same subnet, and can readily ping each other. Yes, when you say asymmetric, yes the difference between L2 SVI (at CatSW) and L3 SVI (routed Sub-Interface at FW). So in the case where HostA pings a Vlan that is not in its subnet the FW is not able to respond back or request timeout; and you indicate, that is because packet is dropped by inspection, but not an ACL Rule. So two questions, 1-what does drop by inspection mean? and 2-Is there a solution to that? Like is it possible, to configure FW 1/3 interface as a VBI as trunk port, point trunk to Vlan1 access port on Catswitch in order to allow for Intervlan routing between the FTD VLANs and Catswitch and GW VLANs? -thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 01:47 PM
Hi friend'
I see your new post so I retrun to your previous post and see your reply
Anyway
Why you not use subinterface IP in FW the GW of all host of all vlan?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 02:01 PM
Thanks for your response. Please see my diagram and writeup and follow up questions. Ping request between hostA and lets say Vlan30 at FP works; however, any other ping request between hostA and any other Vlan that is not Vlan30 at FP does not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 02:05 PM
HostA is in vlan30?
If yes and you use gw of subinterface of FW in hostA then
The subinterface of vlan's must be in same zone in fpr.
Did you config zone inside and include all subinterface vlan in this zone?
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 03:49 PM
Yes, I have an FP Inside zone ACL that includes all subinterfaces of VLANs and allows any ipv4 on any port. As described above, FTD can ping any vlan. but hosts in one vlan cannot communicate with hosts on a different vlan at the FTD. I think this may be the way FTD is suppose to work when your going from L2 Interface to an L3 subinterface, but I am not an expert so I don't know.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-17-2024 11:52 PM
Share how you config interface
And config ACL
Thanks
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-18-2024 09:27 AM
Unable to copy
-Nothing dynamic
1/2 Inside interface, no-name, routed
SubInterface vlan10, Id 10, Ip address as shown in diagram, routed
SubInterface vlan10, Id 20, Ip address as shown in diagram, routed
SubInterface vlan10, Id 30, Ip address as shown in diagram, routed
ACL
- Inside_zone (routed, Inside, Outside, Any Ipv4, Any port)
- Outside_zone (routed, Outside, Inside, Any-Ipv4, Any port)
No nat
All works as previously described
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 09:53 AM
Now I get it what you meaning when I see your other post'
HostA can ping HostB' each host in different vlan' but hostA can not ping to vpan of hostB in FW.
This not need any acl or config because it not work' fw not like Router you can ping from one interface to other through router' in fw this by defualt can not be done.
MHM
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide