- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ACL not working with NAT
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-05-2021 03:54 PM
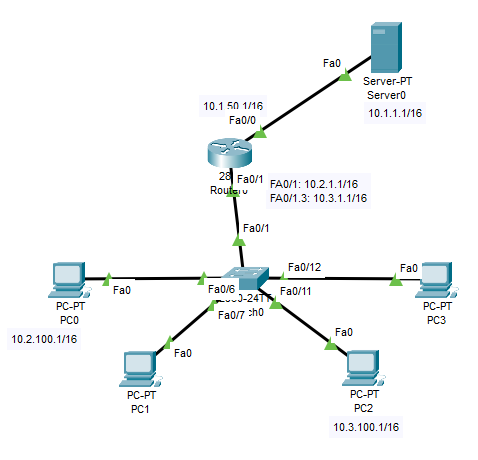
I'm studying on Cisco packet tracking, I just found one strange thing. I attached the network map and configuration below.
1> I created NAT for 10.2.0.0/16 and 10.3.0.0/16 to access the server0.
2> Created ACL for 10.2.100.0 0.0.0.255 to not allow access server www
Created ACL for 10.3.100.0 0.0.0.255 to not allow access server ftp
Now the problem comes, the PC0 still can access the server www, same as PC2 can access FTP.
But if I deleve the nat command line, the ACL works.
I'm confused, the ACL should always work before NAT, it looks like the NAT bypassed the ACL with its outbound IP address without filtered. how does this happen???
! interface FastEthernet0/0 ip address 10.1.50.1 255.255.0.0 ip access-group 110 out ip nat outside duplex auto speed auto ! interface FastEthernet0/1 ip address 10.2.1.1 255.255.0.0 ip nat inside duplex auto speed auto ! interface FastEthernet0/1.3 encapsulation dot1Q 3 ip address 10.3.1.1 255.255.0.0 ip nat inside ! interface Vlan1 no ip address shutdown ! ip nat pool internet 10.1.50.50 10.1.50.50 netmask 255.255.0.0 ip nat inside source list 2 pool internet overload ip classless ! ip flow-export version 9 ! ! access-list 2 permit 10.2.0.0 0.0.255.255 access-list 2 permit 10.3.0.0 0.0.255.255 access-list 110 deny tcp 10.2.100.0 0.0.0.255 host 10.1.1.1 eq www access-list 110 deny tcp 10.3.100.0 0.0.0.255 host 10.1.1.1 eq ftp access-list 110 permit ip any any ! ! !
Solved! Go to Solution.
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-06-2021 02:07 AM - edited 01-06-2021 02:09 AM
Hello
Apologes @Jonasye
I didn’t read your post correctly as such didn’t see the acl 110 applied to the nat rtrs outside interface .
Anyway you just need to simply amend the nat access-list 2 to negate nat for those host so then the access-list 110 will be read,.
This is due to the nat order of operation for domain nat which will read the nat acl before any routing is perfromed or any outbound acl is read - here
example:
no access-list 2
access-list 2 deny host 10.2.100.1
access-list 2 deny host 10.3.100.1
access-list 2 permit 10.2.0.0 0.0.255.255
access-list 2 permit 10.3.0.0 0.0.255.255
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide