- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ACL blocks telnet, but it shouldn't, please help!
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 04:27 PM - edited 03-04-2019 06:54 PM
Hi all,
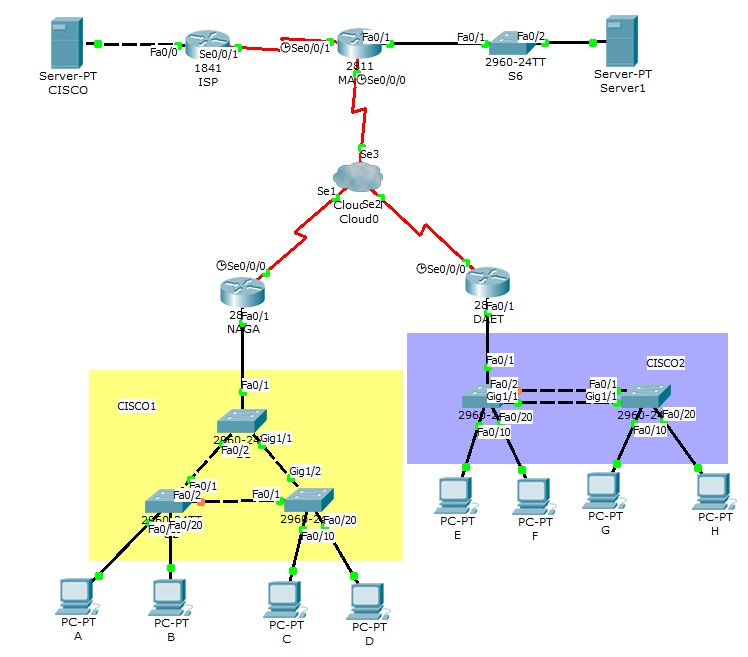
I have problem with ACL, acl 110 blocks telnet to cisco1 vtp domain to cisco2 and vice versa, however i can telnet to the touter on the top.
And i have an other problem too.. I've tried ospf, eigrp, ripv2. Those didn't work properly the routers didn't learn the full routing table.
Of course split horizont is off. Static route worked fine...
I't a point to point frame relay, R1 is the hub, the 2 routers below are the spokes.
.
I've attached the packet tracer file, if you want to take a look
interface Serial0/0/0.1 point-to-point
ip address 192.168.1.254 255.255.255.0
no ip split-horizon
frame-relay interface-dlci 102
ip access-group 110 in
ip nat inside
clock rate 2000000
interface Serial0/0/0.2 point-to-point
ip address 192.168.2.190 255.255.255.192
no ip split-horizon
frame-relay interface-dlci 103
ip access-group 110 in
ip nat inside
clock rate 2000000
access-list 110 permit tcp any any eq 443
access-list 110 permit tcp any any eq www
access-list 110 permit tcp 172.16.20.0 0.0.0.127 host 10.10.10.254 eq ftp
access-list 110 permit tcp any any eq domain
access-list 110 permit udp any any eq domain
access-list 110 permit tcp any any eq telnet
Any help is welcome.
Thanks in advance!
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 05:44 AM
Hi,
> I have problem with ACL, acl 110 blocks telnet to cisco1 vtp domain to cisco2 and vice versa, however i can telnet to the touter on the top.
Because packets goes to the router which you do telnet but cannot go back. So to make it work you need to add additional rule to permit return traffic from remote router.
access-list 110 permit tcp any any eq telnet
access-list 110 permit tcp any eq telnet any
> And i have an other problem too.. I've tried ospf, eigrp, ripv2. Those didn't work properly the routers didn't learn the full routing table.
Problem also in ACL #110. You need to permit dynamic routing protocol traffic (OSPF, EIGRP).
access-list 110 permit eigrp any any
Additional you could permit traffic ICMP traffic for diagnostic purpose.
access-list 110 permit icmp any any
Any access-list in Cisco IOS has at the end of ACL has deny any any default rule.
And above link I posted explains this. I just wanted you to find out it by yourself.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 06:13 AM
No, actually it permits telnet traffic that goes to the remote router only. It means from any source to any destination device that runs Telnet service. And it's applied inbound direction it means packets go through ACL that entering to interface.
Telnet service on the router will be source of packets that responds to destination router.
And when device responds to that source(that requested connection) it's packets get blocked(deny any any, at the end of ACL) because there is no match in ACL.
So permit tcp any eq telnet any permits those traffic from remote router.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-01-2013 09:05 PM
Hi,
Have a look on these links try to understand ACL in Cisco IOS then you will solve your problem
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 05:28 AM
thanks i'll ready them!
but the question is still open
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 05:44 AM
Hi,
> I have problem with ACL, acl 110 blocks telnet to cisco1 vtp domain to cisco2 and vice versa, however i can telnet to the touter on the top.
Because packets goes to the router which you do telnet but cannot go back. So to make it work you need to add additional rule to permit return traffic from remote router.
access-list 110 permit tcp any any eq telnet
access-list 110 permit tcp any eq telnet any
> And i have an other problem too.. I've tried ospf, eigrp, ripv2. Those didn't work properly the routers didn't learn the full routing table.
Problem also in ACL #110. You need to permit dynamic routing protocol traffic (OSPF, EIGRP).
access-list 110 permit eigrp any any
Additional you could permit traffic ICMP traffic for diagnostic purpose.
access-list 110 permit icmp any any
Any access-list in Cisco IOS has at the end of ACL has deny any any default rule.
And above link I posted explains this. I just wanted you to find out it by yourself.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 06:22 AM
thanks it worked fine!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 05:57 AM
oh thanks, i alwas have problem with traffic which is coming back <3 bro!
abut the routing problem, i had problem with it before i set the acl up
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 06:13 AM
No, actually it permits telnet traffic that goes to the remote router only. It means from any source to any destination device that runs Telnet service. And it's applied inbound direction it means packets go through ACL that entering to interface.
Telnet service on the router will be source of packets that responds to destination router.
And when device responds to that source(that requested connection) it's packets get blocked(deny any any, at the end of ACL) because there is no match in ACL.
So permit tcp any eq telnet any permits those traffic from remote router.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 06:24 AM
one more question sir!
the acl under is filtering inbound traffic from the internet
if i use those commands hosts from the internet can access ftp,hhtp,https services on my whole inside network
but if i change the highlighted "any" to host 10.10.10.254 which is my inside server, the hosts from the internet cannot access my inside server anymore
access-list 150 permit tcp any any established
access-list 150 permit tcp any any eq ftp
access-list 150 permit tcp any any eq www
access-list 150 permit tcp any any eq 443
anyway there is an inside outside nat rule+port forwarding
global adress is 198.0.18.9 local is 10.10.10.254
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 06:45 AM
If ACL #150 is applied on Internet facing interface you need to use public IP instead of private.
Note. For security reason I would not recommend to use any statement in ACL that applied on outside interface and also would not recommend to post here real public IP for the same reason.
Hope it will help.
Best regards,
Abzal
Abzal
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-02-2013 06:59 AM
it is a packe tracer lab, so dont worry m8
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

