- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA 5520 to 5505 ipsec tunnel help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 12:56 PM
How to configure a ipsec tunnel between a Cisco ASA 5520 and a Cisco ASA 5505?
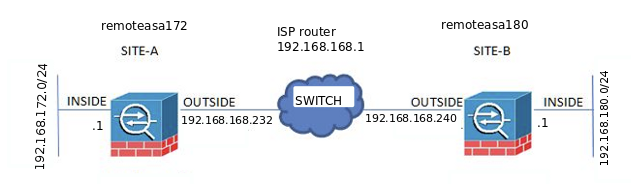
============================---------------------------remoteasa172-------------------------------=================================
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
: ASA Version 9.1(7)32
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 182.168.172.0 255.255.255.0 192.168.180.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
!
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.180.0 255.255.255.0 192.168.168.240 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto map CMAP 80 match address LAN_Traffic
crypto map CMAP 80 set peer 192.168.168.240
crypto map CMAP 80 set ikev1 transform-set TS
crypto map enable interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
dhcpd dns 192.168.168.1
dhcpd lease 3000
dhcpd ping_timeout 20
dhcpd domain mydomain.com
dhcpd option 3 ip 192.168.172.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.172.3-192.168.172.63 inside
dhcpd enable inside
!
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa172#
============================---------------------------remoteasa180-------------------------------=================================
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
: ASA Version 9.2(4)5
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 192.168.180.0 255.255.255.0 192.168.172.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
!
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.172.0 255.255.255.0 192.168.168.232 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
dhcpd dns 192.168.168.1
dhcpd ping_timeout 20
dhcpd domain myudomain.com
dhcpd auto_config outside
dhcpd option 3 ip 192.168.180.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.180.3-192.168.180.63 inside
dhcpd enable inside
!
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa180#
Solved! Go to Solution.
- Labels:
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 10:54 AM
Can 192.168.171.3 ping 192.168.172.3?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:08 AM
Good question!!! Why didn't I think of that. I'm so used to RTRs. ASAs are a lot more protective.
I can ping one way. Must me some reminant on the asa172 asa.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:11 AM
Latest
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233# sh run
: Saved
:
: Serial Number: JMX1510L0T6
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
:
ASA Version 9.1(7)23
!
hostname asa171-233
domain-name mydomain.com
enable password N7HlIItY8AVJppkQ encrypted
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.233 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.171.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
nameif mngt
security-level 0
ip address 10.10.10.13 255.255.255.224
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name mydomain.com
object network 192.168.172.0_24
subnet 192.168.172.0 255.255.255.0
object network 192.168.171.0_24
subnet 192.168.171.0 255.255.255.0
access-list OUTSIDE-IN extended permit ip any any
access-list OUTSIDE-IN extended permit icmp any any
access-list OUTSIDE-IN extended permit tcp any any
access-list OUTSIDE-IN extended permit tcp any any eq www log errors
access-list OUTSIDE-OUT extended permit ip any any
access-list OUTSIDE-OUT extended permit icmp any any
access-list OUTSIDE-OUT extended permit tcp any any
access-list INSIDE-IN extended permit ip any any
access-list INSIDE-IN extended permit icmp any any
access-list INSIDE-IN extended permit tcp any any
access-list INSIDE-OUT extended permit ip any any
access-list INSIDE-OUT extended permit icmp any any
access-list INSIDE-OUT extended permit tcp any any
access-list LAN_Traffic_172_232 extended permit ip object 192.168.171.0_24 object 192.168.172.0_24
pager lines 24
logging enable
logging monitor debugging
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu mngt 1500
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
icmp permit any echo inside
icmp permit any echo-reply inside
icmp permit any mngt
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 5
route outside 192.168.172.0 255.255.255.0 192.168.168.232 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic_172_232
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.168.0 255.255.255.0 outside
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 73ozQQQ.JMBHDyQz encrypted
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
inspect icmp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:d26c4daeb450d9865dee29e4db7f9795
: end
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa171-233#
asa172-232#
asa172-232#
asa172-232#
asa172-232#
asa172-232#
asa172-232#
asa172-232# sh run
: Saved
:
: Serial Number: JMX1519L0A3
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
:
ASA Version 9.1(7)32
!
hostname asa172-232
domain-name mydomain.com
enable password N7HlIItY8AVJppkQ encrypted
names
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
nameif mngt
security-level 0
ip address 10.10.10.12 255.255.255.224
!
interface Management0/0
management-only
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
!
ftp mode passive
dns server-group DefaultDNS
domain-name mydomain.com
object network 192.168.172.0_24
subnet 192.168.172.0 255.255.255.0
object network 192.168.180.0_24
subnet 192.168.180.0 255.255.255.0
object network 192.168.171.0_24
subnet 192.168.171.0 255.255.255.0
access-list LAN_Traffic extended permit ip object 192.168.172.0_24 object 192.168.180.0_24
access-list LAN_Traffic_171_233 extended permit ip object 192.168.172.0_24 object 192.168.171.0_24
access-list OUTSIDE-IN extended permit ip any any
access-list OUTSIDE-IN extended permit icmp any any
access-list OUTSIDE-IN extended permit tcp any any
access-list OUTSIDE-OUT extended permit ip any any
access-list OUTSIDE-OUT extended permit icmp any any
access-list OUTSIDE-OUT extended permit tcp any any
access-list INSIDE-IN extended permit ip any any
access-list INSIDE-IN extended permit icmp any any
access-list INSIDE-IN extended permit tcp any any
access-list INSIDE-OUT extended permit ip any any
access-list INSIDE-OUT extended permit icmp any any
access-list INSIDE-OUT extended permit tcp any any
pager lines 24
logging enable
logging timestamp
logging monitor debugging
logging buffered informational
logging asdm informational
mtu outside 1500
mtu inside 1500
mtu mngt 1500
mtu management 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
icmp permit any echo inside
icmp permit any echo-reply inside
icmp permit any mngt
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
route outside 0.0.0.0 0.0.0.0 192.168.168.1 5
route outside 192.168.171.0 255.255.255.0 192.168.168.233 1
route outside 192.168.180.0 255.255.255.0 192.168.168.240 1
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
no snmp-server location
no snmp-server contact
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 71 match address LAN_Traffic_171_233
crypto map CMAP 71 set pfs
crypto map CMAP 71 set peer 192.168.168.233
crypto map CMAP 71 set ikev1 transform-set TS
crypto map CMAP 80 match address LAN_Traffic
crypto map CMAP 80 set pfs
crypto map CMAP 80 set peer 192.168.168.240
crypto map CMAP 80 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh stricthostkeycheck
ssh 192.168.168.0 255.255.255.0 outside
ssh timeout 5
ssh key-exchange group dh-group14-sha1
console timeout 0
dhcpd lease 3000
!
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username cisco password 73ozQQQ.JMBHDyQz encrypted
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
ikev1 pre-shared-key *****
tunnel-group 192.168.168.233 type ipsec-l2l
tunnel-group 192.168.168.233 ipsec-attributes
ikev1 pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:e7eb2e45adea7e68d5b7781a7e59edc5
: end
asa172-232#
asa172-232#
asa172-232#
asa172-232#
asa172-232#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:14 AM
Strange that the ASA can't ping the switch at .2 but can ping the laptop? This must be an ASA thing.
asa172-232# ping 192.168.171.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.171.2, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
asa172-232# ping 192.168.171.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.171.3, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
asa172-232#
asa171-233#
asa171-233# ping 192.168.172.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.172.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/10 ms
asa171-233# ping 192.168.172.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.172.2, timeout is 2 seconds:
?????
Success rate is 0 percent (0/5)
asa171-233#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:24 AM
Perhaps ASA not able to ping switch might be an ASA thing. But it might also be a switch thing. I don't remember (not sure it was mentioned, and if it was I don't remember) whether switches are layer 2 or layer 3? If they are layer 2 where is their default gateway? In either case I wonder if the issue might be related to whether the switch has a route for the remote network (where the ping originates)? Could it be that the switch is not able to send its ping response?
Have you checked the possibility of a firewall on one of the PC denying ping?
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:14 AM
Before we look for more issues on the ASA can you verify whether that PC might have a firewall that is denying the ping?
If the ipsec sa is showing two way traffic I am pretty confident that the issue is not the vpn.
I believe that one thing that was impacting your testing was trying to ping the ASA inside interface from the remote peer. The ASA as a security feature does not allow that kind of access. Here is a link that has some discussion about that. I hope you find it helpful.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:33 AM
I switched the network top the PC that is pinging and you are right. It's the PC even though the FW is disabled.
So my tunnel is up and pinging. HURRAY You have done the impossible. I'll play around putting the NAT and PAT back in.... At least a normal access to internet NAT should work.... I was hoping that the ASA would support the PAT and the 2921 wouldn't do. I'll give it a try and let you know.
Rick thank you for your help. I should get a couple of trusted laptops and never do a windows update on them :-)
Your the best. I'll close this ticket and try to find where I can rate your help with 5 stars :-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:43 AM
Glad that we got it to work. There have been a couple of issues we had to deal with. The address translation was the most tricky to identify and resolve. There is a question that you need to consider about whether you need address translation on the ASA. I thought it was a bit odd that address translation was on one ASA and not the others. Perhaps there is a reason for that. The main thing to bear in mind is that if any of the ASAs do a translation where the inside subnet is getting translated (typically using the outside interface address) that you will need the static translation for the local_subnet local_subnet remote_subnet remote_subnet to prevent the vpn traffic from being translated.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 01:14 PM
Thanks for the tip Rick. The requirement is that the remote consultant sites have a static ISP address. Then we connect using our own device for an L3 tunnel (due to DISA STIG requirements). But they also need to get out to the internet from their own ISP. So I've got to get an L3 tunnel (from HQ to them) and provide NAT overload working for their internet access.
Before my company got remote sites in using port mapping from our external IP to internal servers. Not a good solution, but something I wanted to continue to support until everyone is on an L3. It was decided not to use login VPNs...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2019 01:06 PM
The NAT that Amikat sent is only needed on the ASA that is doing a NAT to the internet (in my case it's the remote client asa171-233). Otherwise, no NAT is needed. I also had to exclude the tunnel LAN address on the inside IN ACL on the NAT overload ASA. See the attached configs.
Even though the 5520 to 5520 is solid, I can't get the 5505 to work...
-------------------------===================asa171-233================-----------------------
I have a standing ping running and here are the configurations and these are working: If I remove the NAT from Amikat the ping from 172 to 171 stops but 171 to 172 continues!!!!!
asa171-233(config)# sh run | i nat
nat (inside,outside) source static 192.168.171.0_24 192.168.171.0_24 destination static 192.168.172.0_24 192.168.172.0_24 no-proxy-arp route-lookup
nat (inside,outside) after-auto source dynamic any interface
asa171-233(config)# sh run | i route
192.168.172.0_24 no-proxy-arp route-lookup
route outside 0.0.0.0 0.0.0.0 192.168.168.1 5
route outside 192.168.172.0 255.255.255.0 192.168.168.232 1
asa171-233(config)#
access-list INSIDE-IN line 1 extended deny ip 192.168.171.0 255.255.255.0 192.168.172.0 255.255.255.5 (hitcnt=0) 0xf4c50d59
access-list INSIDE-IN line 2 extended permit ip any any (hitcnt=5313) 0xece2599d
access-list INSIDE-IN line 3 extended permit icmp any any (hitcnt=0) 0x5cfc8e4a
access-list INSIDE-IN line 4 extended permit tcp any any (hitcnt=0) 0x8be220e6
---------------==================asa172-232# ================----------------------
asa172-232# sh run | i nat
asa172-232# sh run | i route
route outside 192.168.171.0 255.255.255.0 192.168.168.233 1
route outside 192.168.180.0 255.255.255.0 192.168.168.240 1
asa172-232#
access-list INSIDE-IN line 1 extended permit ip any any (hitcnt=38237) 0xece2599d
access-list INSIDE-IN line 2 extended permit icmp any any (hitcnt=0) 0x5cfc8e4a
access-list INSIDE-IN line 3 extended permit tcp any any (hitcnt=0) 0x8be220e6
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2019 02:39 PM
Hi,
Will you please change the static route configuration at "asa180-240":
route inside 192.168.172.0 255.255.255.0 192.168.168.232 1
to
route outside 192.168.172.0 255.255.255.0 192.168.168.232 1
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-26-2019 03:25 PM
Antonin
Good catch. +5
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 05:02 AM
Holy S, that does it how stupid can I be. The 5505 is now working. THANK YOU EVERYONE.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 06:24 AM
Easy mistake to make. Glad to know that it is working now.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 07:28 AM
Thought that I would send you off the final version of the configuration. The tunnel is up and the overlaod NAT to the internet is working. YES thank you!!!
I've some other duties to do right now but I'd like to put in the PAT into the 5520 to find out if the PAT interfered with the L3 like it did on the 2921.
ip nat static tcp 192.168.180.66 80 192.168.168.235 8080 extendable
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide