1:1 Static NAT, shouldn't this be simple ISR C1121-4P
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 06:33 AM
Hi all, I'm new to cisco and I have this currently running on an RV260 which config is shown very differently in XML, but due to the 30 limit on NAT entries It was recommended to upgrade to ISR. (C1121-4P)
I have 1:1 NAT between two LANS private networks.
Interface 0/1/2 is VLAN2 with 10.10.11.200 255.255.0.0
Interface 0/1/3 in VLAN3 with 10.227.113.132 255.255.255.128
I have approx 80 static nats to enter but keeping it to one for testing.
traffic on port 80 into VLAN3 10.227.113.150 translate to 10.10.11.50 out of VLAN3.
What am I missing? is it an ACL, routes or License maybe?
Config....
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport mode access
!
interface GigabitEthernet0/1/1
shutdown
!
interface GigabitEthernet0/1/2
switchport access vlan 2
!
interface GigabitEthernet0/1/3
switchport access vlan 3
!
interface Vlan1
ip address 10.11.11.200 255.255.0.0
!
interface Vlan2
ip address 10.10.11.200 255.255.0.0
!
interface Vlan3
ip address 10.227.113.132 255.255.255.128
ip access-group TEST in
!
ip http server
ip http authentication local
ip http secure-server
ip forward-protocol nd
ip nat inside source static tcp 10.10.11.50 80 10.227.113.150 80 extendable
!
!
ip access-list extended TEST
100 permit tcp any eq www any eq www
!
!
!
- Labels:
-
ISR 1000 Series
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 07:33 AM - edited 08-12-2022 07:34 AM
You have NAT config on the interface :
interface Vlan3
ip nat outside
!
interface Vlan2
ip nat inside
!
interface Vlan1
ip nat inside
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 08:05 AM
Hi BB.
Yes. I did have that in previous tests its Vlan2 & Vlan3 im NATing.
tried those entries and still no response from webserver @ 10.10.11.50:80 when calling 10.227.113.150:80.
The webserver is working fin in the LAN on 10.10.11.50:80
New config....
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport mode access
!
interface GigabitEthernet0/1/1
shutdown
!
interface GigabitEthernet0/1/2
switchport access vlan 2
!
interface GigabitEthernet0/1/3
switchport access vlan 3
!
interface Vlan1
ip address 10.11.11.200 255.255.0.0
!
interface Vlan2
ip address 10.10.11.200 255.255.0.0
ip nat inside
!
interface Vlan3
ip address 10.227.113.132 255.255.255.128
ip nat outside
ip access-group TEST in
!
ip http server
ip http authentication local
ip http secure-server
ip forward-protocol nd
ip nat inside source static tcp 10.10.11.50 80 10.227.113.150 80 extendable
!
!
ip access-list extended TEST
100 permit tcp any eq www any eq www
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 08:54 AM
i do not see your routing to outside ? from router are you able to ping outside 8.8.8.8 ?
you need to add default route towards ISP - ip route 0.0.0.0 0.0.0.0 10.227.113.X (X is ISP side IP)
Also for testing remove ACL In from outgoing intercace.
interface Vlan3
no ip access-group TEST in
intiate traffic from outside and check translation : (worth enable debug, see if the request coming to your router for the ip - 10.227.113.150)
show ip nat translations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 09:13 AM
Hi BB.
The networks are isolated from the internet. What route should I apply?
ip route 0.0.0.0 0.0.0.0 10.227.113.132 or 129?
The outside network is...
Interface IP : 10.227.113.132
Subnet Mask : 255.255.255.128
Gateway : 10.227.113.129
NAT Range : 10.227.113.133-10.227.113.254
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 09:24 AM
add below :
ip route 0.0.0.0 0.0.0.0 10.227.113.129
from router you should able to ping 10.227.113.129, and also 8.8.8.8 before you go next level
still issue make sure you post below output :
show run
show ip route
show ip interface brief
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 11:24 AM
BB.
In can ping from router to 10.227.113.129 OK.
Target IP address: 10.227.113.129
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.227.113.129, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
this works with or without "ip route 0.0.0.0 0.0.0.0 10.227.113.129"
8.8.8.8 wont work as I explained, the networks have no internet connection.
Ping from an outside pc to the NATed address is ok also.
Pinging 10.227.113.150 with 32 bytes of data:
Reply from 10.227.113.150: bytes=32 time<1ms TTL=255
Reply from 10.227.113.150: bytes=32 time<1ms TTL=255
Reply from 10.227.113.150: bytes=32 time<1ms TTL=255
Reply from 10.227.113.150: bytes=32 time<1ms TTL=255
Ping statistics for 10.227.113.150:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms
show running-config....
version 17.5
service timestamps debug datetime msec
service timestamps log datetime msec
service call-home
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform hardware throughput crypto 50000
!
hostname GARDIS-CB
!
boot-start-marker
boot-end-marker
!
!
enable secret 9
enable password
!
no aaa new-model
!
!
!
!
!
!
!
!
!
!
login on-success log
!
!
!
!
!
!
!
subscriber templating
multilink bundle-name authenticated
!
!
!
crypto pki trustpoint TP-self-signed-
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-
revocation-check none
rsakeypair TP-self-signed-
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-
certificate self-signed 01 nvram:IOS-Self-Sig#5.cer
crypto pki certificate chain SLA-TrustPoint
certificate ca 01 nvram:CiscoLicensi#1CA.cer
!
!
license udi pid C1121-4P sn
memory free low-watermark processor 70642
!
diagnostic bootup level minimal
!
spanning-tree extend system-id
!
username admin privilege 15
username cisco privilege 15
!
redundancy
mode none
!
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport mode access
!
interface GigabitEthernet0/1/1
shutdown
!
interface GigabitEthernet0/1/2
switchport access vlan 2
!
interface GigabitEthernet0/1/3
switchport access vlan 3
!
interface Vlan1
ip address 10.11.11.200 255.255.0.0
!
interface Vlan2
ip address 10.10.11.200 255.255.0.0
ip nat inside
!
interface Vlan3
ip address 10.227.113.132 255.255.255.128
ip nat outside
!
ip http server
ip http authentication local
ip http secure-server
ip forward-protocol nd
ip nat inside source static tcp 10.10.11.50 80 10.227.113.150 80 extendable
ip route 0.0.0.0 0.0.0.0 10.227.113.129
!
!
!
!
!
!
control-plane
!
!
line con 0
stopbits 1
line vty 0 4
password ########
login
transport input ssh
line vty 5 14
password ##########
login
transport input ssh
!
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
!
!
!
!
!
!
end
#show ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, m - OMP
n - NAT, Ni - NAT inside, No - NAT outside, Nd - NAT DIA
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
H - NHRP, G - NHRP registered, g - NHRP registration summary
o - ODR, P - periodic downloaded static route, l - LISP
a - application route
+ - replicated route, % - next hop override, p - overrides from PfR
& - replicated local route overrides by connected
Gateway of last resort is 10.227.113.129 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 10.227.113.129
10.0.0.0/8 is variably subnetted, 5 subnets, 3 masks
C 10.10.0.0/16 is directly connected, Vlan2
L 10.10.11.200/32 is directly connected, Vlan2
C 10.227.113.128/25 is directly connected, Vlan3
L 10.227.113.132/32 is directly connected, Vlan3
L 10.227.113.150/32 is directly connected, Vlan3
show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0/0 unassigned YES NVRAM administratively down down
GigabitEthernet0/0/1 unassigned YES NVRAM administratively down down
GigabitEthernet0/1/0 unassigned YES unset down down
GigabitEthernet0/1/1 unassigned YES unset administratively down down
GigabitEthernet0/1/2 unassigned YES unset up up
GigabitEthernet0/1/3 unassigned YES unset up up
Vlan1 10.11.11.200 YES manual down down
Vlan2 10.10.11.200 YES NVRAM up up
Vlan3 10.227.113.132 YES NVRAM up up
Regards Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 01:34 PM
ok, i was in the impression that IP address was provided by ISP, So you mean the router is not connected to Internet?
from what IP address (source IP) you able to ping 10.227.113.150
how is your network, is this Lab ? or real ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-12-2022 01:50 PM - edited 08-12-2022 01:50 PM
ping tested with the gateway ip of 129 (just tested by setting my PC as 129, this is in lab environment, I don't have a real world gateway here).
Also tested with 133 and 140. Should also be ok for the range all the way up to 254.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2022 02:08 AM
If this LAB you should have confg as below :
PC---(gi0/1/3)---Router---(G0/1/2)--Lan
PC configuration should be 10.227.113.129 - subnetmask 255.255.255.128 gateway 10.227.113.132
Lan segment should be your web server 10.10.11.50 subnet mask 255.255.0.0 gateway 10.10.11.200
check on the router
#show ip nat translations
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-13-2022 01:56 PM
Hi BB.
To confirm, yes, your config is what I have.
!
!
!
!
!
!
interface GigabitEthernet0/0/0
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/0/1
no ip address
shutdown
negotiation auto
!
interface GigabitEthernet0/1/0
switchport mode access
!
interface GigabitEthernet0/1/1
shutdown
!
interface GigabitEthernet0/1/2
switchport access vlan 2
!
interface GigabitEthernet0/1/3
switchport access vlan 3
!
interface Vlan1
ip address 10.11.11.200 255.255.0.0
!
interface Vlan2
description BPSN
ip address 10.10.11.200 255.255.0.0
ip nat inside
!
interface Vlan3
description JPC
ip address 10.227.113.132 255.255.255.128
ip nat outside
!
ip http server
ip http authentication local
ip http secure-server
ip forward-protocol nd
ip nat inside source static tcp 10.10.11.50 80 10.227.113.150 80 extendable
ip route 0.0.0.0 0.0.0.0 10.227.113.129
!
!
!
!
!
!
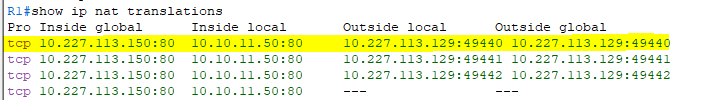
#show ip nat translations
Pro Inside global Inside local Outside local Outside global
tcp 10.227.113.150:80 10.10.11.50:80 --- ---
Total number of translations: 1
Still no access to my webserver.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2022 02:28 AM
#show ip nat translations
Pro Inside global Inside local Outside local Outside global
tcp 10.227.113.150:80 10.10.11.50:80 --- ---
Total number of translations: 1that shows there is no connection intiated from client end
on the router enable Debug - for NAT and Look what transaction getting hit on the router.
when the client initiates the connection HTTP://10.227.113.150
on router show IP nat translation: you see as the example below. (I take this as Cisco 1K Router real hardware)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2022 06:27 AM
I'm having some issue with debug?
Can you show me how to enable and show the log please?
GARDIS-CB#debug ip nat
% Incomplete command.
GARDIS-CB#debug ip nat ?
<1-99> Access list forced
WORD Access list name
ha High Availability debugging
The only reference I can find is by "show ip nat statistics" and watch the counter increasing. The counter does not increase when I try to access the webserver.
show ip nat statistics
Total active translations: 1 (1 static, 0 dynamic; 1 extended)
Outside interfaces:
Vlan3
Inside interfaces:
Vlan2
Hits: 0 Misses: 0
Expired translations: 0
Dynamic mappings:
nat-limit statistics:
max entry: max allowed 0, used 0, missed 0
In-to-out drops: 0 Out-to-in drops: 0
Pool stats drop: 0 Mapping stats drop: 0
Port block alloc fail: 0
IP alias add fail: 0
Limit entry add fail: 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2022 10:05 AM
from PC you having IP 129, what happens when you type HTTP://10.227.113.150
Can you post the show version from device?
ipconfig /all from IP, also route print
from web server also ipconfig /all - route print
If you do not see the IP nat translation, does request not come to the router at all ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-14-2022 04:08 PM
Hello
@ruggrat wrote:
traffic on port 80 into VLAN3 10.227.113.150 translate to 10.10.11.50 out of VLAN3.
So just to confirm web server 10.227.113.150 needs to be seen with vlan 2 ip addresss if/when web server resonds to vlan 2 host or a vlan 2 host connects to web server?
If so then:
interface Vlan2
ip nat inside
interface Vlan3
ip nat outside
ip nat outside source static tcp 10.227.113.150 80 10.10.11.50 80
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul