- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: 5508-X “Advanced Routing” scenario
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-14-2019 07:47 PM - edited 03-24-2019 06:46 AM
Hello... I posted an extremely similar discussion but I believe I may have explained it and myself incorrectly. Thank you regardless to those who assisted.
Here is my situation; I have 2 already established and functioning networks.
Router 1, 10.0.1.1, is giving out 10.0.1.101-10.0.1.120.
Router 2, 10.0.2.1, is giving out 10.0.2.101-10.0.2.120
Both of those Routers are residential WiFi Routers and they themselves have static IPS through Cisco 5508-X and both have Internet access.
What I want to do is create a link between both LANS of each router.
Simply put, I want anyone on 10.0.1.x to access (specifically) my NAS on 10.0.2.115.
I know that to connect 2 Networks I need a L3 Device...
Would I be able to utilize Gigabitethernet 6 and 7 to link both routers? They need no internet access GE 6 and 7 only access to connect to the other LAN.
I am to believe each Interface on my 5508 is L3 so I thought this would be a solution.
where I am lost at is how to deploy this. Such as would the GE 6&7 be their own Subnets or would they use an up from each router they connect to like 10.0.1.114 and 10.0.2.114 to extend off the WiFi routers. Would i need NAT for both interfaces to communicate? As I said I just want straight across the board access. I was also thinking of making both 6/7 security level 90 opposed to 100 as my other interfaces.
any guidence would be wonderful
Solved! Go to Solution.
- Labels:
-
LAN Switching
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 05:06 AM
It certainly is possible to implement a layer 3 switch and to connect a switch interface to each of the routers. And it certainly is possible to configure 2 vlans and to assign each of the switch interfaces to a vlan, and to configure vlan interfaces for the 2 subnets. In doing this you do not need (and do not want) any address translation. You would need a route configured on each of the routers for the other user subnet with the switch interface as the next hop. And I believe this is the problem because you have told us that one of the routers seems to not have support for configuring additional routes.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 10:19 PM
Hi,
Now if 10.0.1.x is the initiating Subnet would I also need an IP Route on the 10.0.2.x? I ask because with the current firmware of DDWRT my ability to add an IP Route does not function. If I absolutely do need to do an IP route for some reversal reason, I will find a modified firmware that does support it.
Yes, You will a route require at both small routers.
You mention the next hop... So on my 10.0.1.x would I have an IP Route such 10.0.2.0 255.255.255.0 10.0.2.115? Or would I need to specify 10.0.2.111 255.255.255.0 10.0.2.115? Or does it need to hit the Router IP to communicate with the other IP's so 10.0.2.1 255.255.255.0 10.0.2.115.
You will need route in such format:
Route 10.0.2.0 255.255.255.0 10.0.1.115 (10.0.2.0/24 is the destination subnet/network and 10.0.1.115 is the next hope (Switch IP address which will responsible for routing.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 01:41 AM
Hello,
just for clarification: do you have BOTH routers connected the SAME firewall currently ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 04:57 AM
If both of the residential wifi routers are already connected through ASA and working successfully then I do not believe that you need new connections to the ASA. The existing connections should be sufficient for allowing access between subnets. You have not provided details of how they are currently connected so I am guessing that both are on ASA interfaces with security level of 100. By default the ASA will not allow traffic to flow between interfaces of the same security level. So you will need to specify same security level inter-interface. Once you have done this the subnets should be able to communicate.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 06:33 AM
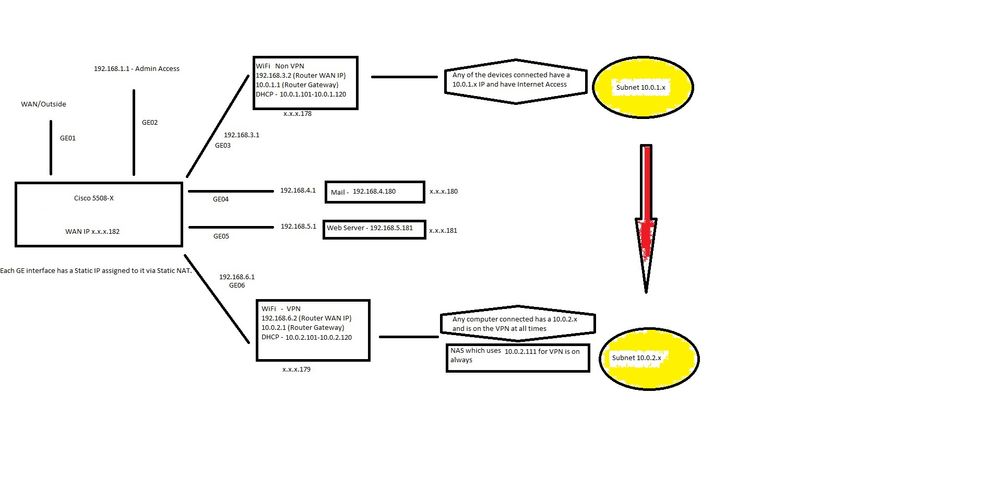
I have added a picture showing my topology. red/yellow are what I wish to achieve.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 08:27 AM
Hello,
so Router 2 is terminating the VPN connections and not the firewall ? It would definitely be helpful to see the configuration of the ASA, as it is unclear how traffic from the VPN clients is blocked from communicating with other subnets directly connected to the ASA...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 08:49 AM - edited 03-15-2019 08:54 AM
I will display my ASA running-config shortly..
Yes, the VPN Router is denying access not the Firewall
As far as the VPN Router, it is a DD-WRT/OpenVPN Client running on my Router 2, D-Link. The VPN is not associated with ASA. The Router connects to Germany or wherever and hides my IP. Based on DD-WRT/OpenVPN once a connection is established nothing can enter through the WAN that not within the tunnel connections. This is why I wanted to link both Routers from the LAN side.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 06:30 AM
The Red/yellow is what I want to achieve.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 06:34 AM - edited 03-15-2019 06:35 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 04:48 AM - edited 03-16-2019 04:50 AM
Hi,
One more question. Is it possible to make changes in configuration on WIFI-VPN and WIFI_NONVPN router?
If yes, then there is a solution:
Option A:
As today, All NATing for your 10.0.1.x and 10.0.2.x NATing is happing by both routers. If possible then remove the NATing from the Both Routers and let's handle by the Cisco ASA. If this condition you can access NAS using the actual IP address.
Following changes required:
Changes on NONVPN router:
Remove NATing
<Need configuration Help, Share your existing configuration>
Changes on the VPN router:
As complete traffic is moving over the VPN then you must bypass 10.0.1.x subnet from the VPN ACL.
Remove NATing
<Need configuration Help, Share your existing configuration>
Changes on ASA router:
As you have allowed the traffic between two different
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
and Add Static routes for both subnets.
Option B:
Changes on the VPN router:
As complete traffic is moving over the VPN then you must bypass 10.0.1.x subnet from the VPN ACL.
Also, you need to allow traffic from WAN to LAN access on the NAS IP address (One to One NATing)
Here WAN IP will be "192.168.6.6 and NAS IP as mentioned "10.0.2.111"
As example: ip nat source static 10.0.2.111 192.168.6.6
<Need configuration Help, Share your existing configuration>
Changes on ASA router:
As you have allowed the traffic between two different
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
Option 3:
Seems not recommended but you can configure GRE tunnel between NON-VPN and VPN router. other changes seem as
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 06:48 AM
Good Morning
as you mentioned option a and b seem to be the better ways. The vpn and nonvpn routers are very generic routers but I believe I can remove NAT. I do not believe they have ACL configurations though.
I think I am just stuck on the concept that the vpn Router, when connected to the vpn (always), removes itself from the local network. As in the 192.168.5.x that it is for its WAN does not take connections anymore. It becomes the random IP address overseas. I’ve contacted the DDWRT community and they said once the VPN tunnel is active there is no connection from WAN to LAN with my ips anymore.
I like where you are going with option B.
This seems to be an excellent idea as long as there is a way to bypass the VPN.
I can give five more details on my TPLink AC3200 (Non VPN) and my DLink AC3200 (Running DDWRT VPN).
My last thought was if using a Cisco SG350 L3 switch I could link the 2 Subnets?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 07:30 AM
Hi,
I never worked on TPlink AC3200 and DLink AC3200
I can give five more details on my TPLink AC3200 (Non VPN) and my DLink AC3200 (Running DDWRT VPN).
Check the configuration if possible.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 07:36 AM
Both the routers I mentioned are residential plug and play routers nowhere near configurable as Cisco.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2019 09:05 AM
ASA Version 9.6(2)2
!
hostname ciscoasa
enable password $sha512$5000$VxGVpbbYO1zrechJNeV1wg==$GTQ23G8/TbyeZGPCsWdOjA== pbkdf2
names
!
interface GigabitEthernet1/1
description WAN
nameif outside
security-level 0
pppoe client vpdn group pppoewan
ip address pppoe setroute
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface GigabitEthernet1/3
description TPLink
nameif tplink
security-level 100
ip address 192.168.2.1 255.255.255.0
!
interface GigabitEthernet1/4
description mail
nameif mail
security-level 100
ip address 192.168.3.1 255.255.255.0
!
interface GigabitEthernet1/5
description fhc
nameif fhc
security-level 100
ip address 192.168.4.1 255.255.255.0
!
interface GigabitEthernet1/6
description vpn
nameif vpn
security-level 100
ip address 192.168.5.1 255.255.255.0
!
interface GigabitEthernet1/7
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet1/8
shutdown
no nameif
no security-level
no ip address
!
interface Management1/1
management-only
no nameif
no security-level
no ip address
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network TPLink
host 192.168.2.177
description TPLink
object network mail
host 192.168.3.180
description mail
object network fhc
host 192.168.4.181
description fhc
object network dlink
host 192.168.5.178
description dlink
object-group network DM_INLINE_NETWORK_1
network-object host 207.108.121.180
network-object object mail
object-group service imapssl tcp
description imapssl
port-object eq 993
object-group network DM_INLINE_NETWORK_4
network-object host 207.108.121.180
network-object object mail
object-group network DM_INLINE_NETWORK_2
network-object host 207.108.121.180
network-object object mail
object-group network DM_INLINE_NETWORK_3
network-object host 207.108.121.180
network-object object mail
object-group network DM_INLINE_NETWORK_5
network-object host 207.108.121.180
network-object object mail
object-group service smtpd tcp
description smtpd
port-object eq 587
access-list outside_access_in extended permit tcp any object-group DM_INLINE_NETWORK_1 eq smtp
access-list outside_access_in extended permit tcp any object-group DM_INLINE_NETWORK_4 object-group imapssl
access-list outside_access_in extended permit tcp any object-group DM_INLINE_NETWORK_3 eq ssh
access-list outside_access_in extended permit tcp any object-group DM_INLINE_NETWORK_5 object-group smtpd inactive
pager lines 24
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu tplink 1500
mtu mail 1500
mtu fhc 1500
mtu vpn 1500
no failover
no monitor-interface service-module
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
arp rate-limit 16384
!
object network TPLink
nat (any,any) static 207.108.121.177
object network mail
nat (any,any) static 207.108.121.180
object network fhc
nat (any,any) static 207.108.121.181
object network dlink
nat (any,any) static 207.108.121.178
access-group outside_access_in in interface outside
route outside 0.0.0.0 0.0.0.0 207.108.121.182 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 sctp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
timeout conn-holddown 0:00:15
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
service sw-reset-button
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpoint _SmartCallHome_ServerCA
no validation-usage
crl configure
crypto ca trustpool policy
crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca 18dad19e267de8bb4a2158cdcc6b3b4a
308204d3 308203bb a0030201 02021018 dad19e26 7de8bb4a 2158cdcc 6b3b4a30
0d06092a 864886f7 0d010105 05003081 ca310b30 09060355 04061302 55533117
30150603 55040a13 0e566572 69536967 6e2c2049 6e632e31 1f301d06 0355040b
13165665 72695369 676e2054 72757374 204e6574 776f726b 313a3038 06035504
0b133128 63292032 30303620 56657269 5369676e 2c20496e 632e202d 20466f72
20617574 686f7269 7a656420 75736520 6f6e6c79 31453043 06035504 03133c56
65726953 69676e20 436c6173 73203320 5075626c 69632050 72696d61 72792043
65727469 66696361 74696f6e 20417574 686f7269 7479202d 20473530 1e170d30
36313130 38303030 3030305a 170d3336 30373136 32333539 35395a30 81ca310b
30090603 55040613 02555331 17301506 0355040a 130e5665 72695369 676e2c20
496e632e 311f301d 06035504 0b131656 65726953 69676e20 54727573 74204e65
74776f72 6b313a30 38060355 040b1331 28632920 32303036 20566572 69536967
6e2c2049 6e632e20 2d20466f 72206175 74686f72 697a6564 20757365 206f6e6c
79314530 43060355 0403133c 56657269 5369676e 20436c61 73732033 20507562
6c696320 5072696d 61727920 43657274 69666963 6174696f 6e204175 74686f72
69747920 2d204735 30820122 300d0609 2a864886 f70d0101 01050003 82010f00
3082010a 02820101 00af2408 08297a35 9e600caa e74b3b4e dc7cbc3c 451cbb2b
e0fe2902 f95708a3 64851527 f5f1adc8 31895d22 e82aaaa6 42b38ff8 b955b7b1
b74bb3fe 8f7e0757 ecef43db 66621561 cf600da4 d8def8e0 c362083d 5413eb49
ca595485 26e52b8f 1b9febf5 a191c233 49d84363 6a524bd2 8fe87051 4dd18969
7bc770f6 b3dc1274 db7b5d4b 56d396bf 1577a1b0 f4a225f2 af1c9267 18e5f406
04ef90b9 e400e4dd 3ab519ff 02baf43c eee08beb 378becf4 d7acf2f6 f03dafdd
75913319 1d1c40cb 74241921 93d914fe ac2a52c7 8fd50449 e48d6347 883c6983
cbfe47bd 2b7e4fc5 95ae0e9d d4d143c0 6773e314 087ee53f 9f73b833 0acf5d3f
3487968a ee53e825 15020301 0001a381 b23081af 300f0603 551d1301 01ff0405
30030101 ff300e06 03551d0f 0101ff04 04030201 06306d06 082b0601 05050701
0c046130 5fa15da0 5b305930 57305516 09696d61 67652f67 69663021 301f3007
06052b0e 03021a04 148fe5d3 1a86ac8d 8e6bc3cf 806ad448 182c7b19 2e302516
23687474 703a2f2f 6c6f676f 2e766572 69736967 6e2e636f 6d2f7673 6c6f676f
2e676966 301d0603 551d0e04 1604147f d365a7c2 ddecbbf0 3009f343 39fa02af
33313330 0d06092a 864886f7 0d010105 05000382 01010093 244a305f 62cfd81a
982f3dea dc992dbd 77f6a579 2238ecc4 a7a07812 ad620e45 7064c5e7 97662d98
097e5faf d6cc2865 f201aa08 1a47def9 f97c925a 0869200d d93e6d6e 3c0d6ed8
e6069140 18b9f8c1 eddfdb41 aae09620 c9cd6415 3881c994 eea28429 0b136f8e
db0cdd25 02dba48b 1944d241 7a05694a 584f60ca 7e826a0b 02aa2517 39b5db7f
e784652a 958abd86 de5e8116 832d10cc defda882 2a6d281f 0d0bc4e5 e71a2619
e1f4116f 10b595fc e7420532 dbce9d51 5e28b69e 85d35bef a57d4540 728eb70e
6b0e06fb 33354871 b89d278b c4655f0d 86769c44 7af6955c f65d3208 33a454b6
183f685c f2424a85 3854835f d1e82cf2 ac11d6a8 ed636a
quit
telnet timeout 5
ssh stricthostkeycheck
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
vpdn group pppoewan request dialout pppoe
vpdn group pppoewan localname *****
vpdn group pppoewan ppp authentication chap
vpdn username ***** password *****
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
dynamic-access-policy-record DfltAccessPolicy
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
no tcp-inspection
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:101b9678ff0b5678925645e7d012a4f7
: end
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 08:16 AM
In regards to a backup plan, if I am unable to configure either of my Routers in a manner that allows my access, which I feel the VPN is going to be the problem, and being that it seems the Cisco will not work in this manner, will using a L3 Switch w/ no WAN access work to connect the separate Subnets? I just see it as being something to be able to do. Assigning Interface 1 an IP from one subnet and assigning Interface 2 an IP from the other subnet and then through the Switch just creating a NAT rule or even just an ip route from 1 Interface to another. With that said I just assumed the 5508 would work the same as each Interface is an independent one. Assign Interface 1/7 and 1/8 to each router independent of the 5508 to just talk to each other.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2019 02:39 PM
Thank you for posting the configuration of the ASA. I have not yet looked at it in detail and before we spend much time on that config there are some basic questions that we need to address. If I am understanding the diagram correctly each LAN is connected to a small router, receives their IP addresses from that router, and use that router as their default gateway. If that is true then the routing logic on each of the small routers is key to our discussion. If you are able to make an alternate connection on the small router, are you able to change the routing logic so that traffic for the desired LAN subnet is sent out an interface different from the interface used for the default route?
HTH
Rick
Rick
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide