- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA 5520 to 5505 ipsec tunnel help
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-21-2019 12:56 PM
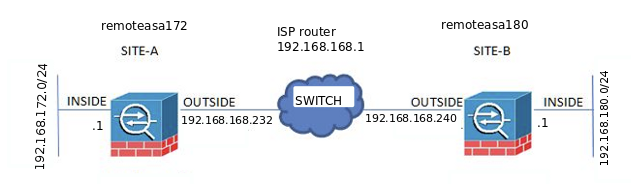
How to configure a ipsec tunnel between a Cisco ASA 5520 and a Cisco ASA 5505?
============================---------------------------remoteasa172-------------------------------=================================
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
remoteasa172#
: Hardware: ASA5520, 2048 MB RAM, CPU Pentium 4 Celeron 2000 MHz
: ASA Version 9.1(7)32
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address 192.168.168.232 255.255.255.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.172.1 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 182.168.172.0 255.255.255.0 192.168.180.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
!
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.180.0 255.255.255.0 192.168.168.240 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto map CMAP 80 match address LAN_Traffic
crypto map CMAP 80 set peer 192.168.168.240
crypto map CMAP 80 set ikev1 transform-set TS
crypto map enable interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
!
dhcpd dns 192.168.168.1
dhcpd lease 3000
dhcpd ping_timeout 20
dhcpd domain mydomain.com
dhcpd option 3 ip 192.168.172.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.172.3-192.168.172.63 inside
dhcpd enable inside
!
tunnel-group 192.168.168.240 type ipsec-l2l
tunnel-group 192.168.168.240 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa172#
============================---------------------------remoteasa180-------------------------------=================================
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
remoteasa180#
: Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz
: ASA Version 9.2(4)5
!
interface Ethernet0/0
description OUTSIDE_200
switchport access vlan 200
!
interface Ethernet0/1
description INSIDE_180
switchport access vlan 180
!
interface Vlan180
nameif inside
security-level 100
ip address 192.168.180.1 255.255.255.0
!
interface Vlan200
description OUTSIDE_200
nameif outside
security-level 0
ip address 192.168.168.240 255.255.255.0
!
access-list OUTSIDE-IN extended permit ip any any log
access-list OUTSIDE-IN extended permit icmp any any log
access-list OUTSIDE-IN extended permit tcp any any log
access-list OUTSIDE-OUT extended permit ip any any log
access-list OUTSIDE-OUT extended permit icmp any any log
access-list OUTSIDE-OUT extended permit tcp any any log
access-list INSIDE-IN extended permit ip any any log
access-list INSIDE-IN extended permit icmp any any log
access-list INSIDE-IN extended permit tcp any any log
access-list INSIDE-OUT extended permit ip any any log
access-list INSIDE-OUT extended permit icmp any any log
access-list INSIDE-OUT extended permit tcp any any log
!
access-list LAN_Traffic extended permit ip 192.168.180.0 255.255.255.0 192.168.172.0 255.255.255.0 log
!
nat (inside,outside) after-auto source dynamic any interface
access-group INSIDE-IN in interface inside
access-group INSIDE-OUT out interface inside
access-group OUTSIDE-IN in interface outside
access-group OUTSIDE-OUT out interface outside
!
route outside 0.0.0.0 0.0.0.0 192.168.168.1 1
route inside 192.168.172.0 255.255.255.0 192.168.168.232 1
!
crypto ipsec ikev1 transform-set TS esp-aes-256 esp-sha-hmac
crypto ipsec security-association pmtu-aging infinite
crypto map CMAP 72 match address LAN_Traffic
crypto map CMAP 72 set pfs
crypto map CMAP 72 set peer 192.168.168.232
crypto map CMAP 72 set ikev1 transform-set TS
crypto map CMAP interface outside
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
dhcpd dns 192.168.168.1
dhcpd ping_timeout 20
dhcpd domain myudomain.com
dhcpd auto_config outside
dhcpd option 3 ip 192.168.180.1
dhcpd option 2 ascii dhcpd_option_2_ascii_examplestring_HERE
!
dhcpd address 192.168.180.3-192.168.180.63 inside
dhcpd enable inside
!
tunnel-group 192.168.168.232 type ipsec-l2l
tunnel-group 192.168.168.232 ipsec-attributes
ikev1 pre-shared-key *****
!
remoteasa180#
Solved! Go to Solution.
- Labels:
-
Other Routing
-
WAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 07:42 AM
Thanks for sharing the current config. Glad that it is working. I am a bit surprised to see the inside in acl begin with a statement which denies traffic from the local subnet to the remote peer subnet.
I would think that the PAT should not cause a problem on the 5520. But since I am not clear why it was a problem on the router there may be some aspect that I am not considering which could also impact the 5520.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 01:20 PM - edited 02-28-2019 10:46 AM
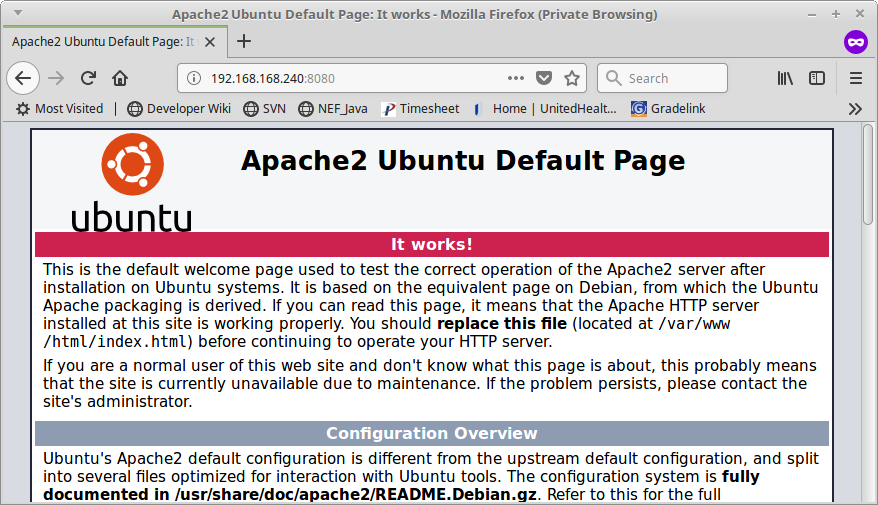
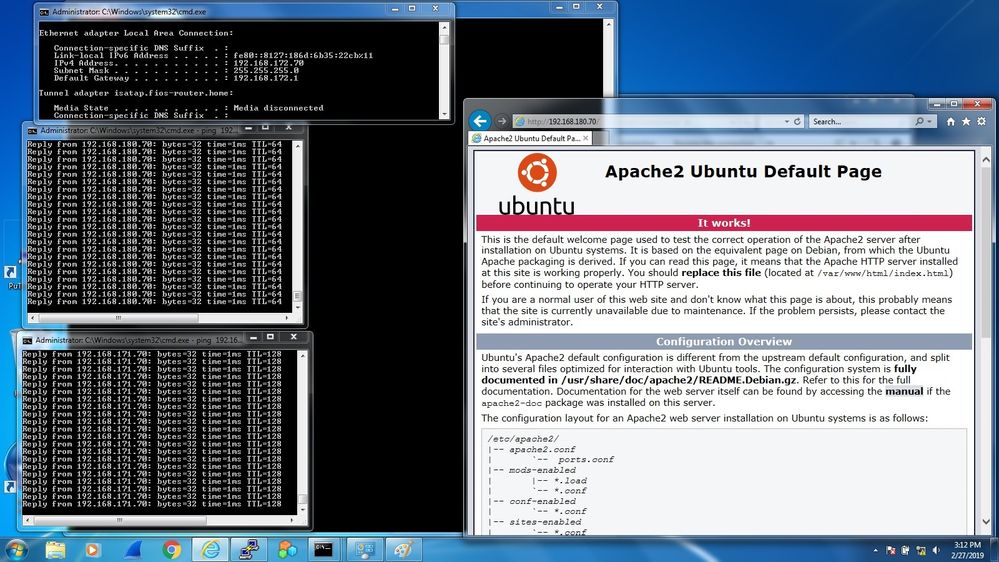
Tested the NAT overload, L3 tunnel, and PAT to www on the 5505 and it all works (see the following screen shots). HURRAY. I've added the final-final configuration attached (Apache2_PAT_5505.txt). Any idea why the 2921 RTR wouldn't do this (PATandL3conflict_2921.txt)? The PAT worked accessing www from outside, but it would block accessing the www server through the tunnel - it would not do what is shown in the second screen shot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-27-2019 02:21 PM
I am not real clear what I am looking at in these configs. But as far as I tell the configs that I believe are indicated as good both include the command
nat (inside, outside) after-auto source dynamic any interface
and the configs that seem to be labeled as bad did not have this command.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-28-2019 10:49 AM
Sorry Rick, I attached the wrong files. I've corrected the posting. It has the good 5505 ASA configuration with overload NAT, PAT to www, and L3 tunnel (as shown in the screen shots). The other is for the 2921 that does the same thing but will not let the tunnel access the www server because of the Port Mapping to it from the outside.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-01-2019 02:12 PM
Hi,
Will you please modify your router static NAT & add couple of lines as per beneath (this should be applicable to access the 192.168.175.66 host from 192.168.176.0/24 subnet via VPN tunnel):
ip nat source static tcp 192.168.175.66 80 192.168.168.235 8080 route-map nonat
access-list 176 deny ip host 192.168.175.66 192.168.176.0 0.0.0.255
access-list 176 permit ip host 192.168.175.66 any
route-map nonat permit 10
match ip address 176
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 06:03 AM
Hi Rick, I'll do that but I have to start up my router workbench. Thanks for the recommendation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-07-2019 11:18 AM
Hi Amikat, I'll get to that NAT on the 2921 as soon as I can. Thank you for your help :-)
I just found out something interesting (but it may be solved with your recommended NAT on the 2921). I'm connecting the remote sites to an alternate ISP so the address for the gateway ASA/RTR on our ops network is not 192.168.168.1 (it's already used) but instead an available address like 192.168.168.233; so I have to put in a ip route on the servers to get back to the remote site gateway router.
When I did this with the 2921, the L2 tunnel source address within the ops network was the ISP static ip network. Like 72.163.4.0/29 - not our real address). But the ASA is showing up as the actual private address from the remote end (host 192.168.180.4 for example).... It makes it much easier to put in routes on the servers.
ASA -------------------------------PING
[root@snips ahuffman]# tcpdump -n -i em1 | grep ICMP
19:10:32.407631 IP 192.168.180.4 > 192.168.168.200: ICMP echo request, id 12268, seq 751, length 64
19:10:32.407656 IP 192.168.168.200 > 192.168.180.4: ICMP echo reply, id 12268, seq 751, length 64
19:10:33.431642 IP 192.168.180.4 > 192.168.168.200: ICMP echo request, id 12268, seq 752, length 64
19:10:33.431658 IP 192.168.168.200 > 192.168.180.4: ICMP echo reply, id 12268, seq 752, length 64
19:10:34.455633 IP 192.168.180.4 > 192.168.168.200: ICMP echo request, id 12268, seq 753, length 64
19:10:34.455649 IP 192.168.168.200 > 192.168.180.4: ICMP echo reply, id 12268, seq 753, length 64
19:10:35.479617 IP 192.168.180.4 > 192.168.168.200: ICMP echo request, id 12268, seq 754, length 64
19:10:35.479634 IP 192.168.168.200 > 192.168.180.4: ICMP echo reply, id 12268, seq 754, length 64
^C283 packets captured
RTR------------------SEE 72.163.4.0 -----------------------IP ROUTE
-----------this is what I had to do to get the 2921 to work------------------
[root@snips ahuffman]# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
0.0.0.0 192.168.168.1 0.0.0.0 UG 0 0 0 em1
10.10.10.0 0.0.0.0 255.255.255.224 U 0 0 0 em2
72.163.4.0 192.168.168.233 255.255.255.248 UG 0 0 0 em1
192.168.168.0 0.0.0.0 255.255.255.0 U 0 0 0 em1
192.168.168.0 0.0.0.0 255.255.255.0 U 0 0 0 em1
192.168.174.0 192.168.168.238 255.255.255.0 UG 0 0 0 em1
[root@snips ahuffman]#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 08:59 AM
Hi Amikat, on a Cisco 2921 - I tried to add a static NAT & route-map (this is applied access the 192.168.175.4 host from 192.168.177.0/24 subnet via VPN tunnel) as follows. But the 2921 c2900-universalk9-mz.SPA.157-3.M2.bin will not accept the command at the "route-map".
ip nat source static tcp 192.168.175.4 80 192.168.168.235 8888 route-map NONAT
access-list 177 deny ip host 192.168.175.4 192.168.177.0 0.0.0.255
access-list 177 permit ip host 192.168.175.4 any
route-map NONAT permit 10
match ip address 177
ip nat source static tcp 192.168.175.4 80 192.168.168.235 8888 route-map NONAT
^
% Invalid input detected at '^' marker.
remotertr175(config)#ip nat source static tcp 192.168.175.4 80 192.168.168.235 8888 ?
extendable Extend this translation when used
no-alias Do not create an alias for the global address
no-payload No translation of embedded address/port in the payload
vrf Specify vrf
<cr>
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#sh run
Building configuration...
Current configuration : 6304 bytes
!
! Last configuration change at 15:06:19 UTC Fri Mar 22 2019
! NVRAM config last updated at 14:48:18 UTC Fri Mar 22 2019
!
version 15.7
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname remotertr175
!
boot-start-marker
boot system flash:c2900-universalk9-mz.SPA.157-3.M2.bin
boot system flash:c2900-universalk9-mz.SPA.154-3.M1.bin
boot system flash:c2900-universalk9-mz.SPA.152-1.T3.bin
boot-end-marker
!
!
enable secret 5 $1$A3Kg$TZeqZI6QF3r.S4nu80fZJ1
!
no aaa new-model
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
no ip dhcp conflict logging
ip dhcp excluded-address 192.168.175.1 192.168.175.2
ip dhcp excluded-address 192.168.175.64 192.168.175.255
!
ip dhcp pool DHCPPOOL
network 192.168.175.0 255.255.255.0
dns-server 192.168.168.200 192.168.168.1
default-router 192.168.175.1
lease 0 2
!
!
!
no ip domain lookup
ip domain name mydomain.com
ip cef
l2tp-class TOM_2_REMOTERTR2_PW
digest secret 7 09414405170003 hash SHA1
!
no ipv6 cef
!
multilink bundle-name authenticated
!
!
!
!
!
!
!
!
voice-card 0
!
!
!
!
!
!
!
!
vxml logging-tag
license udi pid CISCO2921/K9 sn FTX1714AKGS
hw-module pvdm 0/0
!
!
!
username cisco privilege 0 password 7 0614002E585C061611
!
redundancy
!
!
!
!
!
pseudowire-class TOM_2_REMOTERTR
encapsulation l2tpv3
protocol l2tpv3 TOM_2_REMOTERTR2_PW
ip local interface GigabitEthernet0/0
!
!
!
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key firewallcx address 192.168.168.236
crypto isakmp key firewallcx address 192.168.168.237
crypto isakmp key firewallcx address 192.168.168.232
!
!
crypto ipsec transform-set TS esp-3des esp-md5-hmac
mode tunnel
!
!
!
crypto map CMAP 72 ipsec-isakmp
set peer 192.168.168.232
set transform-set TS
match address VPN_TRAFFIC_172
crypto map CMAP 76 ipsec-isakmp
set peer 192.168.168.236
set transform-set TS
match address VPN_TRAFFIC_176
crypto map CMAP 77 ipsec-isakmp
set peer 192.168.168.237
set transform-set TS
match address VPN_TRAFFIC_177
!
!
!
!
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
service-module enable
!
interface GigabitEthernet0/0
description OUTSIDE
ip address 192.168.168.235 255.255.255.0
ip nat enable
ip virtual-reassembly in
duplex auto
speed auto
crypto map CMAP
!
interface GigabitEthernet0/1
description INSIDE
no ip address
ip nat enable
ip virtual-reassembly in
duplex auto
speed auto
!
interface GigabitEthernet0/1.77
description L2_to_RTR2
encapsulation dot1Q 77
xconnect 192.168.168.237 1001 encapsulation l2tpv3 pw-class TOM_2_REMOTERTR
!
interface GigabitEthernet0/1.172
description INSIDE_172
encapsulation dot1Q 172
ip address 192.168.172.1 255.255.255.0
ip nat enable
!
interface GigabitEthernet0/1.174
description INSIDE_174
encapsulation dot1Q 174
ip address 192.168.174.1 255.255.255.0
ip nat enable
ip virtual-reassembly in
!
interface GigabitEthernet0/1.175
description INSIDE_175
encapsulation dot1Q 175
ip address 192.168.175.1 255.255.255.0
ip nat enable
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
!
interface GigabitEthernet0/0/0
description MNGT_10_10_10_15
switchport access vlan 200
no ip address
!
interface GigabitEthernet0/0/1
no ip address
!
interface GigabitEthernet0/0/2
no ip address
!
interface GigabitEthernet0/0/3
description TEST_DELETE
switchport access vlan 77
no ip address
!
interface Vlan1
no ip address
!
interface Vlan200
ip address 10.10.10.15 255.255.255.224
!
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip ftp username ahuffman
ip ftp password 7 091D1C180E040408134D241B1C051B090D
ip nat source list 175 interface GigabitEthernet0/0 overload
ip nat source static tcp 192.168.174.66 80 192.168.168.235 888 extendable
ip nat source static tcp 192.168.175.66 80 192.168.168.235 8080 extendable
ip route 0.0.0.0 0.0.0.0 GigabitEthernet0/0 192.168.168.1
ip route 10.10.77.0 255.255.255.0 192.168.168.237
ip route 192.168.176.0 255.255.255.0 192.168.168.236
ip route 192.168.177.0 255.255.255.0 192.168.168.237
!
ip access-list extended ACLMAP8080
permit tcp host 192.168.175.66 192.168.177.0 0.0.0.255 log
permit ip any any log
ip access-list extended ANY_ANY
permit tcp any any eq www
permit tcp any any
permit icmp any any
permit ip any any
ip access-list extended NAT
permit tcp host 192.168.175.66 eq www any
ip access-list extended REMOTE_OUTSIDE_IN_ACL
permit tcp host 192.168.168.140 host 192.168.168.235 eq 8080
deny tcp any host 192.168.168.235 eq 8080
deny udp any host 192.168.168.235 eq 8080
permit ip any any
ip access-list extended TEMP
permit tcp 192.168.177.0 0.0.0.255 host 192.168.175.66 eq www log
ip access-list extended VPN_TRAFFIC_172
permit tcp 192.168.175.0 0.0.0.255 192.168.172.0 0.0.0.255
permit ip 192.168.175.0 0.0.0.255 192.168.172.0 0.0.0.255
ip access-list extended VPN_TRAFFIC_176
permit tcp 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255
permit ip 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255
ip access-list extended VPN_TRAFFIC_177
permit tcp 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
permit ip 192.168.175.0 0.0.0.255 192.168.177.0 0.0.0.255
!
ipv6 ioam timestamp
!
route-map NONAT permit 10
match ip address 177
!
!
access-list 127 permit ip 0.0.0.0 255.255.255.0 any
access-list 175 deny ip 192.168.175.0 0.0.0.255 192.168.176.0 0.0.0.255
access-list 175 permit ip 192.168.175.0 0.0.0.255 any
access-list 177 deny ip host 192.168.175.4 192.167.177.0 0.0.0.255
access-list 177 permit ip host 192.168.175.4 any
!
control-plane
!
!
!
!
!
!
mgcp behavior rsip-range tgcp-only
mgcp behavior comedia-role none
mgcp behavior comedia-check-media-src disable
mgcp behavior comedia-sdp-force disable
!
mgcp profile default
!
!
!
!
!
!
!
gatekeeper
shutdown
!
!
telephony-service
max-conferences 8 gain -6
transfer-system full-consult
!
!
vstack
!
line con 0
line aux 0
line 2
no activation-character
no exec
transport preferred none
transport input all
transport output lat pad telnet rlogin lapb-ta mop udptn v120 ssh
stopbits 1
line vty 0 4
login local
transport input ssh
!
scheduler allocate 20000 1000
ntp server 192.168.168.200
ntp server 10.10.10.30
!
end
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
remotertr175#
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 01:05 PM
Why doesn't my 2921 accept this syntax?
ip nat source static tcp 192.168.175.66 80 192.168.168.235 8080 route-map nonat
The only route-map that it will accept is # ip nat inside source route-map
All the examples that I see on the Internet are the syntax that you suggest?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-22-2019 03:59 PM - edited 03-22-2019 04:03 PM
Hi,
I am sorry for the typo I made, the correct syntax for my suggestion is:
"ip nat inside source static tcp 192.168.175.66 80 192.168.168.235 8080 route-map NONAT"
Best regards,
Antonin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2019 11:40 AM
Be sure to let me know when you come to DC :=)
- « Previous
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide